Securing Egress Traffic
Securing egress traffic from Azure Kubernetes Service (AKS) clusters is a critical security consideration that involves controlling and monitoring outbound network connections from pods and nodes. This section explores the challenges, solutions, and best practices for implementing comprehensive egress security.
What is Egress Traffic Security?
Egress traffic security refers to the practice of controlling, monitoring, and securing outbound network traffic that originates from within your Kubernetes cluster and travels to external destinations. This includes traffic to:
- External APIs and services
- Third-party SaaS applications
- Package repositories and container registries
- Public cloud services
- On-premises systems
- Internet resources
Egress in AKS
There are several different ways that traffic from AKS that needs to leave the cluster, and local VNet, can be routed.
Warning
Be careful when choosing which outboundType to use for your cluster, as there are limitations on which other types you can migrate to at a later date. This also depends on whether you are using a managed or BYO VNet. Full details of which types can be migrated can be found in the documentation
Load Balancer
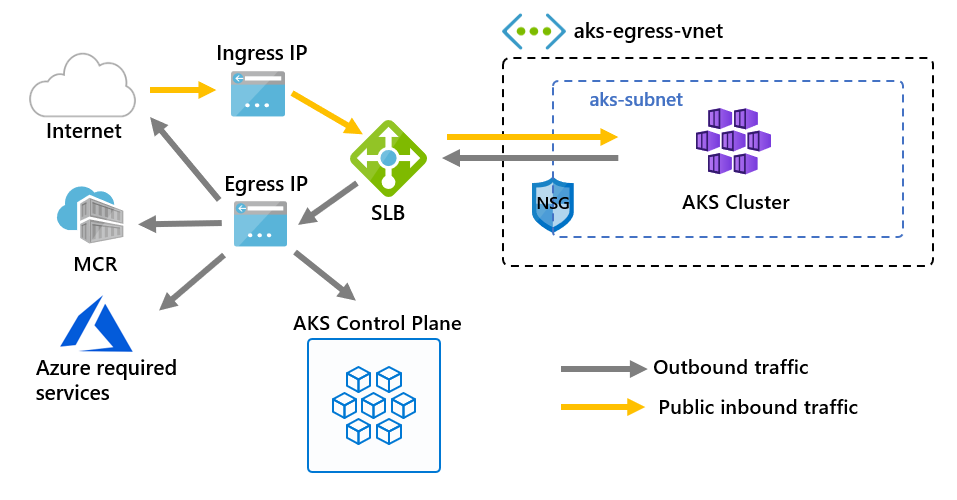
The default approach will be routed through the Azure Load Balancer that was created with your AKS cluster. Traffic will use the public IP address of the Load Balancer to reach external destinations. This is defined as the loadBalancer outbound type in AKS.
Nat Gateway
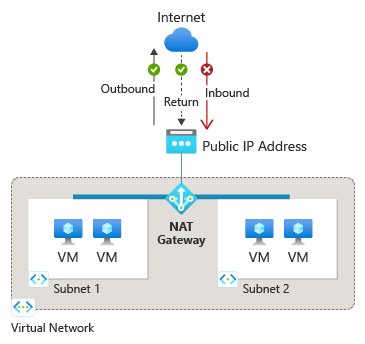
The next method is to route traffic out through a NAT Gateway which provides a managed SNAT service. The type for this can be either managedNatGateway for a NAT Gateway that has been created and managed by AKS, or userManagedNatGateway for a NAT Gateway that has been created separately.
User Defined Routes (UDR)
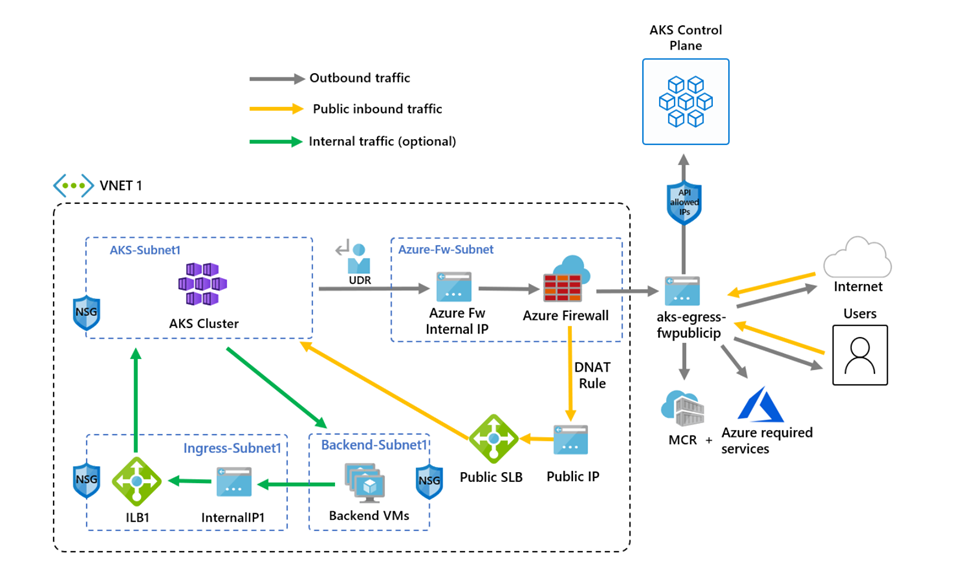
User Defined Routes allow you to define custom routing rules for outbound traffic. This can be used to direct traffic through specific appliances or firewalls, or to control the path that traffic takes to reach external destinations. The most common use case for this is to route traffic out through an Azure Firewall, which can provide advanced filtering and monitoring capabilities. This is defined as the userDefinedRouting outbound type in AKS.
