TIP
🔥 Make sure you star the repo (opens new window) to keep up to date with new tips and tricks.
💡 Learn more : Microsoft Azure Key Vault (opens new window).
📺 Watch the video : Azure Functions and secure configuration with Azure Key Vault (opens new window).
# Azure Functions and secure configuration with Azure Key Vault
# Protecting Application Secrets
Almost every application uses application secrets. These are often values that you use to connect to other services, like a connection string to Azure Storage (opens new window), or an API key to connect with a 3rd party API. Where do you store these secrets securely? And how can you make sure that the right people can configure these secrets? (like DevOps engineers). You shouldn't store secrets in your application code, because every developer would be able to see them. You could store your secrets in the application configuration of your app, like in the configuration settings of your Azure Function (opens new window). This works, but requires DevOps engineers to go into the configuration settings of all individual services to update a setting if the value changes.
A better place to store application secrets is in Azure Key Vault (opens new window). This is an Azure service that allows you to store secrets, keys and certificates in a single place and retrieve them from your applications. Many services in Azure can connect to Azure Key Vault out-of-the-box. In this post, we'll explore how to retrieve a secret from Azure Key Vault from an Azure Function.
# Prerequisites
If you want to follow along, you'll need the following:
- Visual Studio 2019 (opens new window) with the Azure workload selected or VS Code (opens new window) with the Azure Function and C# Extensions installed
- An Azure subscription (If you don't have an Azure subscription, create a free account (opens new window) before you begin)
# Use Azure Function to retrieve a secret from Azure Key Vault
We are going to create a simple Azure Function that reads a secret value from Azure Key Vault. To connect to Azure Key Vault, we'll use the built-in Managed Service Identity (opens new window). Using this, we can easily connect to Azure Key Vault, without storing an API Key for Azure Key Vault in our Azure Function. I'm going to create the Azure Function with Visual Studio, but you can also create it with VS Code or whatever other tool that you prefer.
1. Create the Azure Function
- Open Visual Studio 2019
- Select Create a new project
- Select Azure Functions (C#) and click Next
- Pick a name and location for the Function and click Create
- Now select Http trigger for the Function Type and select Anonymous for the Authorization level. This enables us to test the Function easily
- Click Create to create the Azure Function
We'll keep the Function very simple. In the function, we will add a few lines of code that will read the secret from the Azure Function configuration and display the value in the log. Add the following code:
var config = new ConfigurationBuilder()
.AddEnvironmentVariables()
.Build();
var secret = config["MySecret"];
log.LogInformation($"MySecret:{secret ?? "null"}");
2
3
4
5
6
7
Also add the following using statement:
using Microsoft.Extensions.Configuration;
Now we publish the Function to Azure and create a new Azure Function in the process:
- In Visual Studio, right-click on the project file and select Publish
- In the Pick a publish target window, select Azure Functions Consumption Plan and Create New and click Create Profile
- Leave the information that has been filled out as it is or change it where you want. Click Create to create the Azure Function in Azure
- When the Function is created, you are returned to the Publish window. Click Publish to publish the code to the Function in Azure
That's it. The Function is now running in Azure.
2. Create a Managed Service Identity for the Azure Function
We need to create an Azure Managed Service Identity for the Azure Function. This will enable the Function to connect to Azure Key Vault easily.
