Task 02 - Configure Azure resources
Introduction
Now that you have deployed the necessary Azure resources, the next step is to configure these resources.
Description
In this task, you will configure your Microsoft Foundry project and set up the necessary environment variables for your application.
Success Criteria
- You have configured your Microsoft Foundry project.
- You have set up the necessary environment variables for your application in a .env file.
Learning Resources
- What is Microsoft Foundry?
- Add a new connection to your project
- How to create and configure your storage account for use in Microsoft Foundry Projects
Key Tasks
01: Create Azure AI model deployments
The Microsoft Foundry project that you deployed as part of the first step is now ready to be configured. You will need to set up the project to use the resources that you deployed in the previous step, as well as selecting the model deployments that you will use.
Expand this section to view the solution
Navigate to the Microsoft Foundry and select the project that you created in the prior task.
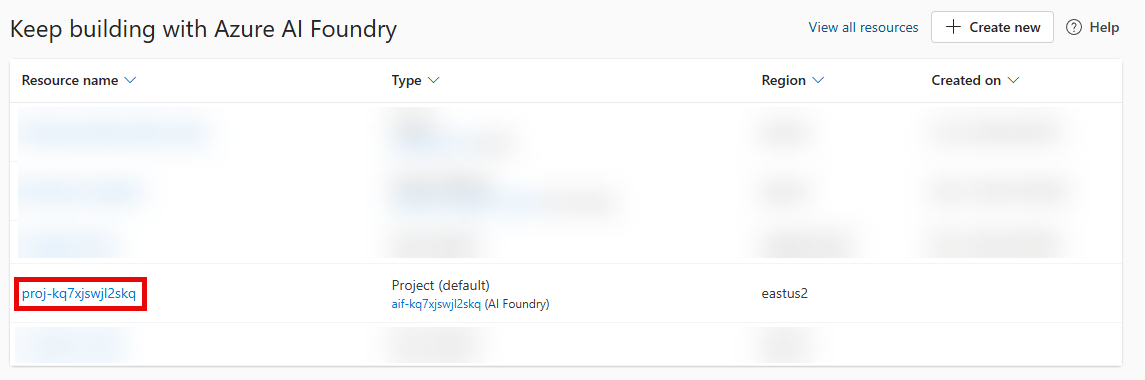
From the Build menu, select Models from the list. Then, select the Deploy a base model.
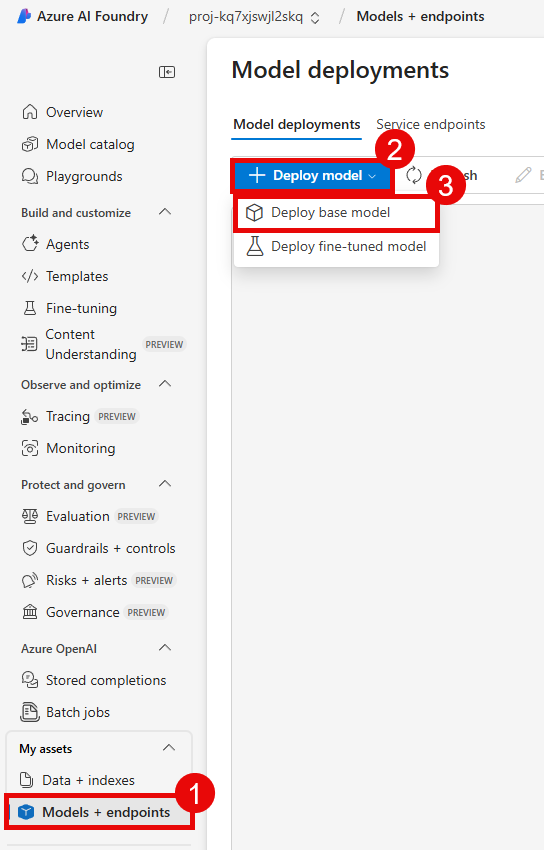
On the Models page, enter phi-4 in the search box and select the Phi-4 model from the list. Then, select Confirm to create a Phi-4 deployment in your project.
