
Challenge 04 - Securing Backends APIs
Pre-requisites
- You should have completed Challenge 03
Introduction
You would like to be able to secure your backend APIs in one of the two ways:
- Secure Hello API in a private network
- Test end-to-end authorization to Hello API via OAuth.
Description
Scenario 01: Configure secured backend APIs in a private network
- Create a new Function App in Elastic Premium plan which will be imported to APIM as Hello Internal API.
- The existing API - Hello API - will now become the public/external API. The new path should be configured in APIM as:
https://apim-.azure-api.net/external/hello - Secure internal Hello Function App by enabling networking feature by either:
- Only accepts traffic coming from the APIM subnet
- Assigning a private endpoint to the Function App
- Import the new Function App as Hello Internal API to APIM. The new path should be:
https://apim-.azure-api.net/internal/hello - Secure external Hello API so that it would only accept requests routed from Application Gateway, which includes setting-up an APIM policy.
- To allow routes to external Hello API only, you should configure URL redirection mechanism in Application Gateway so that:
- All calls to the AGW endpoint with the path /external/* (
http://pip-.australiaeast.cloudapp.azure.com/external) would go tohttps://api..azure-api.net/external/hello - While calls to the default path
http://pip-.australiaeast.cloudapp.azure.com/returns HTTP 404.
- All calls to the AGW endpoint with the path /external/* (
Scenario 02: Configure OAuth2 authorization when calling Hello API
- Configure OAuth 2.0 authorization in APIM
- Register a client application (e.g. APIM Developer Portal or Postman) in Azure AD. This will be used to make calls to Hello API via APIM.
- Configure JWT validation policy to pre-authorize requests to Hello API.
- Register Hello API Function app as an AD application.
- Call Hello API from your client application successfully.
Success Criteria
Scenario 01:
- Verify that you can send GET and POST requests to the public endpoint (
https://apim-.azure-api.net/external/hello) and get a HTTP 200 response. - Verify that you can send GET and POST requests to the internal endpoint (
https://apim-.azure-api.net/internal/hello) over the private network (e.g. from a jumpbox VM) and get HTTP 200 response.
Scenario 02:
- Verify that you are able to get an access token via the OAuth 2.0 authorization code flow.
- Verify that you are able to send GET and POST requests to Hello API (passing the access token into the Authorization header) via the public endpoint and get a HTTP 200 response.
Learning Resources
Scenario 01:
- Azure Functions networking options
- API Management access restriction policies
- Rewrite URL with Azure Application Gateway - Azure portal
- Protect APIs with Application Gateway and API Management
Scenario 02:
- Protect a web API backend in Azure API Management using OAuth 2.0 authorization with Azure Active Directory
- Protect API’s using OAuth 2.0 in APIM
- Configure your App Service or Azure Functions app to use Azure AD login
- Calling an Azure AD secured API with Postman
- Postman - Authorizing requests
Advanced Challenges
Scenario 02:
- You can try to do end-to-end AAD authentication by either:
- Configuring your Function App to use AAD login. Use the existing backend app AAD registration created earlier.
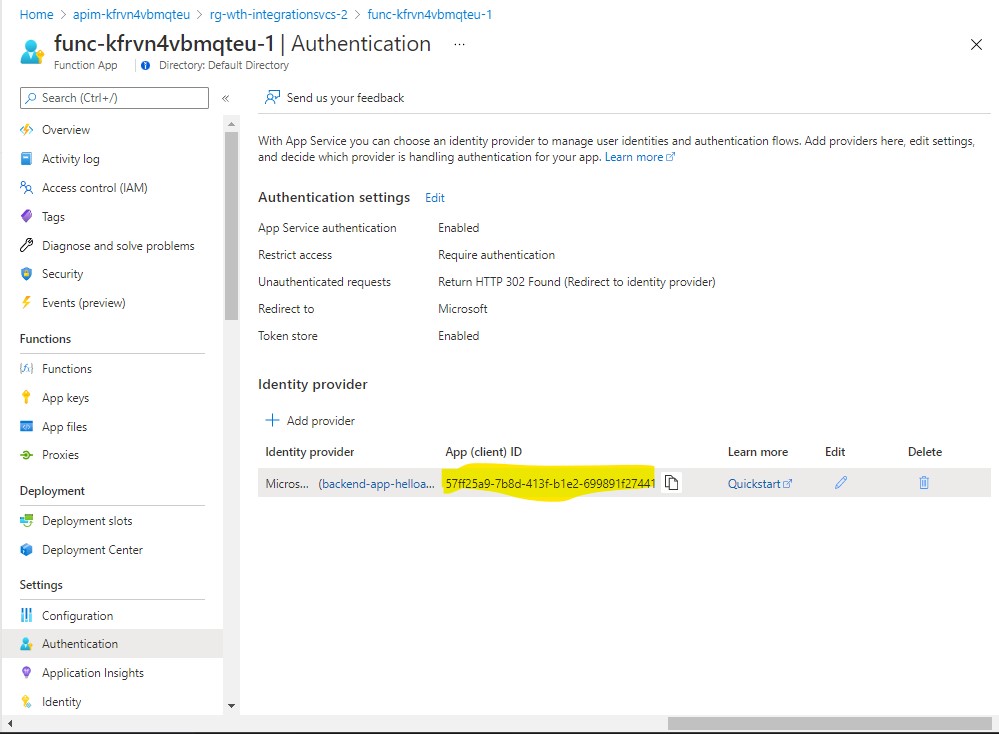
For the issuer URL, usually this would be the AAD Tenant where you created the backend app registration. However, to be sure, I suggest that you check the issuer claim of the Access Token by decoding it using jwt.io.
