Microsoft Defender for Containers
Microsoft Defender for Containers is a security service that monitors and protects containerized environments across multi-cloud and hybrid infrastructures. As part of the Microsoft Defender for Cloud suite, it provides threat protection, vulnerability management, and security posture management for Kubernetes clusters, container workloads, and container registries.
Overview
Microsoft Defender for Containers addresses security challenges in containerized environments through continuous monitoring, threat detection, and automated response. The service utilizes Microsoft’s threat intelligence network and employs analytics, machine learning, and behavioural analysis to identify attacks targeting containerized workloads.
Core Security Domains
Microsoft Defender for Containers operates across four security domains:
- Security Posture Management
- Vulnerability Assessment and Management
- Runtime Threat Protection
- Deployment and Monitoring
Lets take a look at each one in more detail.
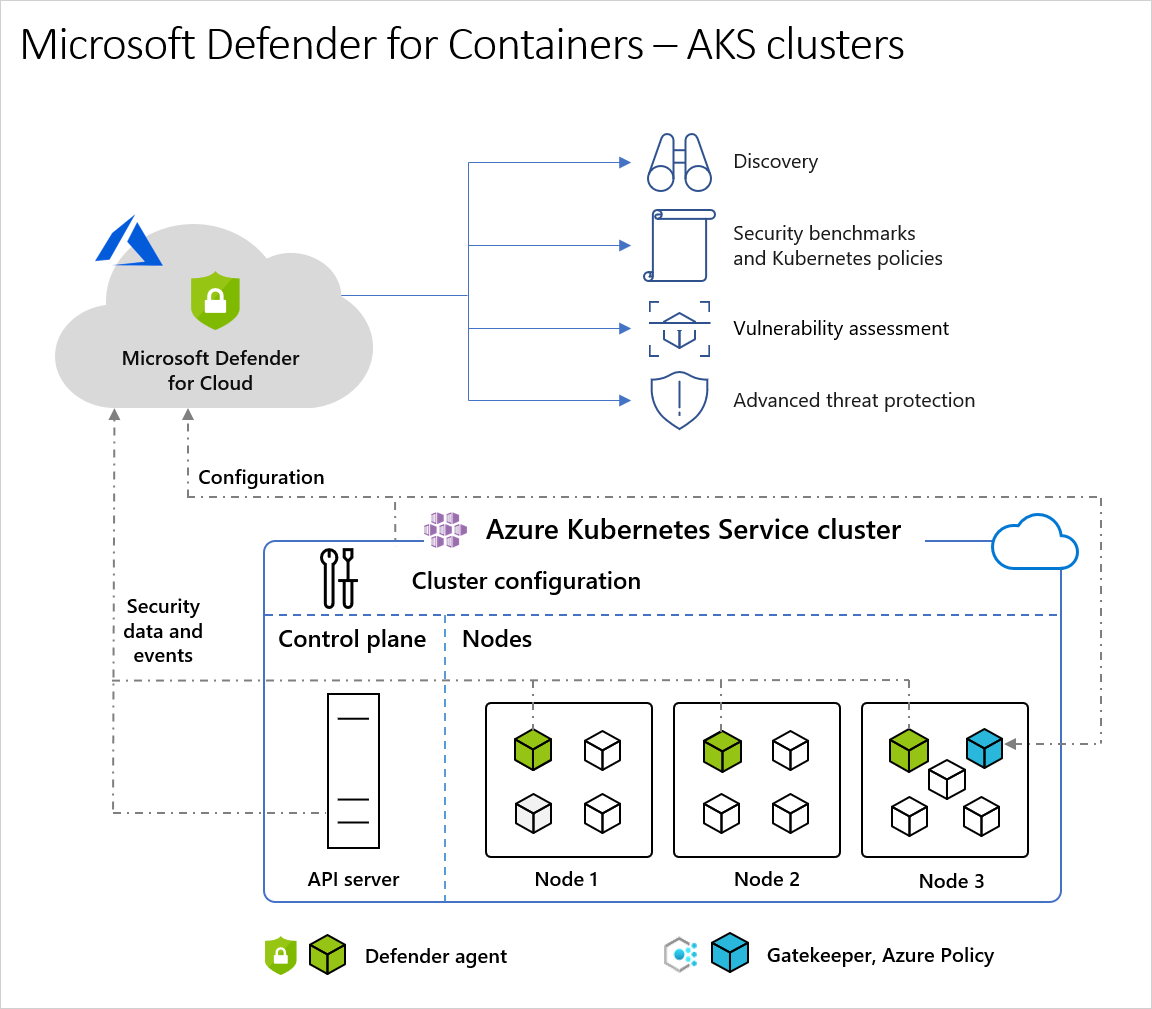
Security Posture Management
Provides visibility into containerized environments through continuous monitoring and agentless discovery. The service maintains an inventory of containerized assets and monitors APIs and configurations to detect misconfigurations. Control plane hardening assesses cluster configurations against security baselines and integrates with Azure Policy for consistent enforcement.
