Azure Container Registry (ACR)
Azure Container Registry (ACR) is Microsoft’s fully managed container registry service that provides enterprise-grade features for storing, managing, and securing container images and OCI artifacts. Built on the foundation of container registry concepts , ACR offers seamless integration with Azure services, particularly Azure Kubernetes Service (AKS), making it the preferred choice for Azure-based containerized workloads.
ACR Service Tiers
Azure Container Registry offers three service tiers designed to meet different requirements and scale needs:
| Service Tier | Description | Storage | Throughput | Features |
|---|---|---|---|---|
| Basic | Cost-optimized entry point for developers learning Docker and ACR | 10 GiB included | Lower throughput | Manual geo-replication, webhooks |
| Standard | Production-ready with increased storage and throughput | 100 GiB included | Higher throughput | Content trust, private link support |
| Premium | Enterprise-grade with advanced security and global distribution | 500 GiB included | Highest throughput | Geo-replication, content trust, private link, customer-managed keys |
OCI Artifact Support in ACR
ACR fully implements the OCI Distribution Specification, making it a versatile artifact repository beyond just container images. Azure Container Registry natively supports:
- Container Images: Docker and OCI-compliant images with multi-platform support
- Helm Charts: Kubernetes application packages stored as OCI artifacts
- Bicep Modules: Reusable Infrasrtucture as Code Modules
- OPA Bundles: Open Policy Agent policy packages
- Custom Artifacts: Any OCI-compliant artifact type
This broad artifact support enables teams to use ACR as a single source of truth for all their containerized application components, simplifying management and applying consistent security policies.
Integration with Azure Kubernetes Service (AKS)
ACR provides deep integration with AKS, offering streamlined authentication, networking, and performance optimizations specifically designed for Azure environments.
Authentication Integration
AKS clusters can authenticate with ACR using several methods, each suited for different scenarios:
| Authentication Method | Use Case | Configuration | Benefits |
|---|---|---|---|
| AKS Service Principal | Traditional authentication for existing clusters | Assign AcrPull role to service principal | Simple setup, compatible with older AKS versions |
| Managed Identity | Modern, secure authentication for new clusters | Enable managed identity during cluster creation | No credential management, enhanced security |
| Azure AD Workload Identity | Pod-level authentication with fine-grained access | Configure workload identity federation | Granular permissions, zero standing credentials |
| Admin User | Development and testing scenarios only | Enable admin user in ACR settings | Quick setup, not recommended for production |