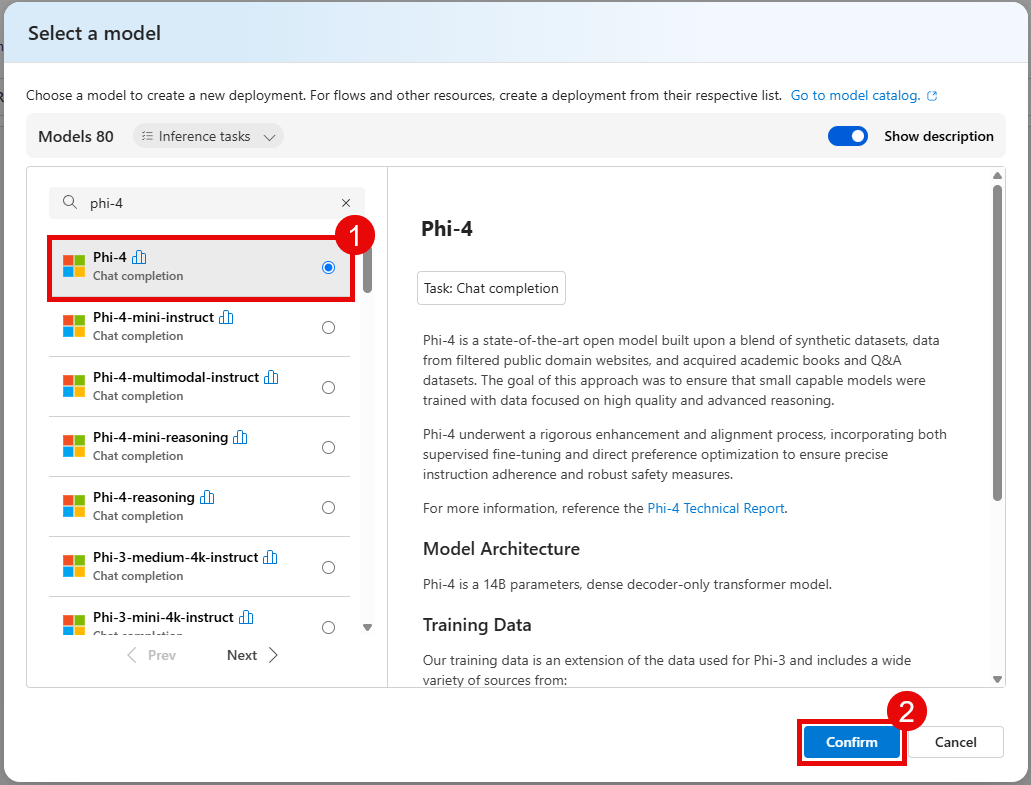
Select the Deploy button and then choose Default settings. On the modal dialog, select Agree and proceed to deploy the model.
Repeat this process for gpt-5-mini and text-embedding-3-large. You will have three model deployments in total.
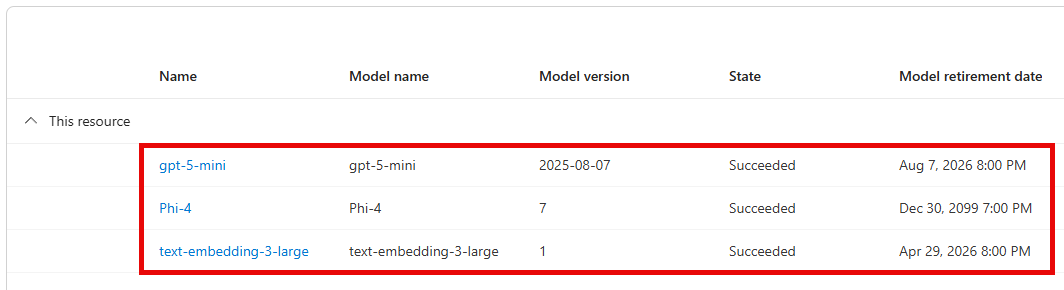
02: Grant storage account permissions
In order to integrate your storage account with your Microsoft Foundry project, you will need to grant the project permission to access the storage account. You will also need to grant your own user account permission to access the storage account so that you can run the code in this training.