- Enable Managed Identities in APIM and then authenticate to backend using that identity using authentication-managed-identity policy.
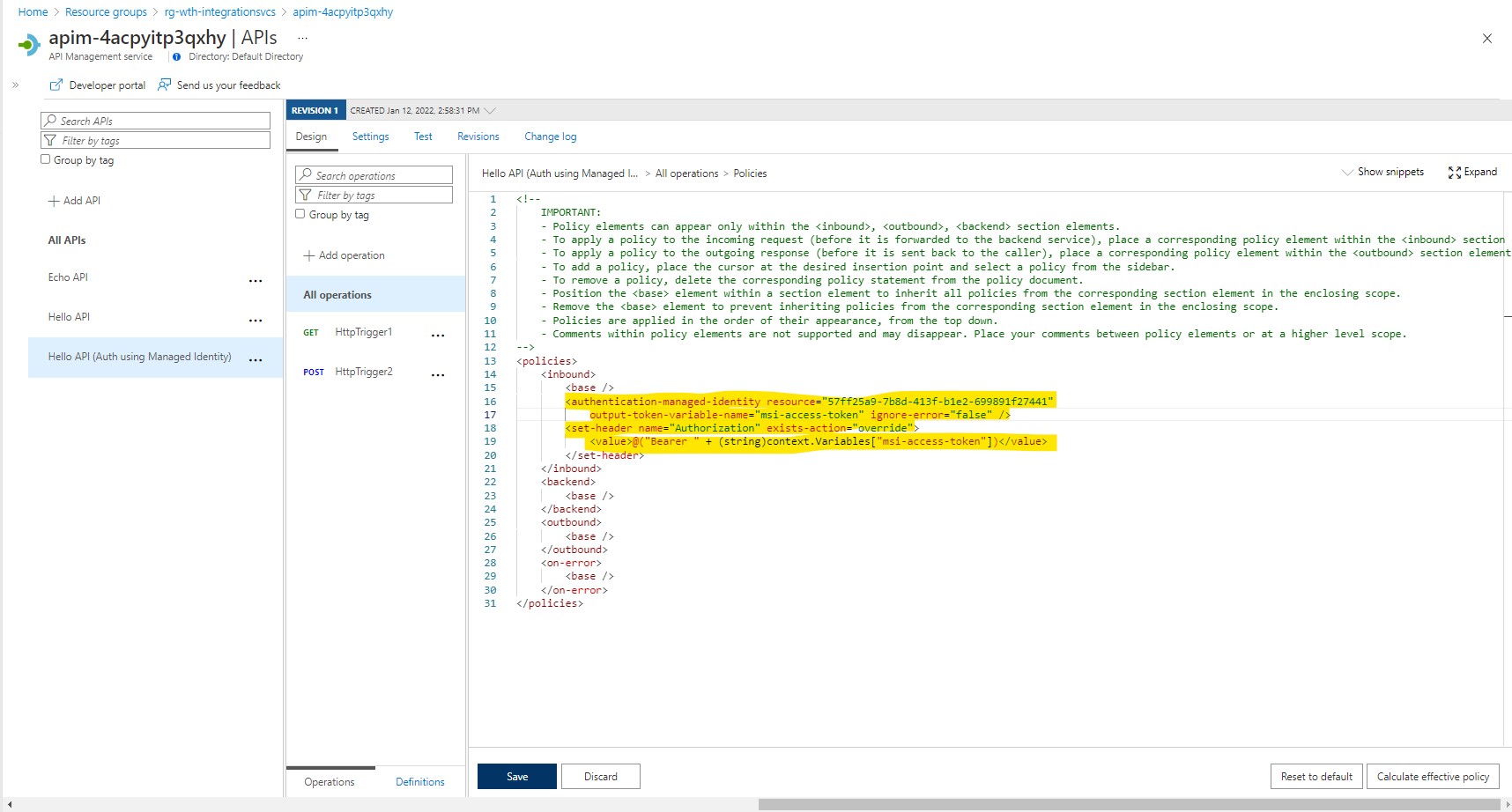
- Configuring your Function App to use AAD login. Use the existing backend app AAD registration created earlier.