
Challenge 0: Install local tools and Azure prerequisites
Description
In this challenge, you’ll do the following:
- Create Azure resources required.
- Resource provisioning can take up to 25 minutes, depending on the region used. Once you launch the script to create the Azure resources, review the application architecture & description with your coach.
- Review TrafficControl application architecture.
Your coach will provide you with a Resources.zip package file that contains the starting projects for this hack. It contains a version of the services that use plain HTTP communication and store state in memory. With each challenge, you’ll add a Dapr building block to enhance the application architecture.
Install local prerequisites
Your coach will have indicated which tools you need to install locally.
- Git (download)
- .NET 6 SDK (download)
- Visual Studio Code (download) with the following extensions installed:
- Docker for desktop (download)
- Dapr CLI and Dapr runtime (instructions)
- Install Azure CLI
- Linux (instructions)
- macOS (instructions)
- Windows (instructions)
- Install Bicep extension for VS Code (instructions)
- If you’re running Windows, you’ll need to install a bash shell to run some of the commands. Install either the Git Bash client or the Windows Subsystem for Linux 2.
- Helm (instructions)
Make sure the following minimum software versions are installed by executing the commands in the following table:
| Software | Version | Command Line |
|---|---|---|
| Dapr runtime version | v1.8.4 | dapr --version |
| Dapr CLI version | v1.2.0 | dapr --version |
| DotNet version | 6.0.0 | dotnet --version |
| azure-cli | 2.42.0 | az --version |
Deployment
This hack’s setup files will create the following resources in your Azure Resource Group. Make sure you can create the following:
- Application Insights
- Azure Cache for Redis
- Azure Container Registry
- Azure Kubernetes Service (or Azure Container Apps)
- Event Hub Namespace
- IoT Hub
- Key Vault
- Log Analytics Workspace
- Logic App (with the Office 365 activity for sending email)
- Storage Account
- Service Bus Namespace
If you can’t instantiate some of these resources, you won’t be able to complete the part of the challenge that uses them, but you may still be able to complete the other challenges
Deployment
- AKS requires the ability to create a public IP address. This may be blocked by some organizations. You will either need to get an exception or have an admin create the AKS cluster for you.
- The
Resources\Infrastructure\bicep\aks.bicepfile specifies the default values for the cluster that will work for this hack. Customize as needed.- 1 Agent Pool with 3 Linux VMs using the Standard_DS2_v2 SKU.
- 3 services using a total of
300mof CPU &300Miof memory by default, limited to a total of3000mof CPU &600Miof memory. - 1 Zipkin service running to monitor communication between the services.
- WARNING: For simplicity, a Kubernetes secret is used to allow AKS to pull images from the Azure Container Registry via the admin account. This is not a best practice. In a production example, you should use a managed identity & RBAC.
IMPORTANT: You will need to register the AKS Workload Identity extension feature flags in your Azure subscription. Follow the instructions at the links provided below.
- Install the AKS Preview Azure CLI Extension
- Register the
enableworkloadidentitypreviewfeature flag - Register the
enabledoidcissuepreviewfeature flag
Deployment
To start, you’ll need access to an Azure Subscription & Resource Group:
- If you don’t have one, Sign Up for an Azure account.
- You will need the following subscription resource providers registered.
Microsoft.AppMicrosoft.CacheMicrosoft.ContainerServiceMicrosoft.ContainerRegistryMicrosoft.DevicesMicrosoft.EventHubMicrosoft.InsightsMicrosoft.KeyVaultMicrosoft.KubernetesConfigurationMicrosoft.LogicMicrosoft.OperationalInsightsMicrosoft.OperationsManagementMicrosoft.ServiceBusMicrosoft.StorageMicrosoft.Web
- You will need the following subscription resource providers registered.
- If you already have an Azure account, make sure you have at least Owner access instructions) for the resource group in which you’ll provision Azure resources.
Your IT organization may provide you access to an Azure resource group, but not the entire subscription. If that’s the case, take note of that resource group name and make sure you have Owner access to it, using the instructions mentioned above.
Next, you’ll create the Azure resources for the subsequent challenges using Azure Bicep and the Azure CLI.
