Security Copilot Resources
What is the Security Copilot Technical Journey? 
The Microsoft Security Copilot Technical Journey will guide you through learning, extending, and driving customer adoption for Security Copilot, the first security platform to enable defenders to move at the speed and scale of AI by leveraging the most advanced large language models (LLMs) with large-scale data and threat intelligence, including more than 78 trillion daily security signals.
Table of Contents
This page is organized into three parts – Learn, Extend, and Driving Adoption.
| Table of Contents | |
| Learn Security Copilot | |
| Extend Security Copilot | |
| Driving Customer Adoption | |
April 25th, 2025 Update📰
| Recent Update (April 25th): Events and almost everything else |
We finally published official documentation on the Splunk plugin in Security Copilot📌
MSSPs, this one’s for you: Security Copilot support for Azure Lighthouse is now in public preview
If you’ve been waiting to use Security Copilot with your managed customers, good news: support is here (well, mostly). So, what’s the catch? As of today, MSSPs can only invoke Sentinel skills on their customer tenants via the Security Copilot standalone portal. In the future, this will expand to include other skills such as Entra, Intune, Purview, and the list goes on. What’s changed? Customers are no longer required to purchase the SCUs themselves.
To get started…
- An MSSP admin should provision SCUs (including the new Overage SCUs, which are $6 per SCU/hour and billed only on usage) and apply them to your Azure Lighthouse subscription
- Make sure you have access to your customer’s Sentinel workspace
Just two weeks ago, we announced Security Copilot agents that automate repetitive, noisy tasks like user-reported phishing alerts, conditional access policy gaps for new users and apps, and DLP/IRM alerts.
Think of these agents more like advanced workflows or simplified Logic Apps — automated, mostly trigger-based sequences for specific tasks + you can guide them with feedback/custom instructions in natural language. Most won’t take action for you, but they’ll help you prioritize (e.g., classifying phish alerts as true or false positive, one-click fixes for users outside existing MFA policies, …)
Who doesn’t want to make incident response in Sentinel faster and smarter? This new post walks through how you can use Security Copilot with Logic Apps and MDTI to automatically enrich incidents, cut down triage time, and get better insights.
Security Copilot egress IPs are now published to help you send requests and receive responses from your plugins!
Older news
You can learn how to access the Security Copilot audit log here or how you can ingest your Security Copilot audit logs using this Azure Function App and PowerShell script.
It’s also worth exploring this solution that automates the analysis of user-submitted phishing emails using Security Copilot🎣
Lastly, my colleague Rick created these easy-to-use KQL templates for custom Defender and Sentinel plugins. Give them a try!
Events
If you’re a member of the Microsoft Security Copilot Customer Connection Program (CCP), join our weekly Security Copilot Skilling and Readiness events:
| Topic | Date & Time | Register! |
| Conditional Access Optimization Agent in Entra | Thursday, May 1st @ 8:00 AM PT | Register |
| Splunk plugin for Security Copilot | Thursday, May 8th @ 8:00 AM PT | Register |
Learn Security Copilot
Are you ready to get started? Dive into onboarding guidance, prompt engineering templates and best practices, community resources, and other relevant documentation.
Overview
- What is Microsoft Security Copilot?
- Microsoft Security Copilot experiences
- Navigate Security Copilot
- Create effective prompts
- What is a compound AI system?
- Using Microsoft Graph as a Security Copilot plugin with Delegated Access
Onboarding
You can provision Security Copilot within the standalone experience or in Azure. If your organization requires tags to deploy Azure resources, use this ARM template to add tags during deployment. We recommend provisioning Security Copilot in the Azure Portal. Azure policies for resource tagging and location can cause deployment failures, and these errors don’t show in the Security Copilot standalone portal. When provisioning, you can purchase capacity in these four regions: East US, West Europe, UK South, and Australia East. Customers can scale from 1 to 100 SCUs per hour, and we now support Overage SCUs, which are billed only when used and can be set to unlimited or capped at a maximum amount.
