TIP
💡 Learn more : Securing your SQL Server Database (opens new window)
This article was brought to you by @kumarallamraju (opens new window)
# Securing your managed Databases in Azure
# Intro
Microsoft Azure provides support for a wide variety of commercial (SQL Database and SQL Managed Instance) and open source databases (MySQL, PostgreSQL, MariaDB). When it comes to protecting your data, Azure provides different security layers. Let's discuss those options below
# 1. Server Firewall
By default Azure Databases are provisioned with a public endpoint e.g. kasqlserver.database.windows.net
Although it's a public endpoint and discoverable by default the access is denied. You can set a "DB server firewall" rule to allow client IPs to communicate with the database server.
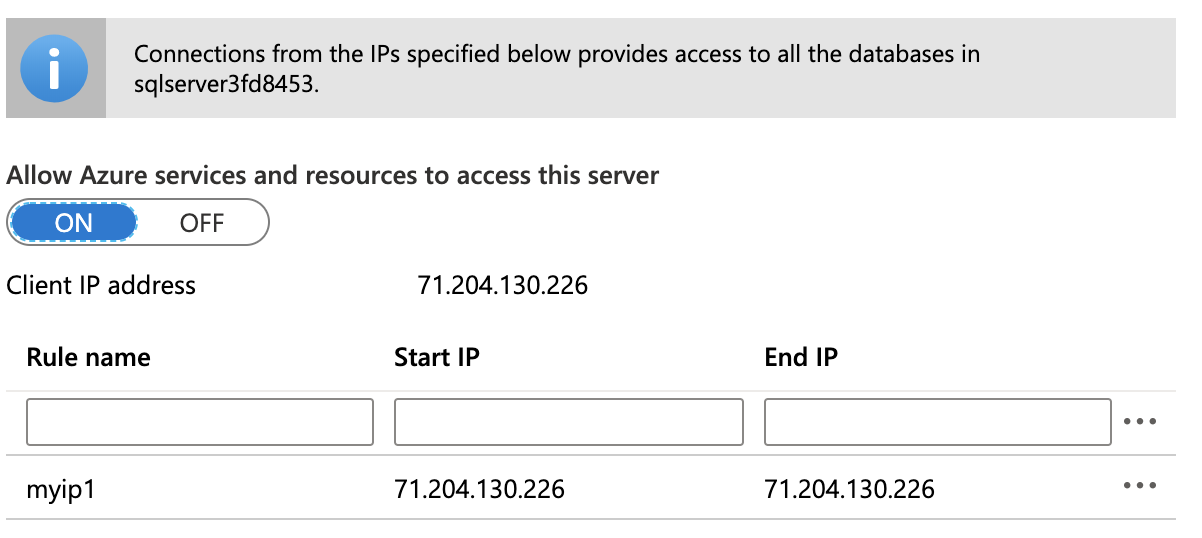
As you notice above, I'm allowing the traffic from my home IP address.
# 2. Integration with Virtual Networks
The second option is to connect to the Database server from your VNets. This can be done by going to Security >> Firewalls and Virtual Networks section in Azure Portal.
