Task 5.2: Investigate a lateral movement alert
Microsoft Defender for Identity is a tool used to discover and analyze attacks. This is an important feature that will help ensure that your environment is secure. Please take your time when analyzing these attacks to become comfortable with their capabilities.
-
Switch to the DC01 RDP session, in the browser, if you are not already, go to https://security.microsoft.com.
-
Under Incidents & alerts, select Alerts
-
Locate and then select the Suspicious network connection over Encrypting File System Remote Protocol alert to show the details page.
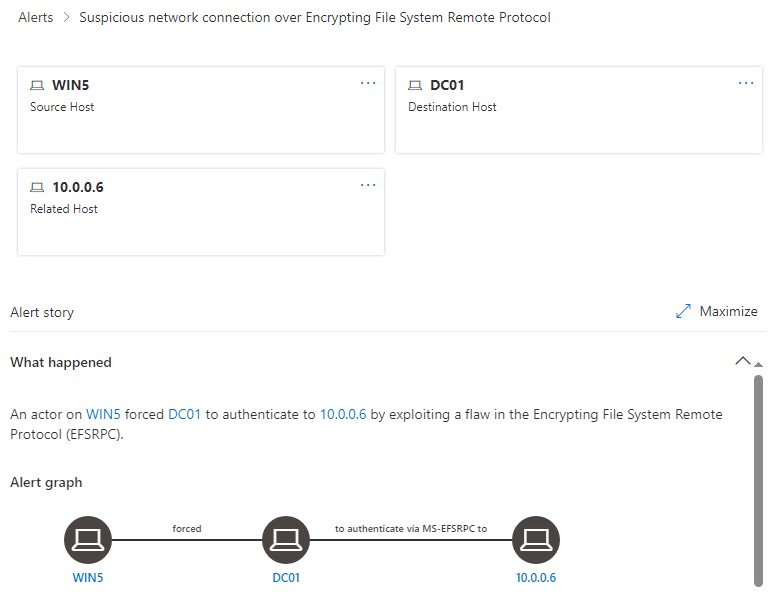
It can take several minutes for the alert to appear. Wait a few minutes, and then refresh the browser. If you don’t see the alert, you can continue to the next section and return to investigate the alert in a few minutes.
-
Review the information regarding the Alert story on the details page.
-
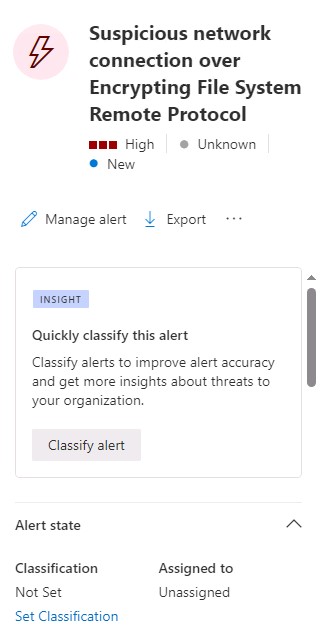
Review the options on the blade on the right side of the details page
-
Under the Incident details, select the Incident link.
-
Review the Incident details page to discover related attacks. This will display additional alerts from the same user or machine.
-
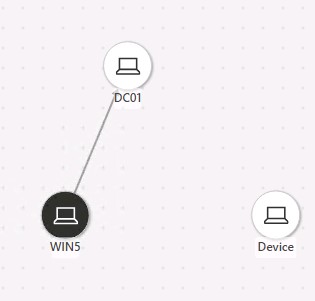
Review the Incident graph.
 )
) -
Select each object in the Incident graph, and then select Device details to display information relating to the object.
-
When finished reviewing the Device details, scroll back to the top, and then select Back to incident details.
-
Select the Alerts tab, and then select Suspicious network connection over Encrypting File System Remote Protocol to return to the alert details page.
-
On the right panel, select Manage alert.
-
On the Manage alert blade, configure the options using the following information:
Heading Value Status In progress Assigned to Assign to me Classification True positive/Malicious user activity Comment This attack requires further investigation. -
Select Save, and then close the Manage alert blade.