While there are technically no prerequisites, you’ll need an Azure subscription and Microsoft Entra ID (Entra ID is required to authenticate your users). We also recommend allowing prompt evaluation anywhere with available GPU capacity for optimal results. By default, all users are Copilot contributors (this may vary according to existing user permissions) and the provisioning user is the Copilot owner. Contributors cannot update data sharing options, manage SCUs, view the usage dashboard, and may only manage and publish custom plugins or upload files when permitted. Also, by default, all users with the Entra Global Admin or Security Admin roles will automatically be assigned the Copilot Owner role.
Security Copilot will not elevate your level of access (e.g., to use the Microsoft Sentinel plugin, you will need the Microsoft Sentinel Reader role). However, plugin settings are managed at the user level, requiring each user to enable/disable plugins and configure authentication methods. Unfortunately, there is no existing option to set plugin configurations at the Tenant level.
We recommend starting with a “crawl, walk, run” model. Crawling starts with the embedded experiences. It’s tool-specific, requires no prompt engineering, and doesn’t support third-party or custom plugins — making it easy to use, more accurate, and cost-efficient. Walking starts with the standalone portal. Users can submit their own prompts and access a broader range of skills, including third-party and custom plugins. This offers more flexibility but requires effective prompt engineering. Running uses Logic Apps or agents to integrate Copilot into automated workflows. This method is highly extensible and can significantly reduce SCU usage by pre-processing data or optimizing prompts.
It’s also important to monitor SCU usage to manage costs and avoid disruptions (e.g., calculate your average SCU utilization over a standard 7 days). Learn more about how to monitor your usage here.