- Go to the Azure portal (opens new window)
- Navigate to the Azure Function that we've just created
- Click on the Platform features tab
- Now click on Identity
- In System assigned, change the status to On and click Save
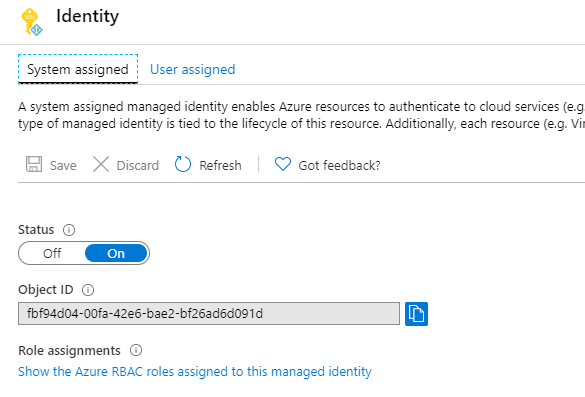
(Configure Azure Function Identity)
3. Create and configure Azure Key Vault
Let's create the Azure Key Vault that will store the application secret:
- Go to the Azure portal (opens new window)
- Click the Create a resource button (the plus-sign in the top left corner)
- Search for Key Vault and click on the result to start creating an Azure Key Vault
- This brings you to the create Azure Key Vault blade
- Select a Resource Group
- Fill in a Name for the Key Vault
- Select a Region
- Leave the rest of the settings as they are and click Review + create
- Click Create to create the Azure Key Vault
After a while the Azure Key Vault is deployed. Navigate to it to start configuring it.
- In the Azure portal, navigate to the Azure Key Vault
- Click on the Access policies menu. We'll add a policy here that allows the Azure Function Managed Service Identity to access the Key Vault
- In the Add access policy blade, click on Service principal
- Search for the name of the Azure Function and select the service principal that belongs to the Function
- Also, select at least the Get operation of Secret permissions. This allows the service principal to get a secret from Azure Key Vault
