TIP
💡 Learn more : Azure Multi-Factor Authentication (opens new window).
# Multi-Factor Authentication on Azure in a Nutshell
In another Tips and Tricks post, we added Azure Active Directory authentication to an existing App Service Web App. Today, we’ll make sure Multi-Factor Authentication (MFA) is on for that user. There are various services in Azure when it comes to Multi-Factor Authentication (opens new window), so let’s first see what’s available. Keep in mind, I want it to be FREE.
If you take a look at the documentation on how it works, the following MFA offerings are listed:
- Azure Active Directory Premium – Licenses for full-featured, on-premises, or cloud-hosted MFA services.
- Multi-Factor Authentication for Office 365 – MFA features included with an Office 365 subscription.
- Azure Active Directory Global Administrators – MFA capabilities made available for free by Microsoft for protecting global administrator accounts.
Note I am using a Microsoft account that is a global administrator on my pay-as-you-go Azure account.
# There are several MFA offerings, but I didn’t use them
So why didn’t I use Azure Active Directory Premium, MFA for Office 365, or MFA for Azure Active Directory Global Administrators?
First, I didn’t want to pay for Azure Active Directory Premium. Also, I didn’t use MFA for Office 365 because it is for accounts connected to an Office 365 account, which I didn’t have. Finally, Azure Active Directory Global Administrators MFA is a two-step verification for Azure Active Directory users (opens new window) and not a Microsoft account. There are ways to turn two-step verification on for Microsoft accounts (opens new window) that are done outside of Azure, which I didn’t want to do.
While researching why I couldn’t enable MFA for my Microsoft account user, I found a newer feature that also provides MFA called Baseline Protection. The nice thing about using Baseline Protection (opens new window) is it works well for Microsoft accounts and Azure Active Directory accounts.
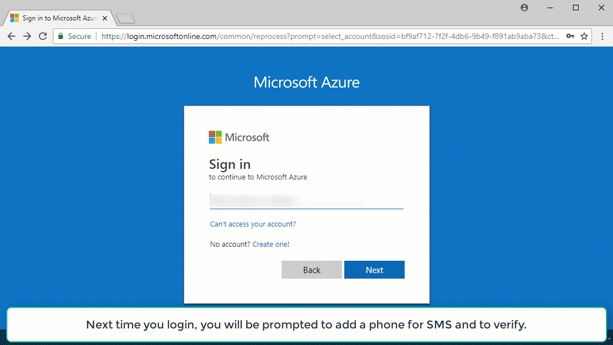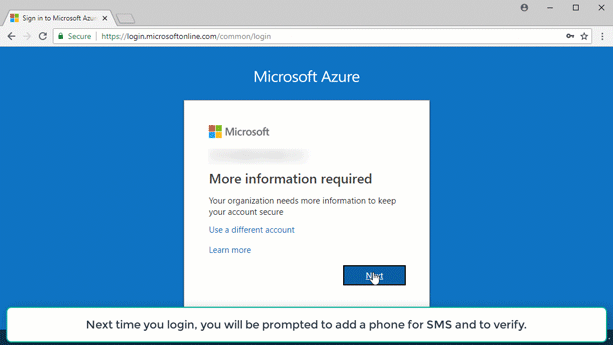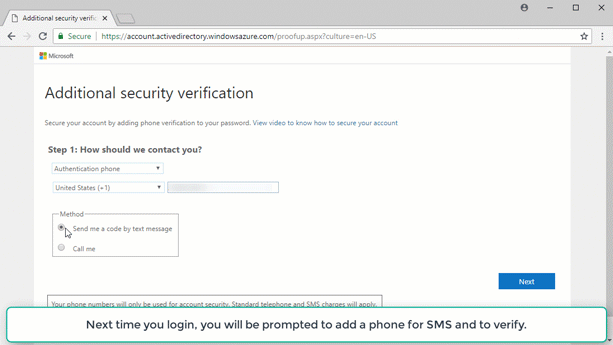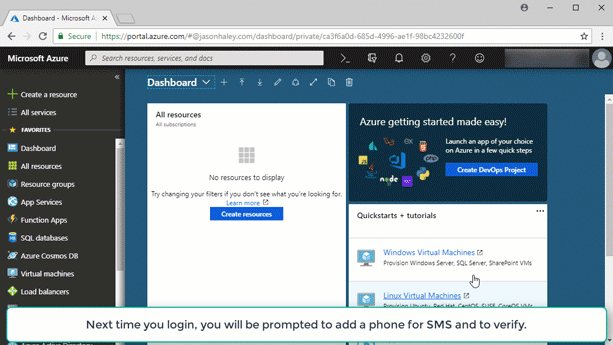
# How I turned on Multi-Factor Authentication using Baseline Policy
Go to the Azure portal and navigate to Azure Active Directory, and then click Conditional access under Security. Since I’m using my own pay-as-you-go subscription, this is the default directory.
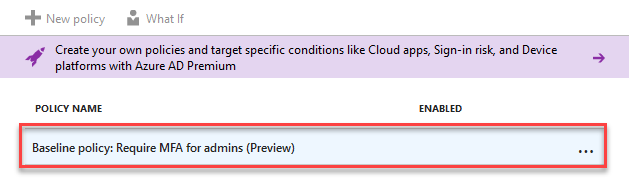
Click on Baseline policy: Require MFA for admins (Preview) in the list of policies.
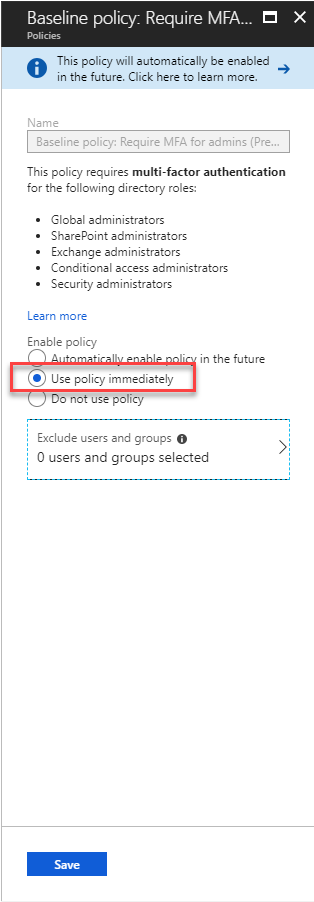
Select Use policy immediately and click the Save button.
Once you have saved, you’ll now see a checkmark in the Enabled column of the policy listing.
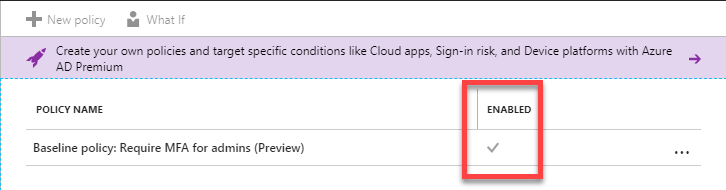
Excellent! Now all global administrators of my Azure account will have Multi-Factor Authentication turned on.