Lastly, experiment with promptbooks (learn how to create your own Promptbooks here) and uploading your organization’s own DOCX, MD, PDF, and TXT files. You can upload files up to 20 MB in total. Security Copilot reasons over files to generate more relevant and specific responses. Learn more about uploading your own files here.
To get the most out of Security Copilot, it’s also helpful to understand its terminology. A session is created for each interaction between a user and Security Copilot. A prompt is a question or instruction submitted by the user. A skill is a specific function Copilot uses to gather data and respond. A plugin is a group of related skills tied to a specific resource, like Sentinel or Entra. Lastly, the orchestrator maps prompts to the right plugin skills behind the scenes.
Get Started
- Get started
- Understand authentication
- Best practices for Microsoft Entra roles
- Prompting
- Promptbooks
- NEW: Prompt Engineering Techniques: A comprehensive repository
- OpenAI Prompt Engineering
- Apply principles of Zero Trust to Microsoft Security Copilot
- Exploring Security Copilot to automate incident triage
Optional resources for after your first few months
Useful for analysts
- Next-Gen device incident investigation and threat hunting with custom plugins
- Accelerating anomalous sign-in detection with Security Copilot + Entra ID
- Monitoring user activities and system events with Security Copilot + Sentinel
- NEW: Proactively identify and prioritize CVEs
Useful for customization
- Leveraging ASIM-based KQL plugins in Security Copilot
- Custom Identity Analyst plugin
- Custom Data Security plugin
Useful for extension
Use Cases
Security Copilot standalone portal
- Triage incidents with threat intelligence
- Investigate an incident’s malicious script
- Overall incident response and remediation
Microsoft Defender XDR
- Summarize an incident
- Script analysis
- File analysis
- Device summaries
- Identity summaries