- Click Add to add the policy
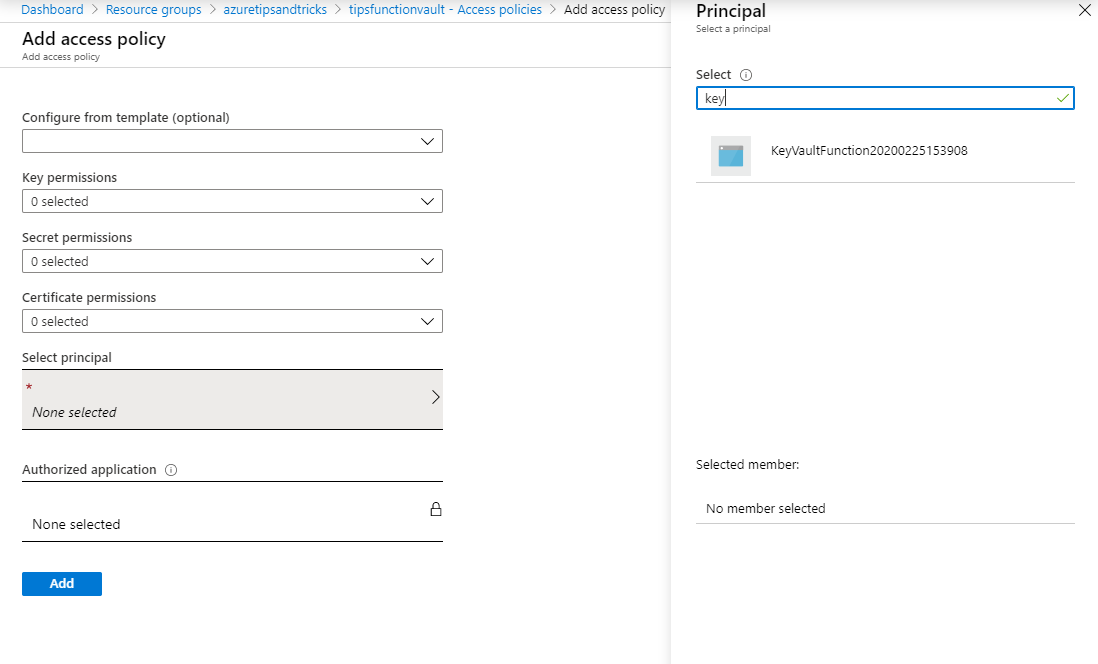
(Add Azure Key Vault Policy)
Now we'll add a secret to the Azure Key Vault that we can read from the Azure Function:
- In the Azure Key Vault in the Azure portal, select the Secrets menu item
- Click Generate / Import
- Give the secret the Name MySecret
- For Value, enter Secretvalue
- Click Create to create the secret
- Once the secret is created, click on it to go into its details
- You'll see the Current Version of the secret (items in Key Vault can have versions). Click on the current version to drill into it
- You are now seeing the details of the secret. Copy the Secret Identifier. We'll need to use that in the Azure Function
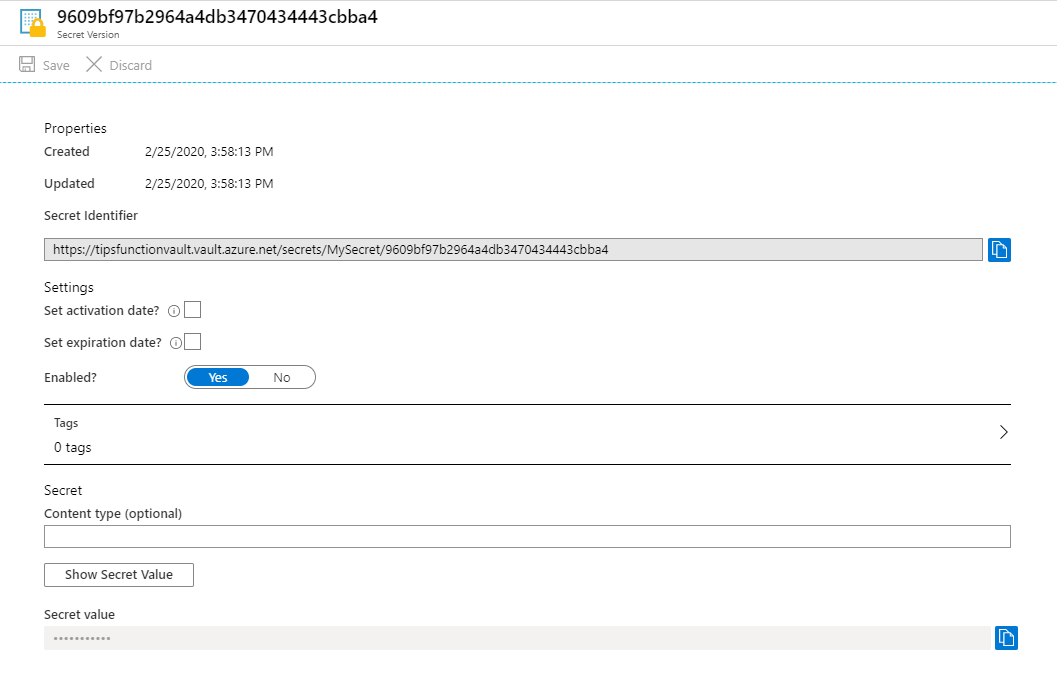
(Copy the Secret Identifier)
4. Configure and run the Azure Function
Now that the Azure Key Vault is configured and it has a secret in it, we can read that secret from our Azure Function:
- In the Azure portal, navigate to the Azure Function that we've created earlier
- Navigate to Platform Features
- Click on Configuration
- We are going to add a reference to the secret in the Azure Key Vault into the Function configuration. Click New application setting
- For the Name of the setting, type in MySecret. That is what the code in the Azure Function will read