Expand this section to view the solution
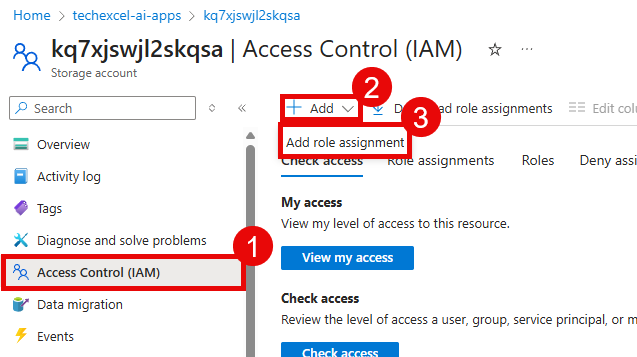
In the Azure portal, navigate to the storage account that you connected to your Microsoft Foundry project in the previous step.
Select the Access control (IAM) option from the left-hand menu. Then, select the + Add button and choose Add role assignment.
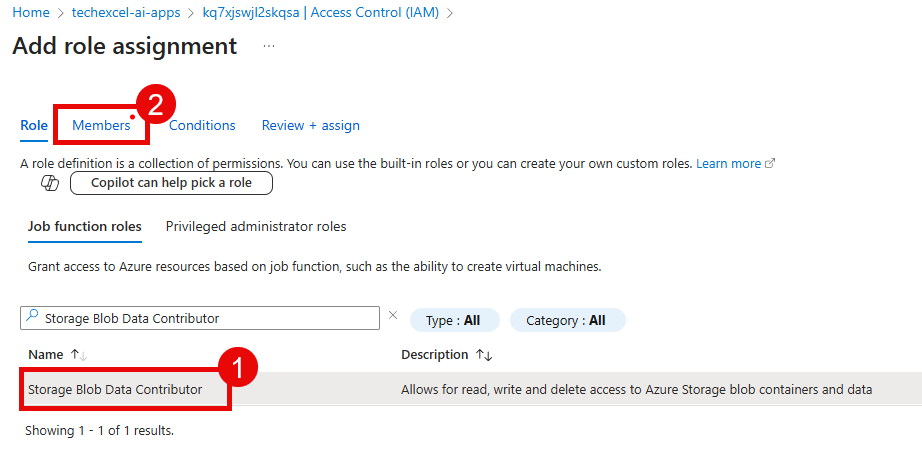
Choose the Storage Blob Data Contributor role from the Job function roles list. Then, select Members.
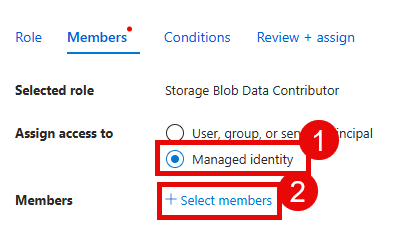
Select the Managed identity radio button and then choose + Select members.
In the flyout pane, ensure your subscription is selected. Then, select Foundry project (previously known as Azure AI Foundry project) from the Managed identity drop-down list. Choose the Microsoft Foundry project associated with this training and then select the Select button at the bottom of the pane. This must be the project and not the Microsoft Foundry resource itself.