- Triage and investigation
- Generate KQL queries
- Create incident reports
Entra
Microsoft Defender for Cloud
- Analyze recommendation
- Summarize recommendations
- Remediate recommendations
- Delegate recommendations
- Remediate code
Threat Intelligence
Also check out our Security Copilot Technical Workshops🔨
Videos
We recommend watching the following videos created by Microsoft Security and the Global Partner Solutions (GPS) Technical Team:
 |
Microsoft Security Copilot John Savill dives into the powerful features and capabilities of Microsoft Security Copilot. |
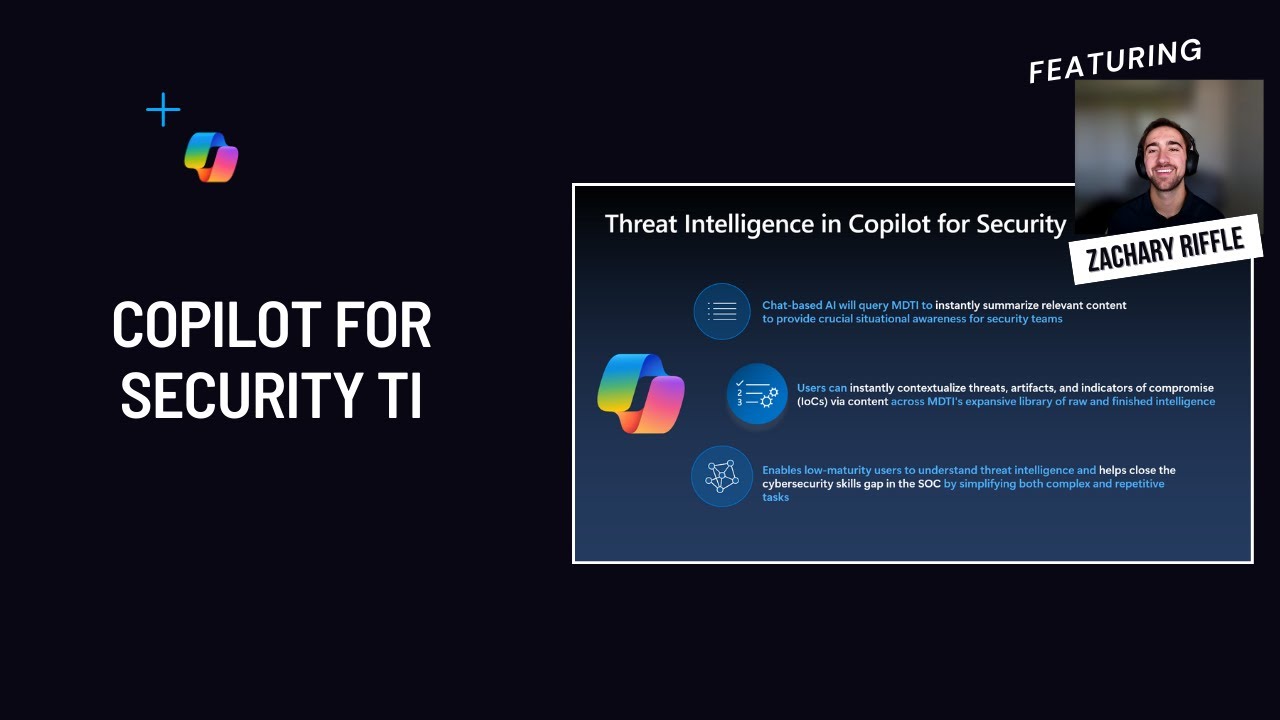 |
Threat Intelligence in Security Copilot with Volt/Silk Typhoon demo Learn about Microsoft Threat Intelligence in Security Copilot, including what it is, how you can use it, and learn from a comprehensive demo featuring Volt/Silk Typhoon, prolific state-sponsored espionage actors from China. |
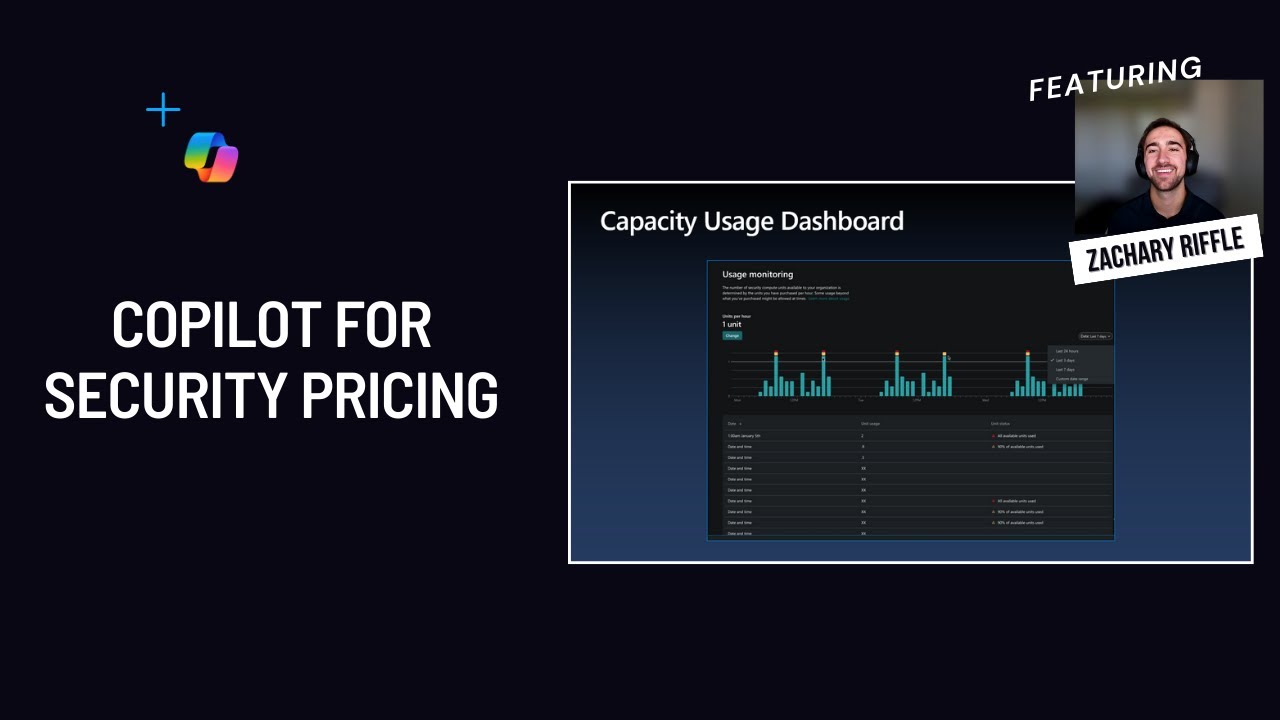 |
Security Copilot Pricing Short on time? Learn about Security Copilot’s pricing model in just 10 minutes, including how to provision, scale, and manage Security Compute Units (SCUs). Discover what you can do today, along with valuable onboarding tips. |
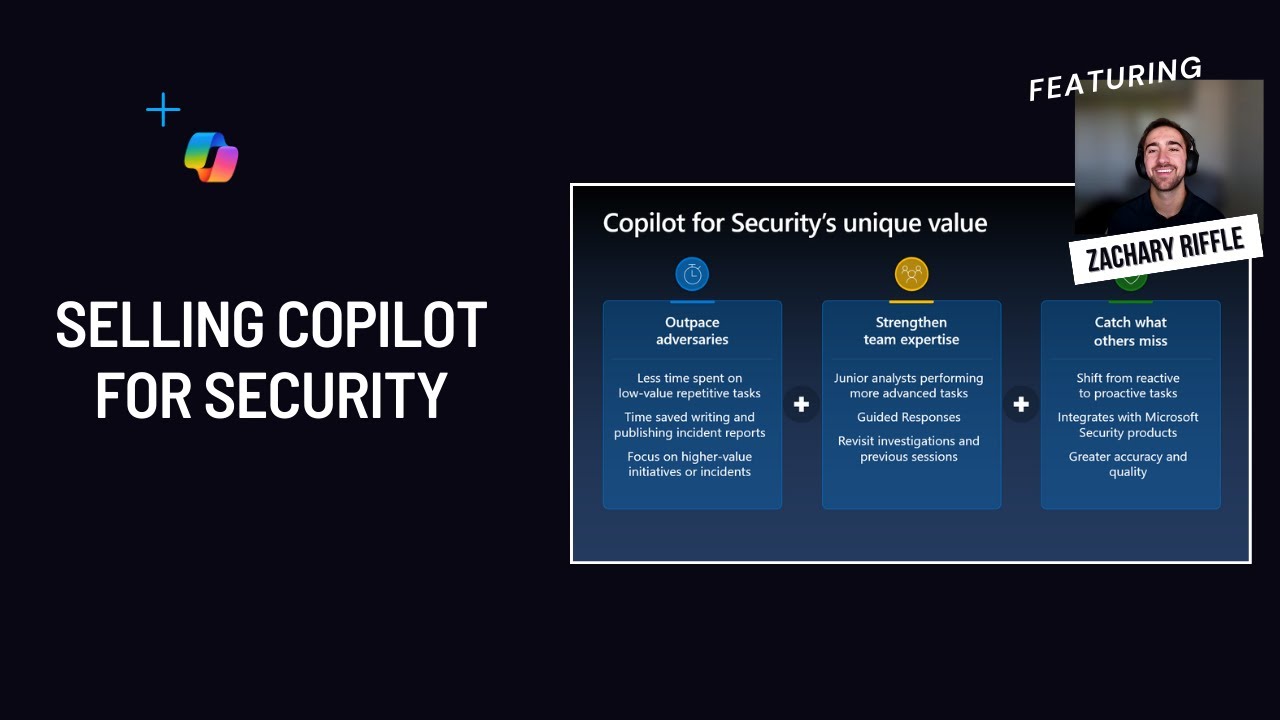 |
Selling Security Copilot w/ Multi-stage Incident Demo Explore Security Copilot’s powerful use cases, its unique value, proven results, and differentiation story, and see it all in action with a comprehensive multi-stage incident demo in Microsoft Defender XDR. |
 |
Security Copilot Responsible AI Learn how Security Copilot mitigates Responsible AI issues and explore Generative AI threats, including prompt injection attacks, disinformation campaigns, spear phishing, etc., and how we at Microsoft defeat them. |
Also explore our Security Copilot YouTube Playlist📹
Roles beyond SOC Analysts
- IT Admins: Create device configuration profiles in Intune and leverage data-driven configuration troubleshooting and remediation.