- For the Value of the setting, type in @Microsoft.KeyVault(SecretUri=) and insert the Secret Identifier from the Key Vault secret just after the equals sign. This value format uses the native capability of Azure Functions to connect to Azure Key Vault
- Click OK
- Click Save to save the new setting
Once the setting has been saved, you'll see that it says Key vault Reference in its "Source" column. And if the value was entered correctly, it will show a green checkmark in front of Key vault Reference, like in the image below:
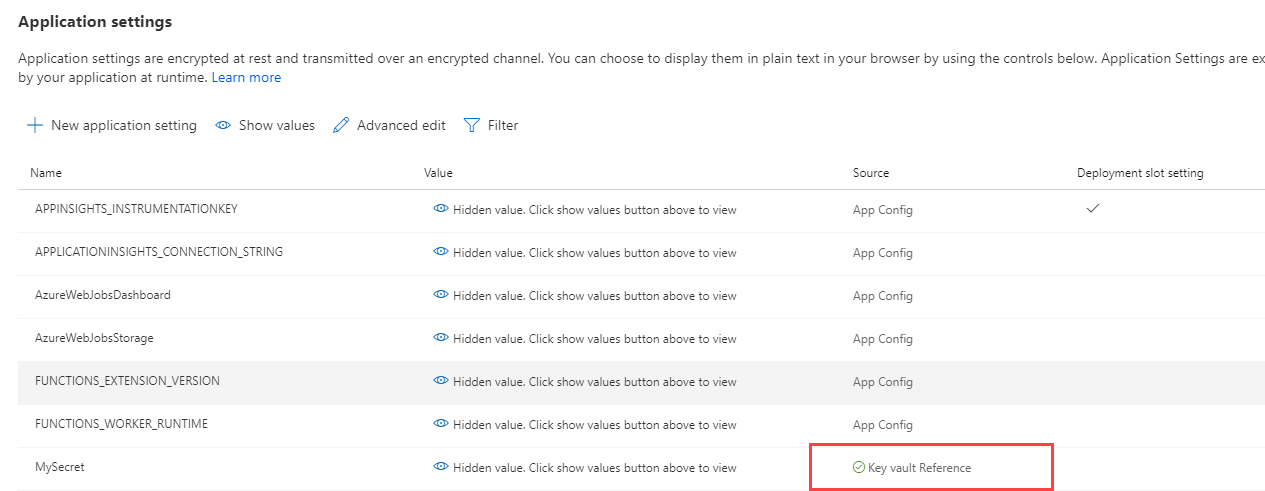
(Setting is a Key vault Reference in Azure Function)
That's it! Let's test it.
- In the Azure portal, click on the Function in the Function App
- Click Run to start the Function
- Take a look at the Log. This will show a log entry that contains the secret value from the Azure Key Vault
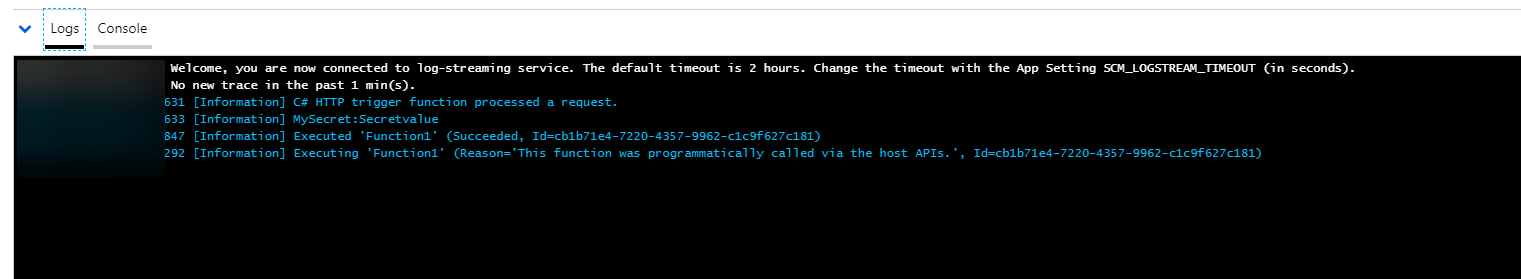
(The setting from Azure Key Vault is logged when the Azure Function runs)
# Conclusion
It is a best practice to keep secrets out of your code and to centralize their management. Azure Key Vault (opens new window) is a great service to keep secrets safe and in a central location. And it is very easy to use Azure Key Vault from an Azure Function (opens new window). All you need is a Managed Service Identity (opens new window) and to reference to the Azure Key Vault in a configuration setting value. Go and check it out!