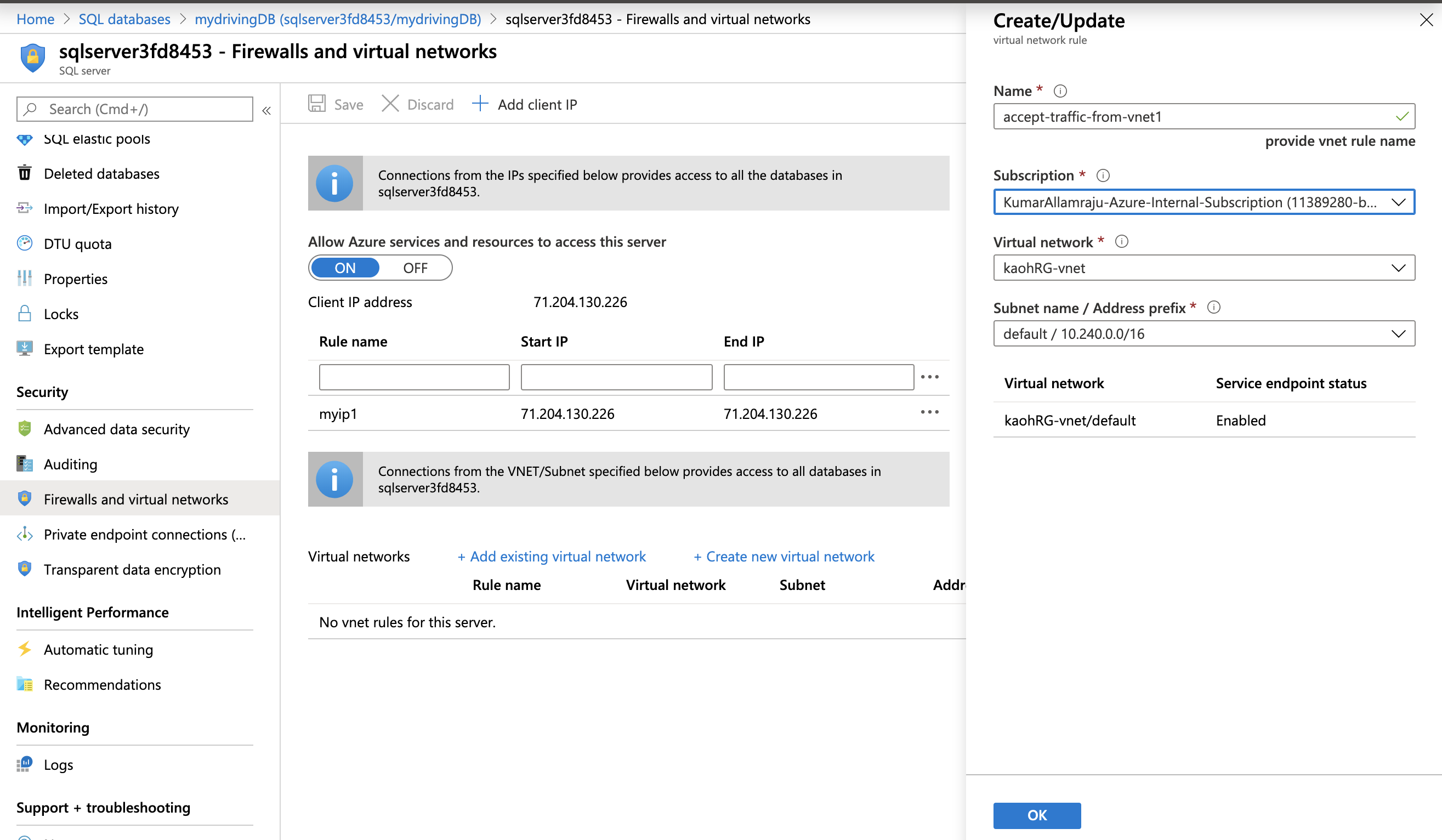
You can spin up an Azure VM in a VNet, install the SQL Server Management Studio (for SQL Server) and add this VNet as mentioned in the above screenshot. Although you are still connecting to a public endpoint, the traffic stays within Azure backbone.
