Microsoft Security Academy

Welcome to the Microsoft Security Academy, your gateway to comprehensive cybersecurity training and resources.
| Table of Contents | |
|---|---|
| Modules | |
| Other Pages | |
April 25th, 2025 Update📰
Recent Update (April 25th): Events, Partner Programs, Back to basics series, almost all Modules, and Security Copilot
Phishers found a sneaky way to make emails look like they were sent to you by naming their account “me@.” Gmail’s UI/UX showed it as just “me” (easy to miss and fall for). Google originally said it wasn’t a bug, but after a lot of pushback, they’re fixing it. What’s the moral of the story? Don’t always trust how it looks and double-check those sender details🎣
Building with Model Context Protocol (MCP)? Start with John Savill’s breakdown, then check out our new guidance on how to keep your implementation secure and avoid OAuth misconfigs. Also new: an AI Red Teaming Agent for testing GenAI security, using PyRIT to simulate real attacks✅
MSSPs: Multi-workspace for multi-tenancy just hit public preview in our unified SecOps portal — if you’re juggling multiple customers and workspaces, this update is a game-changer (native support, less context-switching, more control).
Password spraying is back, and lax MFA is still the low-hanging fruit, according to recent research from Rapid7.
We almost lost the CVE disclosure system last week, and if you’re wondering why that’s important…
Click the image to open in a new tab
A seasonal reminder that M365 Maps should be your go-to for all things licensing 🔍
Big news for SMBs! E5 is now available as an add-on to Business Premium — read about the announcement here!🆕
Just last week, we announced Security Copilot agents that automate repetitive, noisy tasks like user-reported phishing alerts, conditional access policy gaps for new users and apps, and DLP/IRM alerts.
Think of these agents more like advanced workflows or simplified Logic Apps — automated, mostly trigger-based sequences for specific tasks + you can guide them with feedback/custom instructions in natural language. Most won’t take action for you, but they’ll help you prioritize (e.g., classifying phish alerts as true or false positive, one-click fixes for users outside existing MFA policies, …)
It’s been over a month since I updated this page, but I hope no one missed North Korea pulling off the largest crypto heist in history via a compromised dev’s laptop at Safe (a 3rd-party crypto storage Bybit uses); read the full breakdown here (another reminder “attackers don’t break in, they log in…”)
Some enthusiasts argue you need every tool below to maintain digital hygiene and protect your online life. One thing’s certain: Signal is widely popular across many types of users — but it’s not without risk according to recent Google threat intelligence.
.jpg)
There’s was a lot of buzz last month week about this research on the TTPs of an alleged NSA-led hack of a top Chinese university. Although some of it merits skepticism (since some of these tools leaked almost 9 years ago), it’s still an interesting read🕵️
Many of my partners live and breathe by ServiceNow for ticketing and tracking investigations, but did you know we recently launched case management in Defender? If not, read about it here! Now generally available
Most security vendors pitch Zero Trust and phishing-resistant MFA as the foundations, but are you not sure where to start? Grab a coffee and read through our new Zero Trust Deployment Essentials☕
Product names aren’t the only thing known to change at Microsoft, and certifications are no exception. Read about the retirement of the SC-400 and our new SC-401: Information Security Administrator Certification.
Remember how the U.S. State Department caught Chinese hackers snooping around Microsoft’s email systems? They used the now infamous “Big Yellow Taxi” KQL detections, which you can find here🚕
Other News
There’s a lot coming to Microsoft Sentinel, including multi-tenancy support for the unified SecOps platform, more Codeless Connectors, and SOC Optimization updates🔥
Log Analytics can be tricky, but our new Simple Mode makes it easier than ever before!
If you’re looking for an easier way to consume Microsoft Sentinel’s extensive GitHub repository, this is a helpful catalog.
We also recently launched a Zero Trust partner kit which includes pre-packaged and co-branded resources for you to use with customers. Just add your own branding!
The Microsoft Incident Response team recently created a compilation of incident response/TTP guides, best practices, and threat-hunting strategies, known as the Microsoft Incident Response Ninja Hub.
Events🎯
| Topic | Date | Register | |
|---|---|---|---|
| Microsoft Defender for Cloud | Microsoft Defender CSPM | APR 30 | Register |
| Microsoft Purview | What’s new in MIP? | MAY 06 | Register |
| Microsoft Purview | What’s new in DLP? | MAY 07 | Register |
| Microsoft Purview | Insider Threats: Are they real? | MAY 08 | Register |
| Microsoft Defender for Cloud | Secure Your Containers! | MAY 13 | Register |
| Microsoft Defender for Cloud | XDR Advanced Hunting | MAY 15 | Register |
| Microsoft Sentinel | Unified SOC: Mastering Multi-tenancy | MAY 20 | Register |
| Microsoft Defender XDR | MDO Configuration Best Practices | MAY 21 | Register |
| Microsoft Defender for Cloud | What’s new in Defender for Storage | MAY 22 | Register |
| Microsoft Defender for Cloud | Defender for SQL | MAY 27 | Register |
| Azure Network Security | Azure Firewall Management | MAY 28 | Register |
| Microsoft Sentinel | New Case Management Features | MAY 29 | Register |
| Azure Network Security | Azure DDoS Protection | JUN 05 | Register |
| Microsoft Purview | AI Network Level Integration | JUN 10 | Register |
| Microsoft Purview | New Model for E3/E5 Customers | JUN 11 | Register |
| Azure Network Security | Mastering Azure WAF Rulesets | JUN 26 | Register |
Start Your Journey
- M365 Maps For all things licensing
- Get started
- Basic cyber hygiene prevents 98% of attacks
- Microsoft’s Incident Response Guide
- Secure Cloud Business Applications (SCuBA) Project – CISA
Stay Connected🔗
Join our Security Connection Program where you can have influence in helping us shape our products together.