-
Login to Azure Portal and create a Resource Group. Create the Resource Group in an Azure region that can support AKS version 1.26.0 & a VM size of
Standard_B4ms(such as South Central US or Central US). -
If you’re using Azure Cloud Shell, skip this step and proceed to step 2. Open the terminal window in VS Code and make sure you’re logged in to Azure
az login -
Optional: Make sure you have selected the Azure subscription in which you want to work. Replace the ‘x’s with your subscription GUID or subscription name. The subscription GUID can be found in the Azure Resource Group blade from the Azure Portal.
az account set --subscription "xxxx-xxxx-xxxx-xxxx" -
Install the
aks-previewextension.az extension add --name aks-previewNote: If you have previously installed the
aks-previewextension, please update it.az extension update --name aks-preview -
Install the
k8s-extension.az extension add --name k8s-extensionNote: If you have previously installed the
k8s-extension, please update it.az extension update --name k8s-extension -
Enable the
Workload Identity Previewfeature.Register the feature:
az feature register --namespace "Microsoft.ContainerService" --name "EnableWorkloadIdentityPreview"Wait a few minutes and verify its registered.
az feature show --namespace "Microsoft.ContainerService" --name "EnableWorkloadIdentityPreview"Refresh the registration.
az provider register --namespace Microsoft.ContainerService -
Enabled the
AKS Extension Managerfeature.az feature register --namespace "Microsoft.ContainerService" --name "AKS-ExtensionManager"Wait a few minutes and verify its registered.
az feature show --namespace "Microsoft.ContainerService" --name "AKS-ExtensionManager"Refresh the registration.
az provider register --namespace Microsoft.ContainerService -
Enable the
DaprFeature.az feature register --namespace "Microsoft.ContainerService" --name "AKS-Dapr"Wait a few minutes and verify its registered.
az feature show --namespace "Microsoft.ContainerService" --name "AKS-Dapr"Refresh the registrations.
az provider register --namespace Microsoft.ContainerService az provider register --namespace Microsoft.KubernetesConfiguration -
Optional: The following steps assume you already have a resource group created. If not, run the following command to create one. Replace the resource group name and location with your own values.
az group create --name <resource-group-name> --location <location> -
Optional: You can run the following PowerShell script to evaluate if you have installed all the prerequisites.
./Resources/Infrastructure/setup.ps1 -
In the accompanying source code, modify the
Resources/Infrastructure/bicep/env/main.parameters.jsonfile so it is unique to you (each person will get their own copy of each Azure resource). You can modify the app name, region & environment as you see fit. These will be concatenated together to generate the names of the Azure resources. Try to keep the name short, as certain Azure resources (like Key Vault) have name limits.```json { "appName": { "value": "dapr<your-initials><3-random-numbers>" }, "region": { "value": "ussc" }, "environment": { "value": "dev" } } ``` -
You’ll now create the required Azure resources inside your resource group with the following Azure CLI command (replace the resource group name).
**If you are going to deploy to Azure Kubernetes Service (AKS).** ```shell cd Resources/Infrastructure/bicep az deployment group create --resource-group <resource-group-name> --template-file ./main.bicep --parameters ./env/main.parameters.json --query "properties.outputs" --output yamlc ``` **If you are going to deploy to Azure Container Apps (ACA) service.** ```shell az deployment group create --resource-group <resource-group-name> --template-file ./main.bicep --parameters ./env/main.parameters.json --query "properties.outputs" --output yamlc --parameters shouldDeployToContainerApps=true ``` _Creating the resources can take some time (>20 minutes). You're encouraged to jump to review the [TrafficControl app architecture](/WhatTheHack/047-TrafficControlWithDapr/Student/Resources/) while the command executes._ Upon completion, the command will output information about the newly-created Azure resources: ```yaml aksFQDN: type: String value: dapr-mce123-609718f5.hcp.southcentralus.azmk8s.io aksName: type: String value: aks-dapr-mce123 aksazurePortalFQDN: type: String value: dapr-mce123-609718f5.portal.hcp.southcentralus.azmk8s.io containerRegistryLoginServerName: type: String value: crdaprmce123.azurecr.io containerRegistryName: type: String value: crdaprmce123 eventHubEntryCamName: type: String value: ehn-dapr-mce123-trafficcontrol/entrycam eventHubExitCamName: type: String value: ehn-dapr-mce123-trafficcontrol/exitcam eventHubNamespaceHostName: type: String value: https://ehn-dapr-mce123-trafficcontrol.servicebus.windows.net:443/ eventHubNamespaceName: type: String value: ehn-dapr-mce123-trafficcontrol iotHubName: type: String value: iothub-dapr-mce123 keyVaultName: type: String value: kv-dapr-mce123 logicAppAccessEndpoint: type: String value: https://prod-29.southcentralus.logic.azure.com:443/workflows/9bd179c8dd7049b8a152e5f2608f8efc logicAppName: type: String value: logic-smtp-dapr-mce123 redisCacheName: type: String value: redis-dapr-mce123 serviceBusEndpoint: type: String value: https://sb-dapr-mce123.servicebus.windows.net:443/ serviceBusName: type: String value: sb-dapr-mce123 storageAccountContainerName: type: String value: trafficcontrol storageAccountKey: type: String value: **_REMOVED_** storageAccountName: type: String value: sadaprmce123 ``` Copy these values into a text editor. You'll need them to configure your Dapr services. -
Assign permissions to KeyVault
Assign yourself access to the KeyVault so you can create secrets:
az keyvault set-policy --resource-group "<resource-group-name>" --name "<key-vault-name>" --upn "dwight.k.schrute@dunder-mifflin.com" --secret-permissions get list set delete --certificate-permissions get list create delete update -
Run the following command to initialize your local Dapr environment:
dapr init
Additional instructions for Azure Kubernetes Service (AKS), skip these if using Azure Container Apps (ACA)
-
Run the following command to fetch the AKS credentials for your cluster.
