AZT301.4 - Virtual Machine Scripting: Compute Gallery Application#
By utilizing Compute Gallery Applications, an attacker can pass MS-DOS or PowerShell commands to the VM as SYSTEM.
Actions
- Microsoft.Compute/virtualMachines/write
- Microsoft.Compute/galleries/write
- Microsoft.Compute/galleries/applications/write
- Microsoft.Compute/galleries/applications/versions/write
Resource
Virtual Machine
Examples
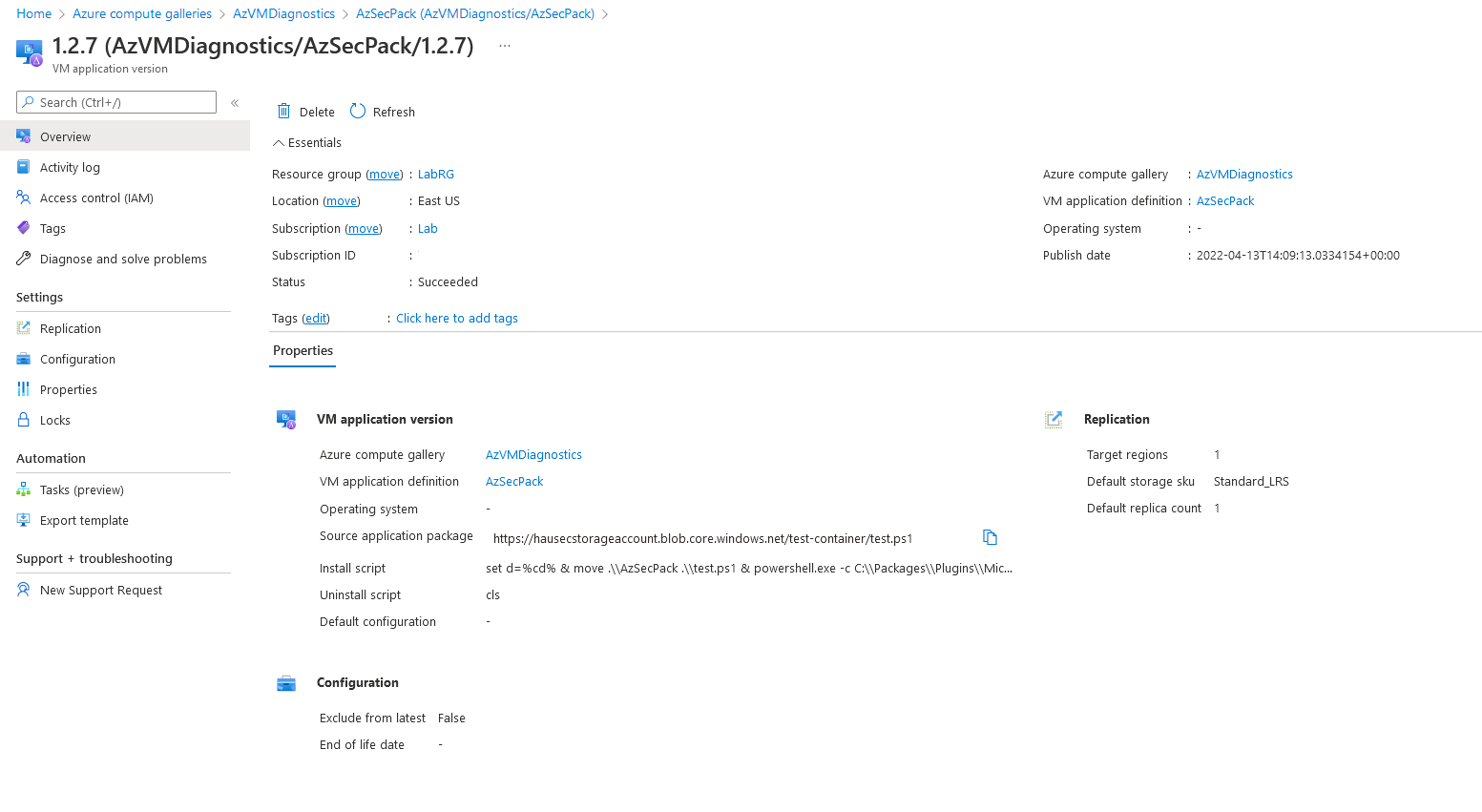
Detections
Logs#
| Data Source | Operation Name | Action/On-Disk Location | Log Provider |
|---|---|---|---|
| Resource | Create or Update Gallery Application Version | Microsoft.Compute/galleries/applications/versions/write | AzureActivity |
| Resource | Create or Update Gallery Application | Microsoft.Compute/galleries/applications/write | AzureActivity |
| Resource | Create or Update Gallery Application Version | Microsoft.Compute/galleries/applications/versions/write | AzureActivity |
| Resource | Create or Update Gallery Application Version | Microsoft.Compute/galleries/applications/versions/write | AzureActivity |
| On-Resource File | File Creation | C:\Packages\Plugins\Microsoft.Powershell.DSC\2.83.2.0\Status | Event |
Queries#
| Platform | Query |
|---|---|
| Log Analytics | AzureActivity | where OperationNameValue == 'MICROSOFT.COMPUTE/GALLERIES/APPLICATIONS/VERSIONS/WRITE' and ActivityStatusValue == 'Created' |
Azure Monitor Alert#
Additional Resources
https://docs.microsoft.com/en-us/azure/virtual-machines/vm-applications