Stay connected with our Security Community, your peers, find guidance and resources, view technical and roadmap related questions, and more.
- Microsoft Sentinel Blog
- Microsoft Defender XDR Blog
- Microsoft Defender for Cloud Blog
- Microsoft Entra Blog
- Azure Network Security Blog
- Microsoft Defender for Endpoint Blog
- Microsoft Defender for IoT Blog
- Security, Compliance, and Identity Blog
Want to be a Ninja?
Microsoft Ninja trainings are sets of organized learning modules that guide you through the advanced features and functions of our products.
- Microsoft Security Copilot Ninja Training
- Microsoft Unified SOC Platform Ninja Training
- Microsoft Sentinel Ninja Training –
- Microsoft Sentinel Automation Ninja Training
- Microsoft Defender Threat Intelligence Ninja Training
- Microsoft Sentinel Notebooks Ninja Training
- Microsoft Defender XDR Ninja Training
- Microsoft Defender for Office 365 Ninja Training
- Microsoft Defender for Identity Ninja Training
- Microsoft Defender for Cloud Apps Ninja Training
- Microsoft Defender for Cloud Ninja Training Recently updated
- Microsoft Defender External Attack Surface Management Ninja Training
- Azure Network Security Ninja Training Recently updated
- Microsoft Defender for Endpoint Ninja Training
- Microsoft Defender for IoT Ninja Training
- Microsoft Purview eDiscovery Ninja Training Recently updated
- Microsoft Purview Information Protection Ninja Training
- Microsoft Purview Data Loss Prevention (DLP) Ninja Training
- Insider Risk Management Ninja Training
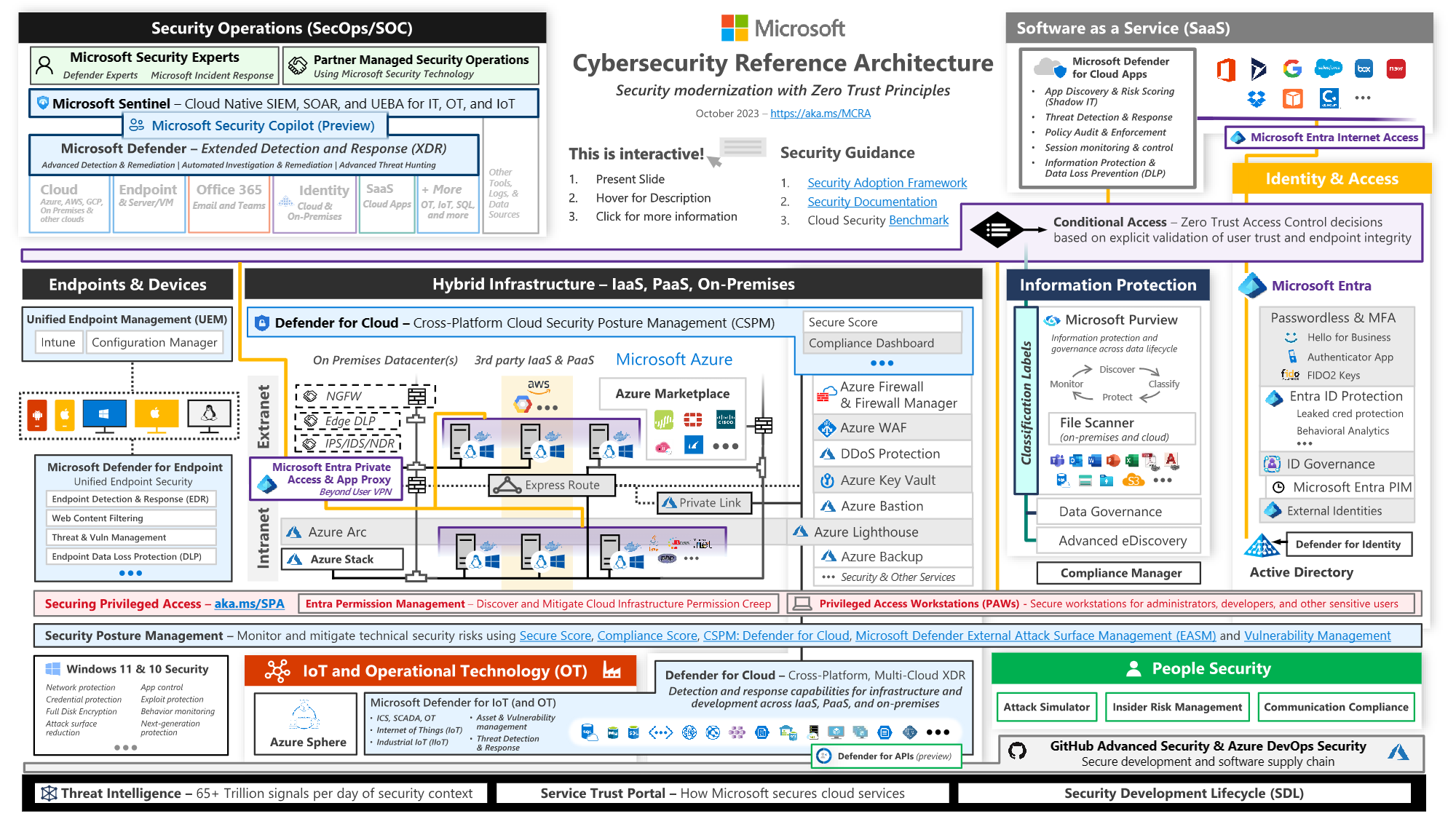
Microsoft Cybersecurity Reference Architecture (MCRA)🔒