None and Block
If you deploy AKS using a special Network Isolated
configuration, you have two additional options for outbound traffic, none and block.
- None: No outbound connectivity is configured for the cluster. If you require outbound connectivity, you must configure it using a NAT Gateway or User Defined Routes.
- Block: Outbound connectivity is blocked and you must explicitly allow traffic to specific destinations
On the surface these two options may seem similar, but they have different implications for how you manage egress traffic:
- With
none, you are responsible for ensuring that no unintended egress occurs. If a route or NSG rule is misconfigured, traffic might still escape. - With
block, AKS guarantees that egress is blocked unless you explicitly override it.
Why Secure Egress Traffic?
| Category | Risk/Concern | Examples |
|---|---|---|
| Data Exfiltration Prevention | Sensitive data leaving the cluster, intentional or accidental leaks | |
| Attack Vector Mitigation | External communication enabling attacks or malware | |
| Resource Protection | Abuse of cluster resources and external services | |
| Compliance and Governance | Regulatory and organizational requirements for controlling egress |
Egress Security Challenges in Kubernetes
Securing egress traffic in Kubernetes is challenging due to the dynamic nature of pods, which frequently change IP addresses and scale rapidly. Traditional firewall rules based on static IPs are often ineffective. Microservices architectures further complicate control, as each service may have its own external dependencies. Rapid development cycles and frequent updates introduce new outbound connections, making it difficult for security teams to maintain visibility and control. Effective egress security requires adaptive, granular solutions that can keep pace with these changes.
Egress Security Solutions
Network Policies
As well as controlling east-west traffic between pods, as we discussed in the network policies section , Kubernetes Network Policies can also be used to control egress traffic from pods to external destinations - with some limitations.
Capabilities
| Capability | Description |
|---|---|
| Pod-level Control | Restrict egress traffic from specific pods or namespaces |
| Protocol Filtering | Control traffic based on protocols (TCP, UDP, SCTP) |
| Port-based Rules | Allow or deny traffic to specific ports |
| Namespace Isolation | Prevent cross-namespace communication |
| IP/CIDR Blocks | Control access to specific IP ranges |
Limitations
| Limitation | Description |
|---|---|
| No Application-layer Filtering | Cannot inspect HTTP headers, URLs, or content |
| Limited External Control | Basic IP-based rules for external traffic, unless using advanced policies such as Cilium (DNS rules) |
| No Encryption | Cannot decrypt and inspect encrypted traffic |
| DNS Challenges | Difficult to create rules for services with dynamic IPs |
Extended Network Policies
Extended network policies, such as those provided by Calico or Cilium, can enhance the capabilities of standard Kubernetes Network Policies. They allow for more granular control over egress traffic, including DNS-based rules and application-layer filtering. These extended policies can also provide additional features such as:
| Feature | Description |
|---|---|
| Advanced Network Policies | Extended policy capabilities beyond standard Kubernetes |
| DNS Policies | Control access based on DNS names |
| Egress Gateways | Dedicated egress points with detailed logging |
| Threat Detection | Real-time security monitoring and alerting |
| Compliance Reporting | Automated compliance reporting and auditing |
| Network Observability | Deep network visibility and monitoring |
| Multi-cluster Networking | Secure connectivity across clusters |
AKS can be configured with Calico or Cilium as the network policy provider to take advantage of these extended capabilities. Some of the features, such as DNS-based rules require implementation of AKS Advanced Container Networking which has an additional cost associated with it.
Azure Firewall Integration
Azure Firewall provides advanced egress filtering capabilities when integrated with AKS:
- FQDN Filtering: Block or allow traffic based on fully qualified domain names
- Application Rules: HTTP/HTTPS traffic filtering with URL and header inspection
- Network Rules: Traditional layer 3/4 filtering
- Threat Intelligence: Automatic blocking of known malicious IPs and domains
- Centralized Management: Single point of control for multiple clusters
AKS can be configured to route egress traffic through Azure Firewall by using a User Defined Route (UDR) that directs traffic to the firewall’s private IP address. This allows for centralized control and monitoring of outbound connections. The firewall can be deployed in several different configurations depending on your requirements:
- Hub-and-Spoke: Route cluster traffic through a centralized Azure Firewall
- Dedicated Firewall: Deploy a dedicated firewall instance for each cluster
- Regional Firewalls: Share firewall instances across clusters in the same region
Service Mesh Solutions
Many service meshes offer advanced capabilities for managing and securing egress traffic from Kubernetes clusters using egress gateways. They enable fine-grained control over outbound connections, enforce security policies, provide observability, and support encryption for external communications. Common features include centralized egress gateways, policy-driven access control, traffic monitoring, and integration with external services.
Popular service mesh options for egress management in AKS include:
- Istio
- Linkerd
- Consul
- Cilium Service Mesh
Integration with Azure Services
AKS can be integrated with several Azure security monitoring services to enhance egress security and monitoring:
Azure Monitor Integration
- Network Insights: Deep visibility into network traffic patterns
- Log Analytics: Centralized logging and analysis
- Application Insights: Application-level monitoring and tracing
- Workbooks: Custom dashboards for security monitoring
Azure Security Center
- Security Recommendations: Automated security recommendations
- Threat Detection: Advanced threat detection capabilities
- Compliance Monitoring: Continuous compliance assessment
- Security Alerts: Real-time security alerting
Azure Sentinel
- SIEM Integration: Security information and event management
- Threat Hunting: Proactive threat hunting capabilities
- Incident Response: Automated incident response workflows
- Threat Intelligence: Integration with global threat intelligence