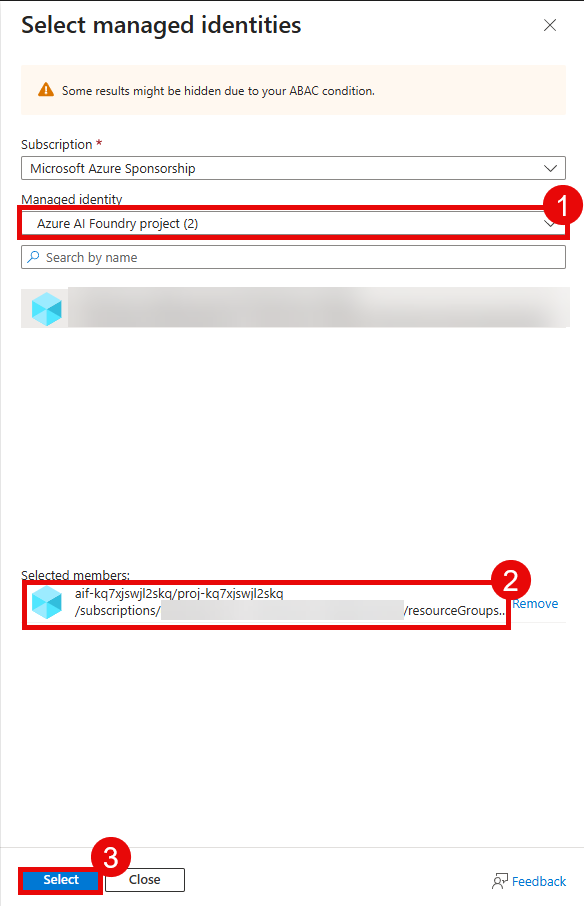
After adding the managed identity, select User, group, or service principal from the Select members pane. Then, search for your own user account and select it from the list. Finally, select the Select button at the bottom of the pane.
When you are back on the Add role assignment pane, select the Review + assign button twice to grant both the managed identity for your Microsoft Foundry project and your own user account the Storage Blob Data Contributor role on this storage account. 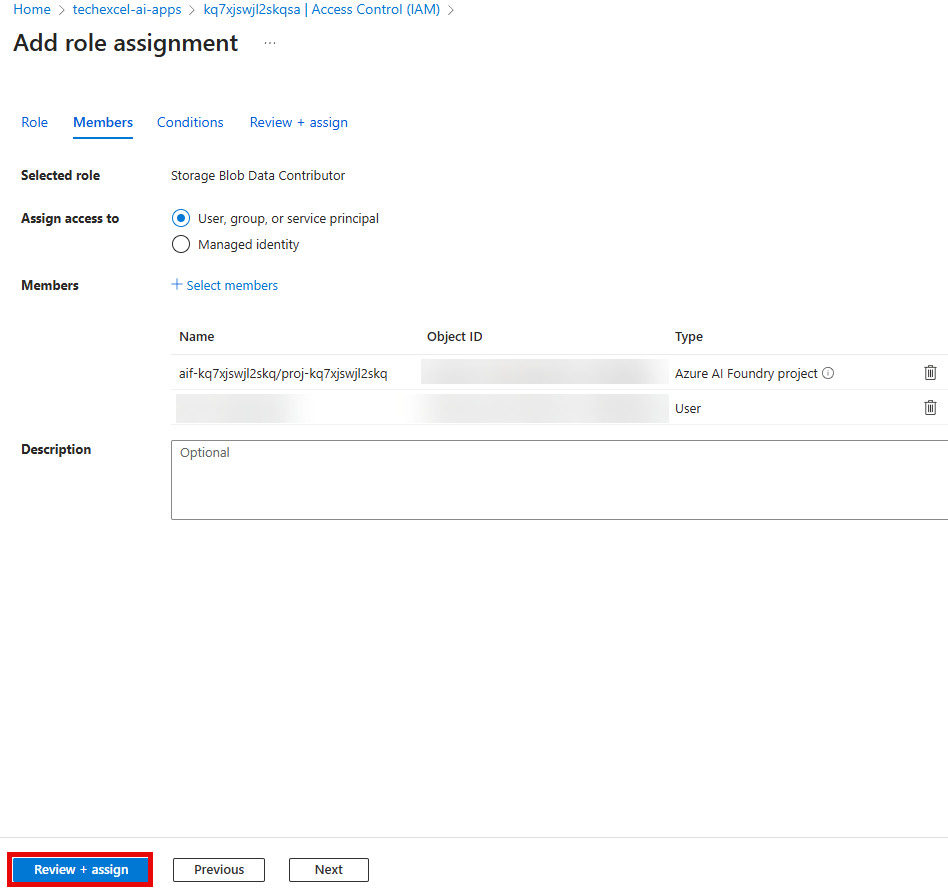
03: Create .env file
In order to run the code in this training, you will need to create a .env file in the src directory of the repository that you cloned in the first task. This file will contain the necessary environment variables for your application to connect to the Azure resources that you deployed and configured in the previous tasks. Use the file src/env_sample.txt as a template for creating your .env file.
