TIP
🔥 Download the FREE Azure Developer Guide eBook here (opens new window).
💡 Learn more : Azure Security Center overview (opens new window).
📺 Watch the video : How to connect GitHub Actions to Azure Security Center (opens new window).
# How to connect GitHub Actions to Azure Security Center
# Integrate security in your DevOps practices
Many companies have adopted DevOps practices, which enable them to automatically build, test and release software. This increases software quality and innovation, as it eliminates human error, and promotes practices like Infrastructure-as-Code (IaC), and container usage. The latter makes things easier by running your applications on the same infrastructure in development, test, and production environments. DevOps is essential, but often lacks integrated security practices. That is where Azure Security Center (opens new window) comes in.
Azure Security Center is an infrastructure security management system that provides advanced threat protection. And now, you can integrate Azure Security Center into your GitHub Actions (opens new window) DevOps process. In this post, we'll explore how to integrate Azure Security Center into GitHub Actions to secure a DevOps pipeline.
# Prerequisites
If you want to follow along, you'll need the following:
- An Azure subscription (If you don't have an Azure subscription, create a free account (opens new window) before you begin)
- A GitHub account. Create one here for free (opens new window)
- A GitHub repository with a containerized ASP.NET application
- Access to an Azure Container Registry (opens new window). Check out Azure Tips and Tricks Tip 312 (opens new window) to learn how to create an Azure Container Registry
# Integrate Azure Security Center into GitHub Actions
We'll use a sample ASP.NET application that has a Docker file, to build a container and push it to Azure Container Registry. From there, the container can be deployed to any service that can run it. In GitHub, we'll create a GitHub Action to build the container, scan it for security vulnerabilities, and send the log results to Application Insights, which is connected to Azure Security Center. And first, we'll need the integration information from Azure Security Center.
- Go to the Azure portal (opens new window)
- Search for Azure Security Center in the search box and click on the result. This will take you to your Azure Security Center
- Navigate to the Pricing & settings menu
- Select your subscription
- Click on Azure Defender Plans
- Make sure that Container registries is enabled. This allows Azure Defender to scan containers in Azure Container Registry
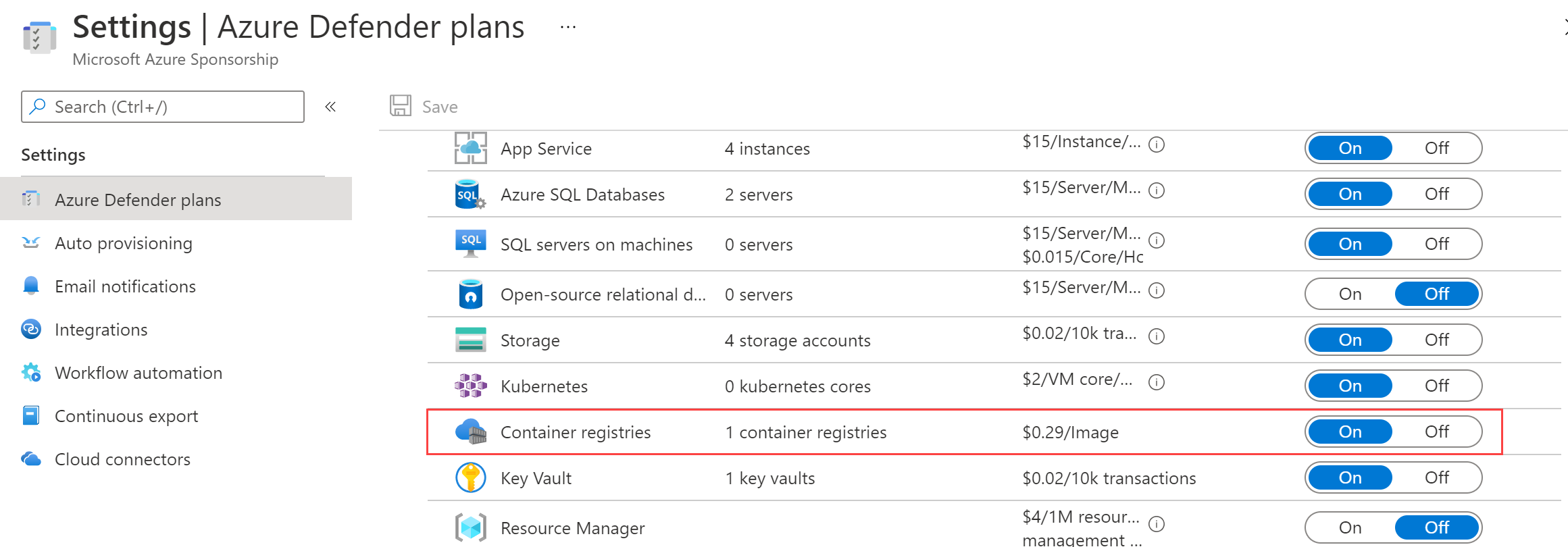
(Enable Azure Defender for Container registries)
- Click on Integrations
- Select Configure CI/CD integration
- Copy the Authentication token and Connection string. We'll use this to send security scan information to the Application Insights workspace that is connected to Azure Security Center
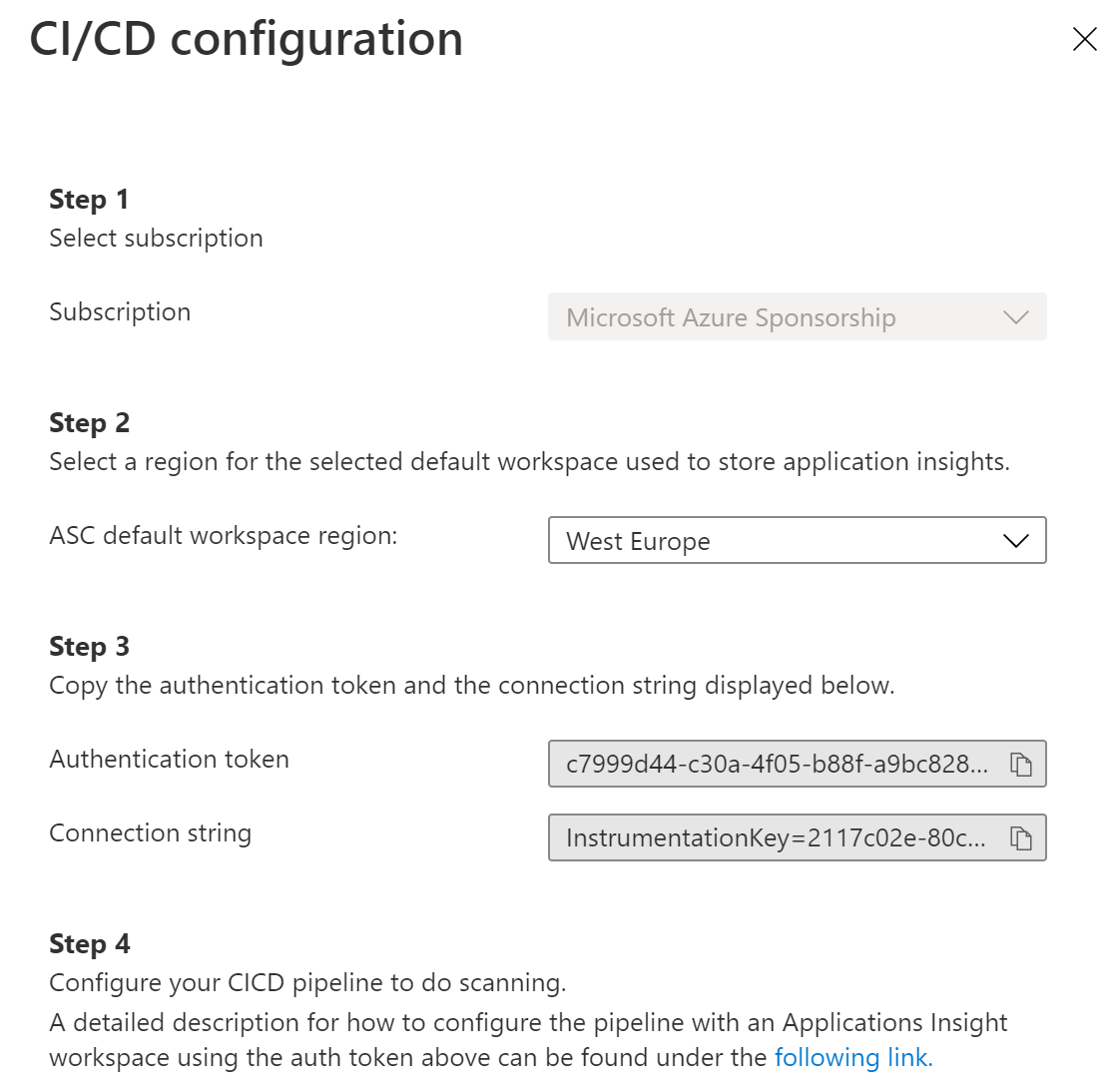
(Configure CI/CD integration in Azure Security Center)
Next, we need to create a GitHub Action that builds and pushes a container and scans it for security vulnerabilities.