az aks get-credentials --name <aks-name> --resource-group <resource-group-name>The
az aks get-credentialscommand retrieves credentials for an AKS cluster. It merges the credentials into your local kubeconfig file. -
Verify your “target” cluster is set correctly.
kubectl config get-contextsMake sure that you see a listing for
aks-dapr-<your value>and that it has a star next to it as shown below:CURRENT NAME CLUSTER AUTHINFO NAMESPACE * aks-dapr-<your value> aks-dapr-<your value> clusterUser_rg-dapr-<your value>_aks-dapr-<your value> default -
Create the
dapr-trafficcontrolKubernetes namespaceYou will need to create a namespace to own all of the TrafficControl Kubernetes objects.
kubectl create namespace dapr-trafficcontrol -
Change your local
kubectlcontext to thedapr-trafficcontrolnamespace so all resources are created in that namespace.kubectl config set-context --current --namespace=dapr-trafficcontrol -
Assign permissions to Key Vault
Assign yourself access to the Key Vault so you can create secrets:
az ad signed-in-user show --query userPrincipalName -o tsv az keyvault set-policy --resource-group <resource-group-name> --name <key-vault-name> --upn "dwight.k.schrute@dunder-mifflin.com" --secret-permissions get list set delete -
Update the AKS cluster with the OIDC issuer & Workload Identity feature flags.
az aks update -g "<resource-group-name>" -n "<cluster-name>" --enable-oidc-issuer --enable-workload-identity -
Install the Dapr extension in your AKS cluster.
az k8s-extension create --cluster-type managedClusters --cluster-name <aks-name> --resource-group <resource-group-name> --name dapr --extension-type Microsoft.Dapr -
Shut down your AKS cluster to save money until we need it for Assignment 8
az aks stop --name <aks-name> --resource-group <resource-group-name>
Review TrafficControl application architecture
Spend some time with your teammates reviewing the TrafficControl application architecture & services.
The TrafficControl application architecture consists of four microservices:
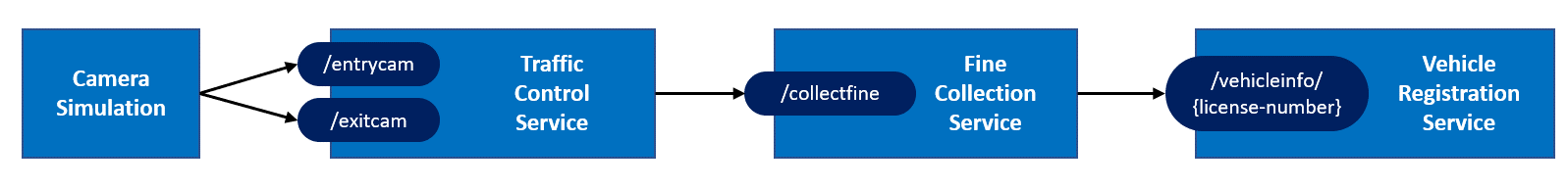
- The Camera Simulation is a .NET Core console application that will simulate passing cars.
- The Traffic Control Service is an ASP.NET Core WebAPI application that offers entry and exit endpoints:
/entrycamand/exitcam. - The Fine Collection Service is an ASP.NET Core WebAPI application that offers 1 endpoint:
/collectfinefor collecting fines. - The Vehicle Registration Service is an ASP.NET Core WebAPI application that offers 1 endpoint:
/getvehicleinfo/{license-number}for retrieving vehicle and owner information of a vehicle.
These services compose together to simulate a traffic control scenario.
TrafficControl Application & Services Description
Success Criteria
- Verify all local prerequisite tools are installed locally.
- Verify all Azure resources have been successfully created.
- Verify your understanding of the TrafficControl application architecture with your coach.