Expand this section to view the solution
Copy the file src/env_sample.txt to a new file named .env in the same directory. Then, open the .env file in a text editor and update the values for each environment variable to match your Azure resources. For any environment variables with pre-filled values, you can leave them as they are unless you explicitly changed the names of the resources during deployment.
You will find many of these variables in the Microsoft Foundry project that you created. To find these values, start by navigating to the Home page.
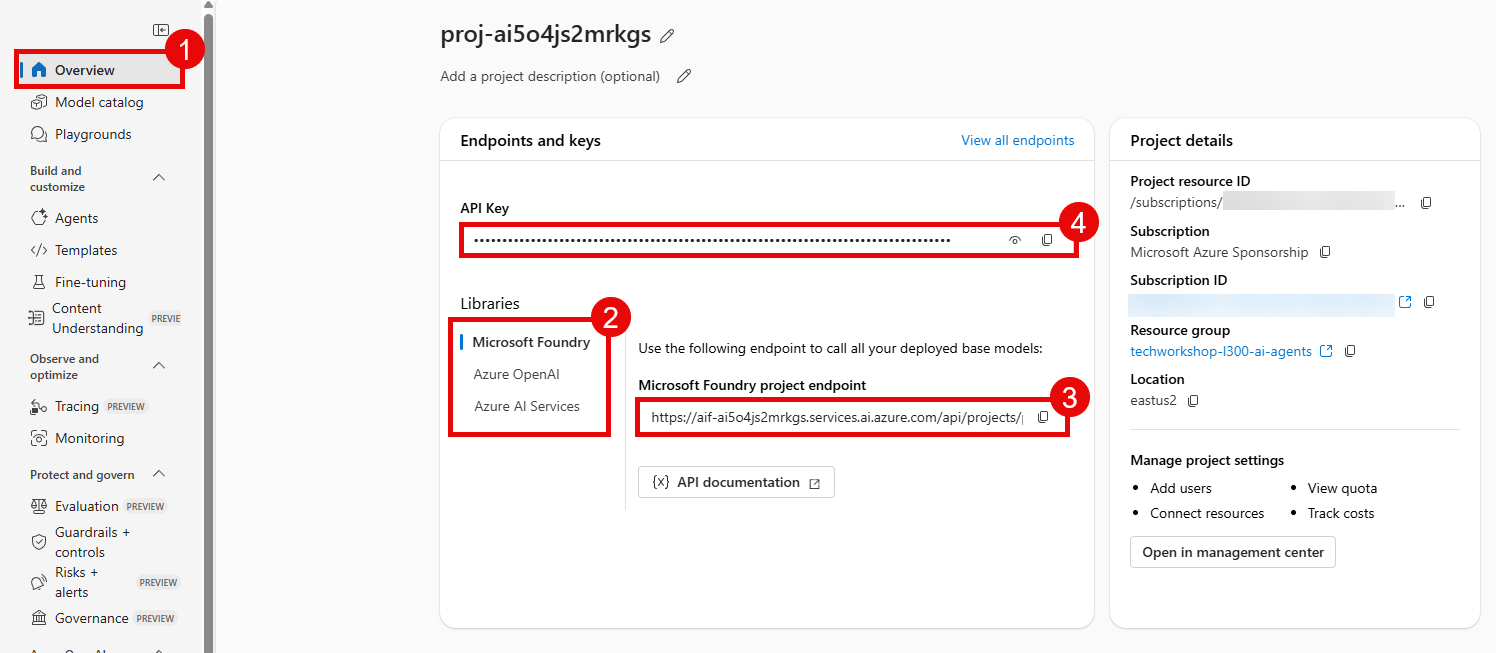
Then, fill in the following.
FOUNDRY_ENDPOINT: Copy the Project endpoint box.FOUNDRY_KEY: Copy the Project API Key box.