- Go to GitHub (opens new window) and open the repository with the containerized ASP.NET application
- Navigate to the Actions menu
- Click New workflow
- Select "set up a workflow yourself" to create a GitHub Action
(Create a new GitHub Action)
- In the main.yml file, paste the following code, and save and commit it
on: [push]
jobs:
build-secure-and-push:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@master
- run: docker build . -t ${{ secrets.ACR_NAME }}.azurecr.io/${{ secrets.ACR_REPOSITORY_NAME }}:${{ github.sha }}
- uses: Azure/container-scan@v0
id: container-scan
continue-on-error: true
with:
image-name: ${{ secrets.ACR_NAME }}.azurecr.io/${{ secrets.ACR_REPOSITORY_NAME }}:${{ github.sha }}
- uses: Azure/docker-login@v1
with:
login-server: ${{ secrets.ACR_NAME }}.azurecr.io
username: ${{ secrets.REGISTRY_USERNAME }}
password: ${{ secrets.REGISTRY_PASSWORD }}
- run: docker push ${{ secrets.ACR_NAME }}.azurecr.io/${{ secrets.ACR_REPOSITORY_NAME }}:${{ github.sha }}
- name: Post logs to appinsights
uses: Azure/publish-security-assessments@v0
with:
scan-results-path: ${{ steps.container-scan.outputs.scan-report-path }}
connection-string: ${{ secrets.AZ_APPINSIGHTS_CONNECTION_STRING }}
subscription-token: ${{ secrets.AZ_SUBSCRIPTION_TOKEN }}
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
- The main.yml contains placeholders for secrets. Go to the repository Settings menu
- Click on the secrets menu
- Add the following Repository secrets:
- name = ACR_NAME, value = The name of the Azure Container Registry, without azurecr.io
- name = ACR_REPOSITORY_NAME, value = The repository name in Azure Container Registry to push the container to
- name = REGISTRY_USERNAME, value = The admin username of the Azure Container Registry
- name = REGISTRY_PASSWORD, value = The admin password of the Azure Container Registry
- name = AZ_APPINSIGHTS_CONNECTION_STRING, value = The CI/CD integration Connection string that we copied from Azure Security Center
- name = AZ_SUBSCRIPTION_TOKEN, value = The CI/CD integration Authentication token that we copied from Azure Security Center
- Change something in the code repository and push it. This will trigger the GitHub Action
- Go to the Actions menu and drill down into the Action. You'll see the results of the security scan
If the security scan found any vulnerabilities, these will show up as Azure Security Center recommendations when refreshed (Azure Security Center recommendations refresh every 24 hours). From there, you can apply remediations if they are available.
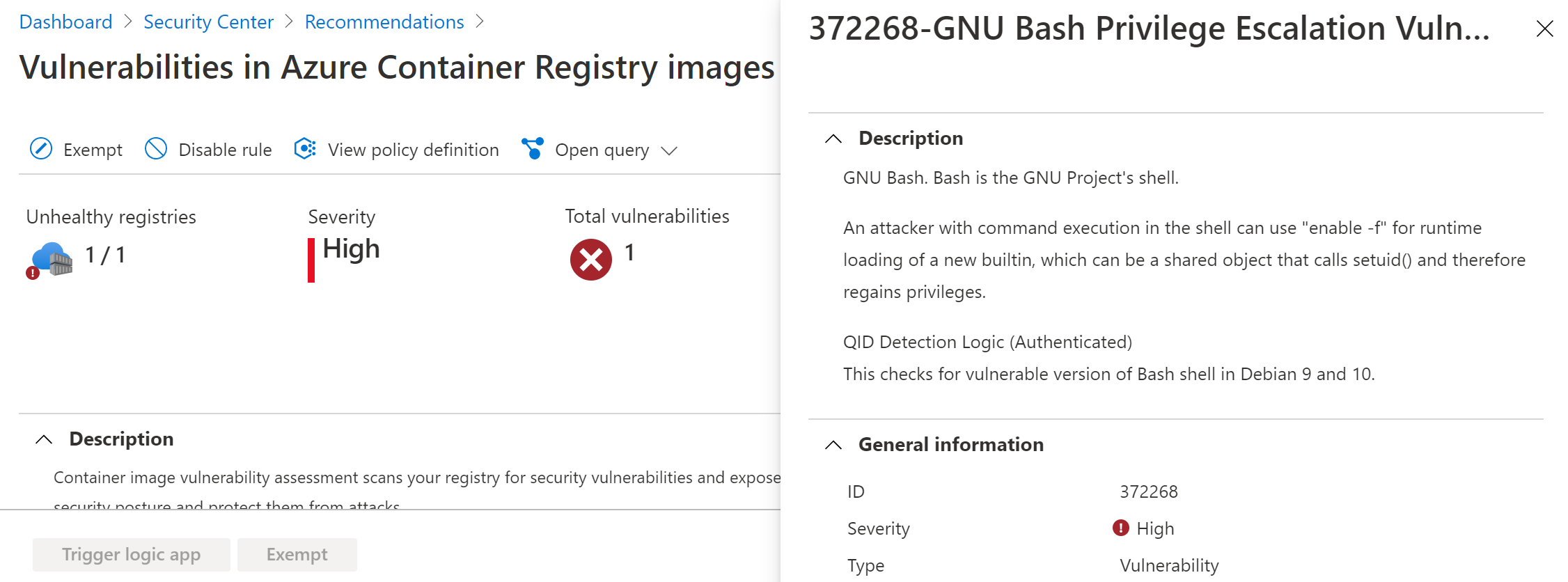
(Container security recommendations in Azure Security Center)
# Conclusion
Security needs to be part of every process of software development, including DevOps processes. Azure Security Center (opens new window) integrates with GitHub actions (opens new window) to scan containers for security vulnerabilities and report them as actionable recommendations. Go and check it out!