Vulnerability Assessment and Management
Uses both agentless and sensor-based approaches to scan container images, running containers, and Kubernetes nodes. Performs daily scans across multiple registry types and provides runtime vulnerability assessment. Integrates with Microsoft Defender Vulnerability Management for exploitability insights and generates signed vulnerability findings.
Runtime Threat Protection
Provides real-time monitoring using over 60 Kubernetes-aware analytics and anomaly detection capabilities. Threat detection aligns with the MITRE ATT&CK framework and operates across cluster, node, and workload levels.
| Protection Layer | Detection Capabilities | Coverage Areas |
|---|---|---|
| Cluster Level | API server monitoring, RBAC violations, resource manipulation | Control plane activities, administrative actions, policy violations |
| Node Level | Process monitoring, network activity, file system changes | Host-level threats, privilege escalation, lateral movement |
| Workload Level | Container behaviour analysis, application interactions, data access | Application-level attacks, runtime exploitation, data exfiltration |
Deployment and Monitoring
Ensures security components are properly installed and maintained across container infrastructure. Monitors clusters for missing sensors and provides automated deployment. Supports multiple deployment methods including Azure Portal, REST API, ARM templates, and Helm charts.
Threat Detection and Response
The system leverages Microsoft’s threat intelligence network and generates security alerts categorized by severity and mapped to the MITRE ATT&CK framework. Integrates with Microsoft Defender XDR for unified incident response, providing automated containment actions and forensic data collection.
Compliance and Governance
Supports regulatory compliance frameworks through automated assessment capabilities. Integrates with Azure Policy for consistent policy enforcement across container environments, including real-time policy evaluation and automated remediation actions.
Operational Considerations
The service minimizes performance impact through efficient data collection and filtering. Designed to scale across large, distributed environments with support for multi-cloud deployments. Pricing is based on vCPUs in monitored clusters with flexible deployment options for cost optimization.
Architecture and Components
Microsoft Defender for Containers uses a distributed architecture combining cloud-based analytics with cluster-deployed sensors.
Defender Sensor Architecture
The Defender sensor is the primary data collection component deployed within Kubernetes clusters. It operates at the node level using eBPF technology to monitor system calls, network activity, and process behaviour with minimal performance overhead.
| Component | Function | Deployment Method |
|---|---|---|
| Data Collection Engine | Monitors system calls, network traffic, and process activities | eBPF-based kernel integration |
| Event Processor | Analyses collected data and identifies security-relevant events | Local processing with cloud correlation |
| Communication Module | Securely transmits security data to Microsoft Defender for Cloud | Encrypted channels with certificate-based authentication |
The sensor automatically adapts to different Kubernetes distributions including AKS, Azure Arc-enabled Kubernetes, Amazon EKS, Google GKE, and other CNCF-certified distributions.
Sensor Deployment Options
Organizations can deploy the Defender sensor through:
- Automatic provisioning: Sensor automatically installed when service is enabled
- Manual deployment: Selective deployment to specific clusters with custom procedures
- Helm-based deployment: Integration with DevOps pipelines and infrastructure-as-code
Network Requirements
The sensor requires outbound connectivity to Microsoft Defender for Cloud endpoints. Supports environments with restricted network access through Azure Monitor Private Link Scope integration for secure communication.