For the following variables, navigate to the Models menu option from the Build menu.
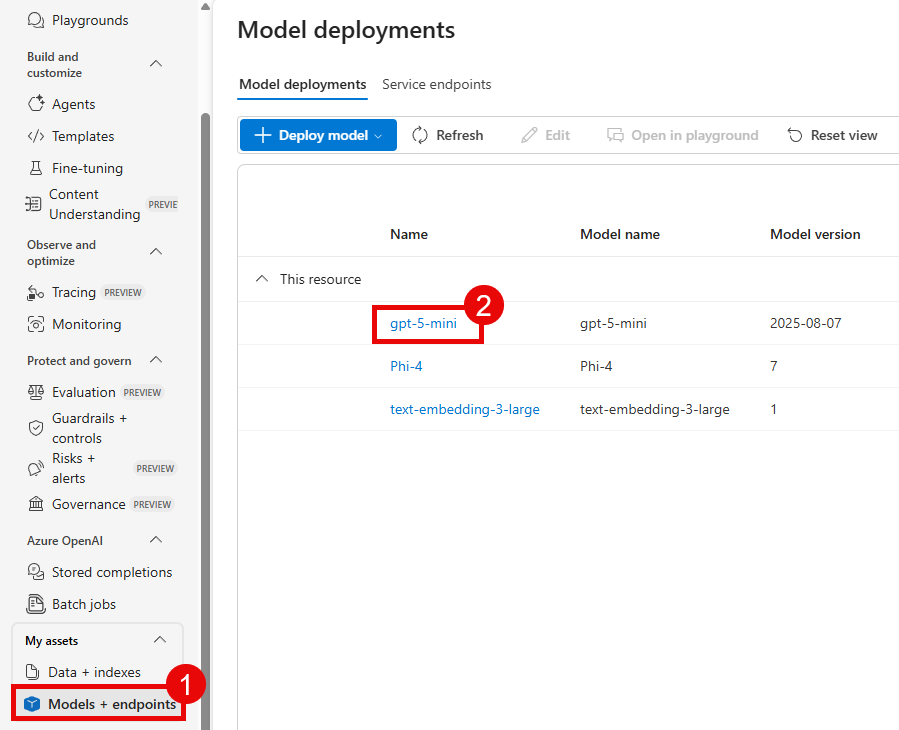
Then, select the appropriate model deployment that you created in the previous step and navigate to the Details tab in order to fill in the details below. Start with the gpt-5-mini deployment.
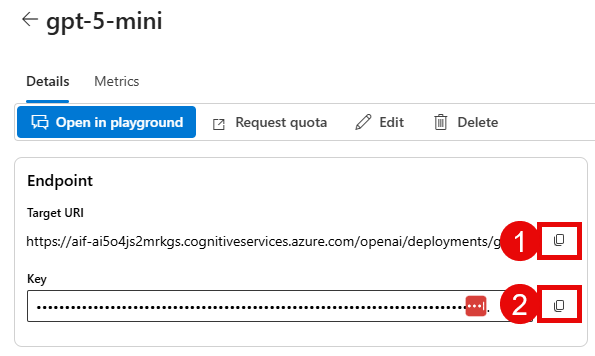
gpt_endpoint: Copy the Target URI box from the gpt-5-mini deployment and save everything prior to/openaiin the URI. It should look something likehttps://{YOUR_AI_FOUNDRY}.cognitiveservices.azure.com/.gpt_api_key: Copy the Key box from the gpt-5-mini deployment.
Repeat this process to collect the text-embedding-3-large endpoint details:
embedding_endpoint: Copy the Target URI box from the text-embedding-3-large deployment. You can copy and paste the entire URL for this endpoint.embedding_api_key: Copy the Key box from the text-embedding-3-large deployment.
Repeat this process to collect the Phi-4 endpoint details, with one major exception.
phi_4_endpoint: Use the following URL, populating the value of your Microsoft Foundry name for{YOUR_AI_FOUNDRY}:https://{YOUR_AI_FOUNDRY}.services.ai.azure.com/models.phi_4_api_key: Copy the Key box from the Phi-4 deployment.