Network Integration
ACR supports multiple networking configurations to meet security and performance requirements:
- Public Access: Default configuration allowing internet access with optional IP restrictions
- Private Endpoints: Secure connectivity through Azure Private Link for isolated network access
- Virtual Network Integration: Direct integration with AKS virtual networks for optimized performance
- Firewall Rules: Network-level access controls to restrict registry access by IP ranges
Performance Optimizations
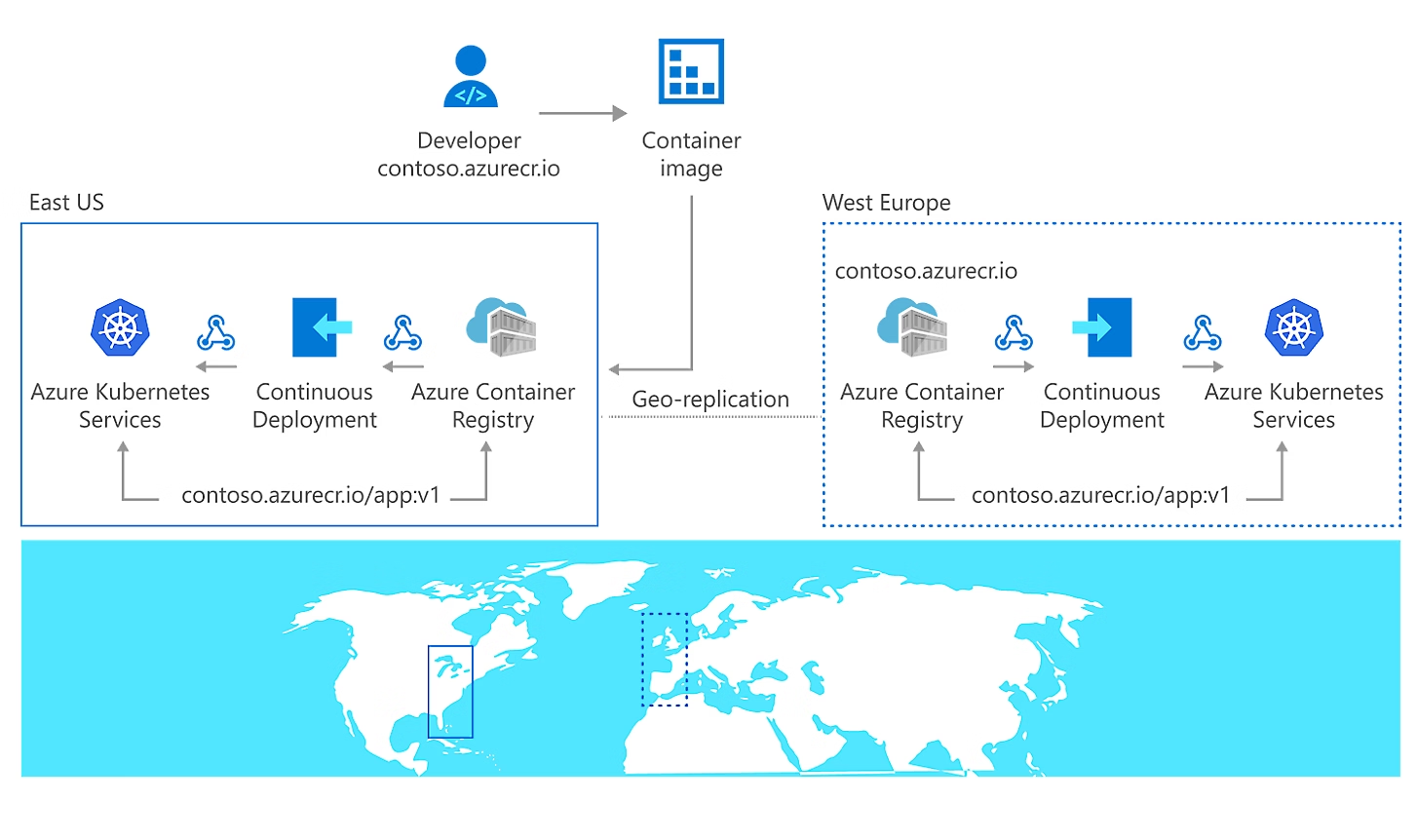
The proximity between ACR and AKS within Azure regions provides significant performance benefits:
- Regional Proximity: Reduced latency for image pulls within the same Azure region
- Azure Backbone: High-speed connectivity through Microsoft’s global network infrastructure
- Geo-replication: Premium tier feature enabling image replication across multiple regions
- Content Caching: Efficient layer caching reduces bandwidth and improves pull performance
Security Features
ACR implements comprehensive security controls designed for enterprise environments:
Vulnerability Scanning
- Microsoft Defender for Containers: Integrated vulnerability assessment and threat detection
- Qualys Integration: Third-party vulnerability scanning with detailed reporting
- Policy Enforcement: Prevent deployment of images with high-severity vulnerabilities
Access Control
- Azure RBAC: Fine-grained role-based access control integrated with Azure Active Directory
- Repository-scoped Tokens: Limited-scope access tokens for CI/CD systems
- Anonymouse Access: Open registry for public distribution of images
Encryption and Compliance
- Encryption at Rest: All registry content encrypted using Azure Storage encryption
- Customer-Managed Keys: Premium tier support for customer-controlled encryption keys
- Compliance Certifications: SOC, ISO, and other enterprise compliance standards
Best Practices for ACR with AKS
| Practice | Implementation | Benefit |
|---|---|---|
| Use Managed Identity | Enable managed identity for AKS clusters | Eliminates credential management overhead |
| Implement Geo-replication | Configure replication in regions where AKS clusters operate | Reduces image pull latency and improves reliability |
| Enable Private Endpoints | Use private link for production workloads | Enhances security by eliminating internet exposure |
| Organize with Repositories | Use separate repositories for different applications or teams | Improves organization and enables granular access control |
| Implement Retention Policies | Configure automatic cleanup of old image versions | Controls storage costs and maintains registry hygiene |
| Monitor Registry Metrics | Use Azure Monitor to track pulls, storage, and performance | Identifies optimization opportunities and usage patterns |