Security review
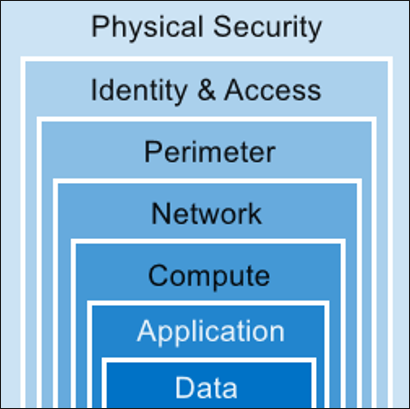
A multi-layered approach to securing your environment will increase the security posture of your environment. Commonly known as defense in depth. You need to review and protect all the layers (from deep to surface):
- Data: avoid data access vulnerabilities
- Application: malicious code injection and other common attacks.
- Infrastructure: malware, credential exposure and lateral movements protection.
- Network: unnecessary open ports, brute-force attacks.
- Perimeter: DoS attacks
- Policies and access: monitoring, use of modern authentication methods.
- Physical: unauthorized access to facilities.
Increasing the security of your workload, may probably increase your Azure bill, but you also need to calculate the huge costs of a security breach. Today, the cost of not applying security mechanisms goes beyond the trust of loss or the cost of repairing the aftermath. Malicius actors are using many techniques to take control of full subscriptions where they will deploy costly resources to serve their needs.
Level 1 - Identity and Encryption
How are authentication and authorization managed for the resources? What protocols are in use? Are you applying MFA? Are you using Managed Identities?
Check if you are using correctly RBAC with the least access principle, and have controls in place to access your Azure resources.
List the encryption requirements at the different application levels.
Level 2 - Networking, Secrets and Tools
Review how the network perimeter is being protected (e.g. use of NSGs, Bastion, end-to-end encryption, etc). Check the use of Firewalls and Gateways.
Verify the proper usage of Keys, Secrets and Certificates. Lifecycle management of keys, and the access policies applied.
List the tools and processes used for monitoring, auditing and detecting vulnerabilities.
Level 3 - Application level security
Many vulnerabilities start in the workload code. Review the Development Lifecycle of the application and ensure that DevSecOps principles are applied, using automated code scanning and vulnerability assessment tools.
Check that the deployments are automated to avoid human errors.
How are users authenticated and authorized to access the application?
Do regular Threat Modelling sessions with the development team. Do shift left.
Resources
Checkpoint
- Most important security risks identified (Threat matrix).
- Effort evaluation for optimizations related to security.
- Trade-offs, costs and potential cost of a security breach.
Now you can move to the next pillar: Reliability