- DLP Analysts: Summarize DLP alerts and analyze DLP policy configurations.
- Insider Risk Analysts: Summarize Insider Risk Management (IRM) alerts and gain context around users with risky behavior.
- eDiscovery Analysts: Generate Keyword Query Language from NL in eDiscovery and summarize evidence collected.
- Identity Access Management (IAM) Admins: Discover high risk users, overprivileged access, and users out of compliance (e.g., MFA).
- CISOs: Receive executive summaries and detailed reporting.
Announcements & Whitepapers
- Nov. 2024: Generative AI and SOC Productivity: Evidence from Live Operations
- Oct. 2024: Randomized Controlled Trials for Security Copilot for IT Admins
Community Resources
- Join the Security Copilot Customer Connection Program (CCP)
- Microsoft Security Copilot Tech Community Blog
- Applied Generative AI (GAI) in Security Blog
- Why AI Will Save the World
AI Security
- Learn more about our approach to Responsible AI
- MITRE ATLAS (Adversarial Threat Landscape for Artificial-Intelligence Systems)
- OWASP AI Security and Privacy Guide
Back to Table of Contents. Are you ready to extend Security Copilot?
Extend Security Copilot
Learn how to grant an MSSP access and how to use and create plugins. Security Copilot plugins extend the platform’s capabilities by acting as connectors, enabling seamless integration with infinite partners and third parties to support custom functionality.
MSSPs
Plugins
As of today, custom plugins in Security Copilot work by executing 1. a KQL query, 2. a GPT query, or 3. making an API call (either GET or POST), and the data returned depends on the type of call and the associated API permissions.
- Overview
- Other plugins – Non-Microsoft plugins
- API
- GPT
- KQL
- Manage plugins
- Create custom plugins
- Plugin error codes
Connectors
3P Plugins
- AbuseIPDB – AbuseIPDB is a central repository to report and identify IPs that are associated with malicious activity online
- