TIP
🔥 Checkout our new Azure Developer page at azure.com/developer (opens new window).
💡 Learn more : Azure Security Center JIT (opens new window)
This post was brought to you by Kumar Allamraju (opens new window).
# Reduce Brute Force attacks to Azure VMs
# Enabling Just In Time access to Azure VMs
Brute force attacks commonly target management ports (22 for SSH, 3389 for RDP etc.) as a means to gain access to Compute VMs. If successful, an attacker can take control over the VM and establish a foothold into your environment.
In this post, I will explain how JIT access to Azure virtual machines enables us to further secure Azure VMs and enable on-demand access to the machines.
# What is JIT access?
Azure Security Center provides several threat prevention mechanisms to help you reduce surface areas susceptible to attack. One of those mechanisms is Just-in-Time (JIT) VM Access. Management ports do not need to be open at all times. They only need to be open while you are connected to the VM, for example to perform management or maintenance tasks. When you enable JIT for your VMs, you can create a policy that determines the ports to be protected, how long ports remain open, and approved IP addresses from where these ports can be accessed. The policy helps you stay in control of what users can do when they request access. Requests are logged in the Azure Activity Log, so you can easily monitor and audit access. The policy will also help you quickly identify existing virtual machines that have JIT enabled and virtual machines where JIT is recommended.
# How does it work?
Launch an Azure VM.
Go to your running VM. Under Settings >> Configuration section
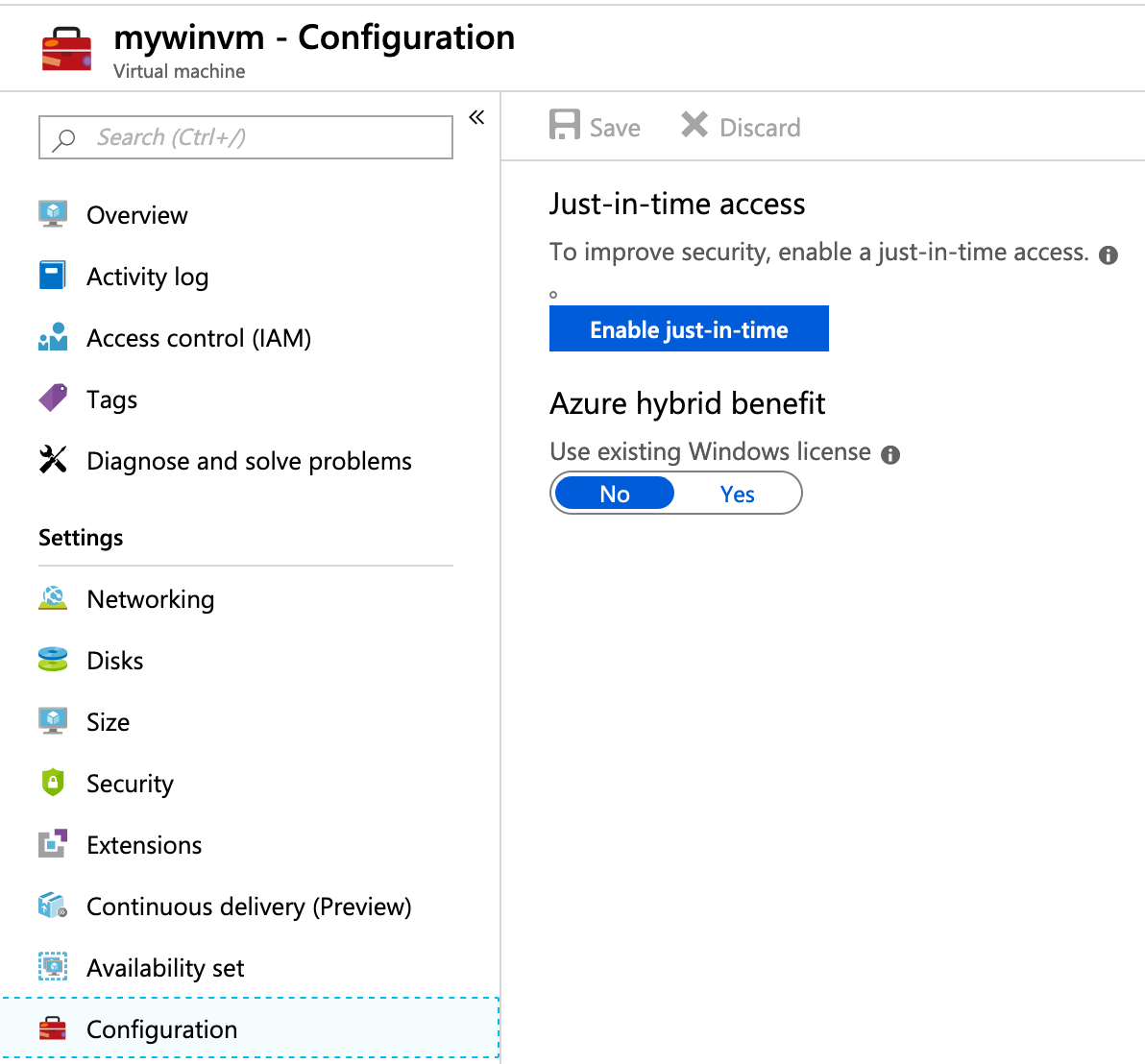
Click on “Enable just-in-time” button.
Go back to Security Center blade in Azure Portal. select “Just in time VM access” under ADVANCED CLOUD DEFENSE section
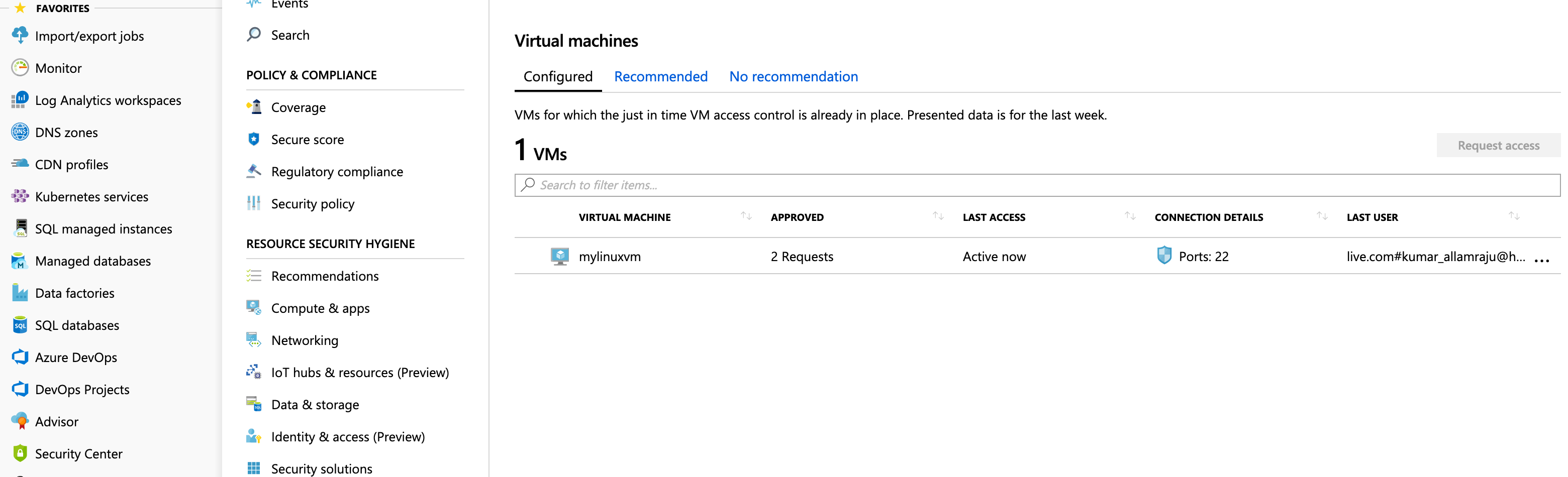
- Click on “Request Access”
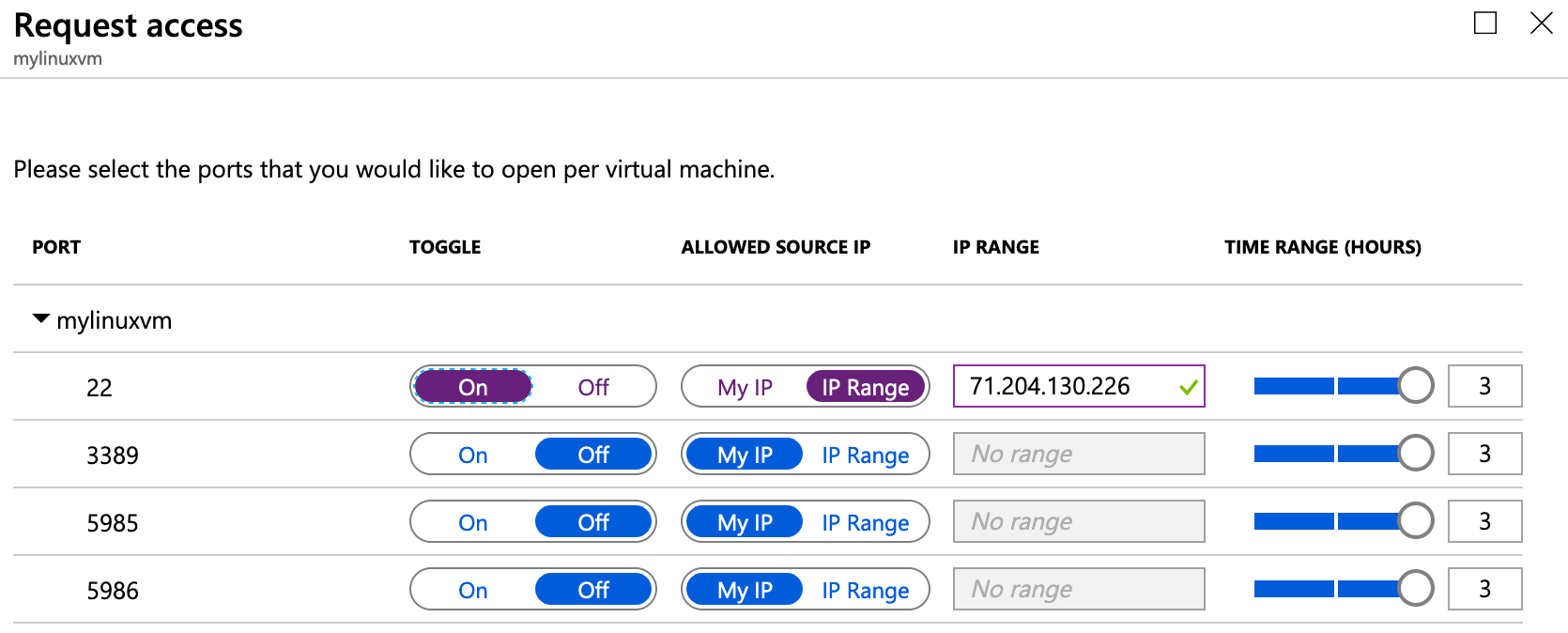
Toggle the On/Off option and choose the My IP or IP Range. Make sure to save the changes.
After this change you can only SSH to this VM from the source IP. Any other source IPs will get denied access. When the agreed time has expired, JIT VM Access will automatically remove the allowed rule and re-lock down the environment.
# Conclusion
Microsoft uses a wide variety of physical, infrastructure, and operational controls to help secure Azure—but there are additional actions you need to take to help safeguard your workloads. Just-in-Time VM Access reduces your surface area exposed to RDP/SSH brute-force attack. This feature is available in the standard pricing tier of Azure Security Center, and you can try Security Center (opens new window) for free for the first 60 days. Go and try it out!
