Exercise 7: Ingress
In this exercise, you will configure an Ingress resource to expose your application using a single external IP address. Ingress allows you to manage external access to services in your cluster, typically HTTP.
Task 1 - Identify the Ingress Controller’s Public IP
The Nginx Ingress Controller has already been deployed as part of the AKS cluster deployment. Get the public IP address assigned to the Nginx ingress controller:
kubectl get service -n app-routing-systemkubectl get service -n app-routing-systemLook for a service named
nginxor similar. The EXTERNAL-IP column shows the IP you will use to access your app.
Task 2 - Create an Ingress Resource
Create an Ingress manifest that routes HTTP traffic to your existing service (
sample-svc) on port 80 when requests are sent to thehttp://lab.kubernetes.demoURL:$sampleIngressYaml = @" apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: sample-ingress annotations: nginx.ingress.kubernetes.io/ssl-redirect: "false" nginx.ingress.kubernetes.io/rewrite-target: / spec: ingressClassName: webapprouting.kubernetes.azure.com rules: - host: lab.kubernetes.demo http: paths: - path: / pathType: Prefix backend: service: name: sample-svc port: number: 80 "@ # Apply the Ingress manifest $sampleIngressYaml | kubectl apply -f -cat << EOF | kubectl apply -f - apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: sample-ingress annotations: nginx.ingress.kubernetes.io/ssl-redirect: "false" nginx.ingress.kubernetes.io/rewrite-target: / spec: ingressClassName: webapprouting.kubernetes.azure.com rules: - host: lab.kubernetes.demo http: paths: - path: / pathType: Prefix backend: service: name: sample-svc port: number: 80 EOFCheck that the Ingress resource is created:
kubectl get ingresskubectl get ingressThe ADDRESS column should eventually show the same public IP as the Ingress controller, as well as the URL.
Task 3 - Test Access via Ingress
Important
At this point, if you were doing this for real, you would need to configure your DNS to point lab.kubernetes.demo to the Ingress controller’s public IP address. You would also want to setup an SSL certificate for secure access.
For the purposes of this lab, we will test Ingress by calling the Ingress controller from the command line, with a host header set to lab.kubernetes.demo.
Use the following command to test access to your service via Ingress:
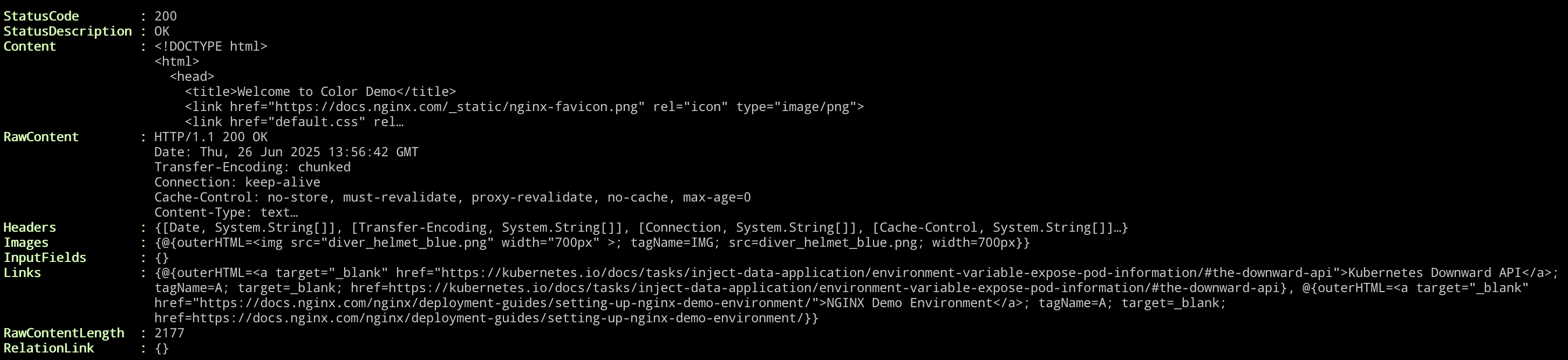
Invoke-WebRequest -Uri "http://<INGRESS_CONTROLLER_IP>" -Headers @{ Host = "lab.kubernetes.demo" }curl -H "Host: lab.kubernetes.demo" http://<INGRESS_CONTROLLER_IP>Replace
<INGRESS_CONTROLLER_IP>with the actual IP address you found in Task 1.If you used Powershell, you should see the response from your service, with a
200 OKcode, indicating that the Ingress is correctly routing traffic to your service.If you used Bash, you will see the raw HTML of the webpage being displayed, and near the top you should see a line like this:
<title>Welcome to Color Demo</title>
Task 4 - Clean Up
Deleting any pod within our current Deployment will simply tell Kubernetes that the Deployment is not in its desired state and it will automatically create a replacement. You can only delete pods that were spawned by a Deployment by deleting the Deployment.
Delete the Deployment.
kubectl delete deployment sample-depkubectl delete deployment sample-depThe Service is independent of the pods it services, so it’s not affected when the Deployment is deleted. Anyone trying to access the service’s address will simply get an error message. If the Deployment is ever re-created, the Service will automatically start sending traffic to the new pods.
Delete the Service. This may take a little while to complete, as Kubernetes will first remove the public IP and then delete the Service.
kubectl delete service sample-svckubectl delete service sample-svcFinally, delete the Ingress:
kubectl delete ingress sample-ingresskubectl delete ingress sample-ingress