# 3. Private Endpoint (in public preview)
You can use Azure Private Link to access Azure PaaS Services (for example, Azure Storage, Azure Cosmos DB, and SQL Database) and Azure hosted customer/partner services over a Private Endpoint in your virtual network. Traffic between your virtual network and the service traverses over the Microsoft backbone network, eliminating exposure from the public Internet. As an example you will be connecting to your database server on a private endpoint e.g. "kasqlserver.privatelink.database.windows.net"
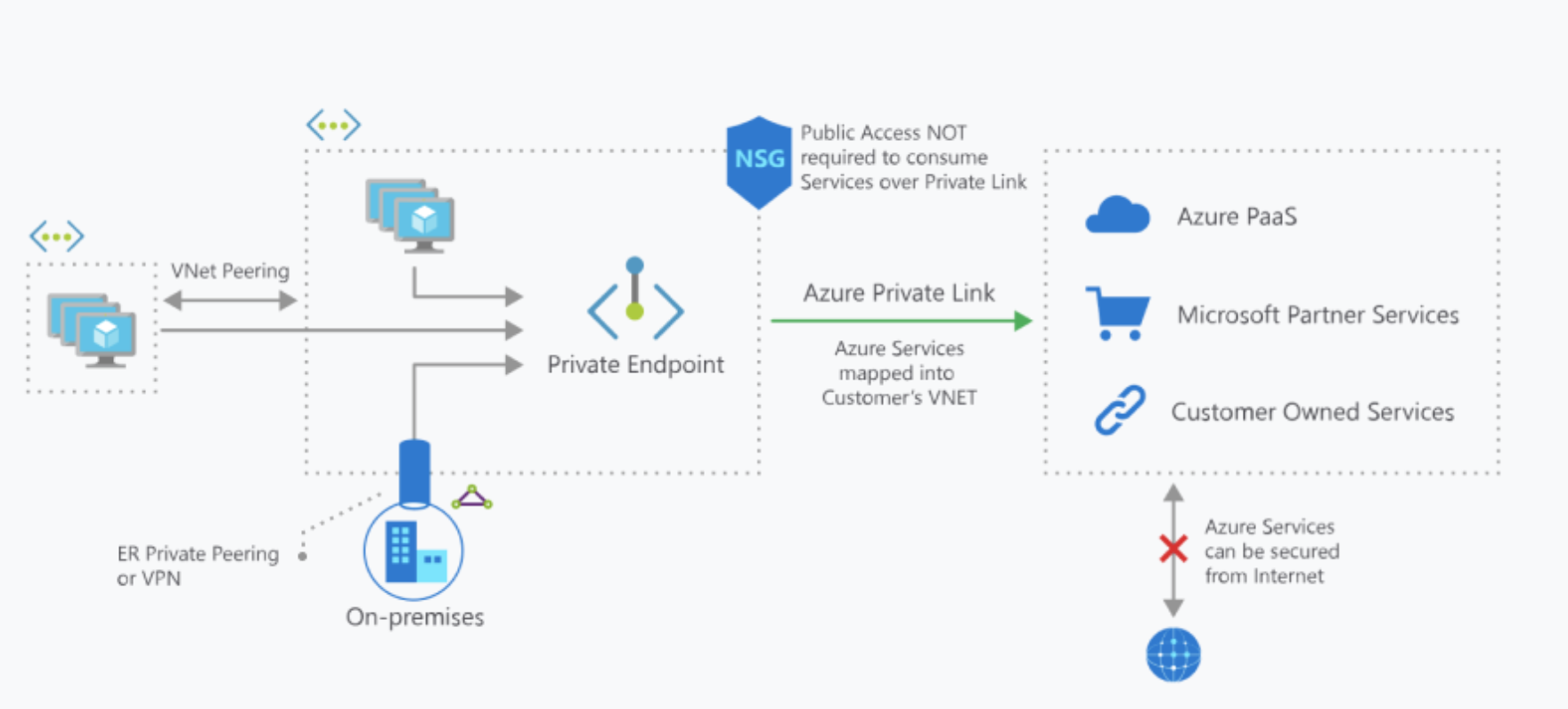
You can refer to this link (opens new window) to provision a Private Endpoint to your SQL Database.
We have seen a great response from customers who tried Azure Private Link and are actively using for dev/staging databases. Once the feature goes to General Availability (GA), we anticipate the customers will adopt this feature for production databases as well.
# 4. SQL Managed Instance
As part of the provisioning process, SQL MI will be created in your VNet so it will have a private IP address. You can connect to the private endpoint from your on-premises via VPN/Express Route or from an Azure VM provisioned in the same VNet.
# Conclusion
As the platform evolves, we continue to add more security features to protect your data in the public cloud. This is the just the beginning and I anticipate we continue to add more features in the months to come. I highly recommend you to consider the above options to secure your databases and as always pls provide your valuable feedback.
