AZT501.3 - Account Manipulation: Azure VM Local Administrator Manipulation#
An adverary may manipulate the local admin account on an Azure VM
Resource
Azure Active Directory
Actions
- microsoft.compute/virtualMachines/extensions/write
Examples
Detections
Detection Details#
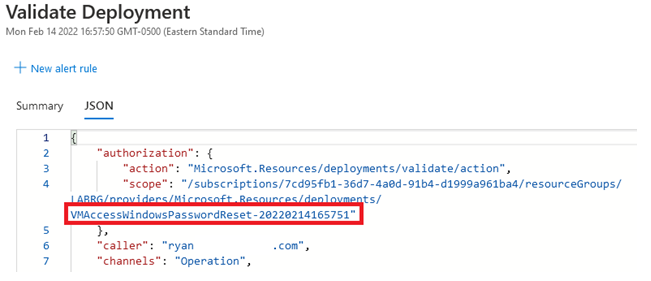
After a successful reset, the log 'Validate Deployment' will be created. Specifically, in the scope, a password reset will be mentioned "VMAccessWindowsPasswordReset".
Logs#
| Data Source | Operation Name | Action | Log Provider |
|---|---|---|---|
| Resource | Create or Udpate Virutal Machine Extension | microsoft.compute/virtualMachines/extensions/write | ActivityLog |
| Resource | Validate Deployment | Microsoft.Resources/deployments/validate/action | ActivityLog |
Detection Screenshot#
Queries#
| Platform | Query |
|---|---|
| Log Analytics | AzureActivity | where Properties_d has 'vmaccesswindowspasswordreset' |
Azure Monitor Alert#
Additional Resources
https://docs.microsoft.com/en-us/troubleshoot/azure/virtual-machines/reset-rdp