For the following variables, navigate to the Azure Portal and open the storage account that you granted permissions to in the prior task. Then, navigate to the Access keys option from the Security + networking menu on the left-hand side.
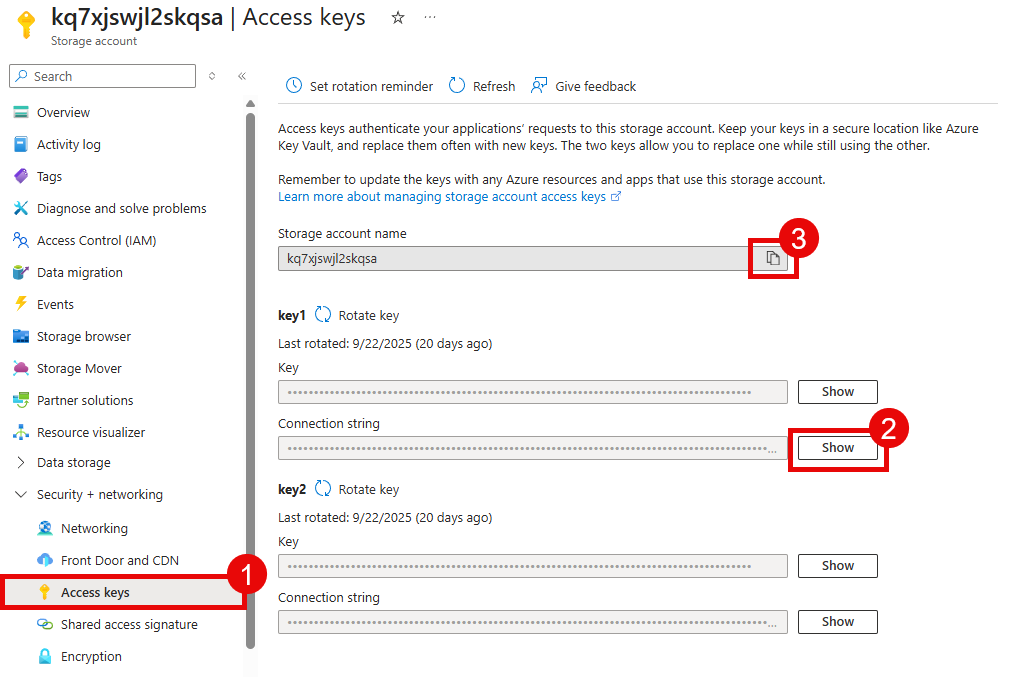
blob_connection_string: Copy the value for Connection string from the key1 section.storage_account_name: Copy the value for Storage account name.
The
blob_connection_stringvariable is used as a fallback in case your managed identity access does not work. Otherwise, it will not be used in this training.
To fill in the Cosmos DB variables, navigate to the Cosmos DB account that you created in the first task.
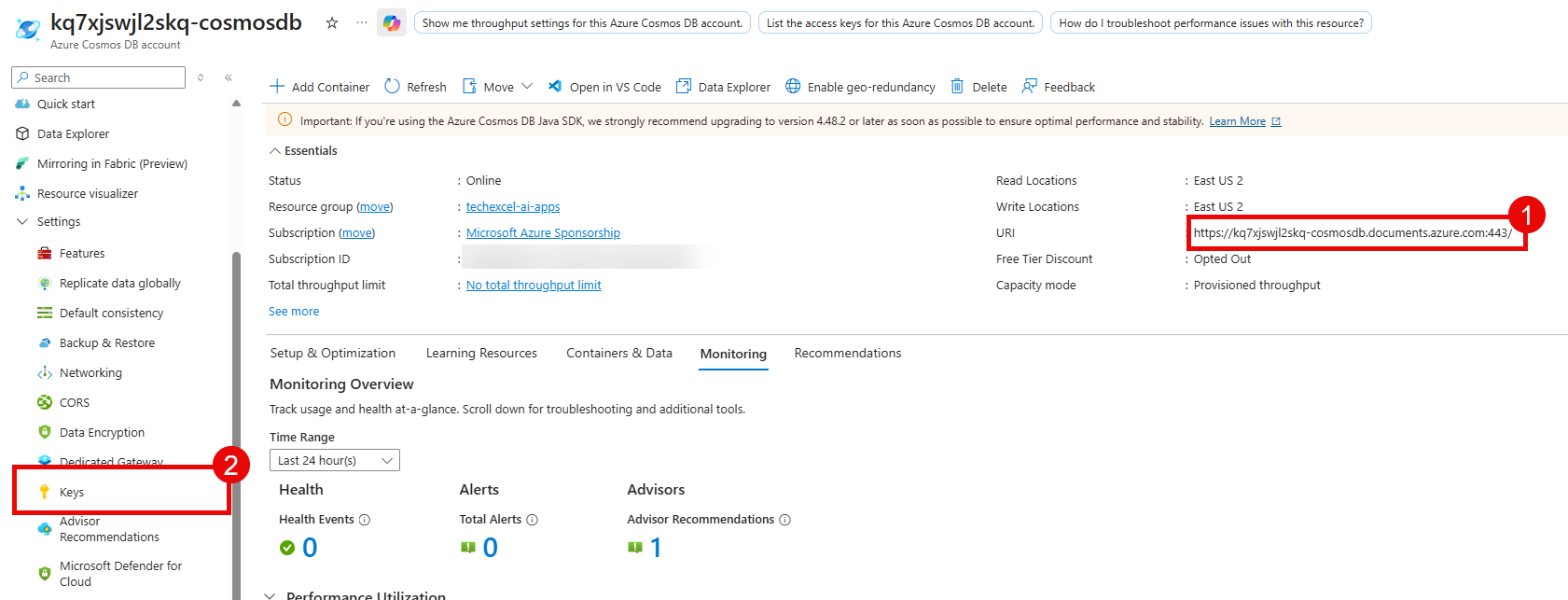
COSMOS_ENDPOINT: Copy the value for URI from the Overview page.COSMOS_KEY: Copy the value for PRIMARY KEY from the Keys page in the Settings menu.
The
COSMOS_KEYvariable is used as a fallback in case your managed identity access does not work. Otherwise, it will not be used in this training.
For the following variable, navigate to the Application Insights resource that you created in the first task.
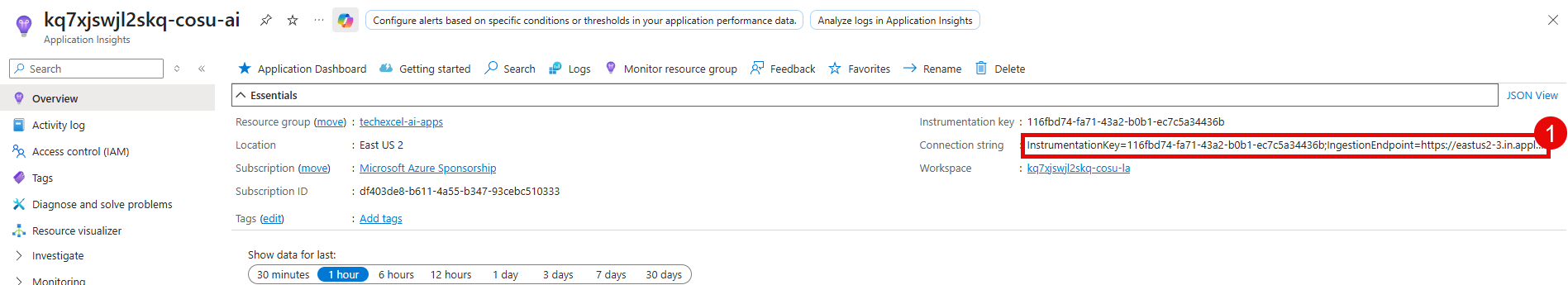
APPLICATIONINSIGHTS_CONNECTION_STRING: Copy the value for Connection string from the Overview page.
The .env file also includes values for an MCP server location and agent IDs. You will use these in during Exercise 2 and do not need to modify them.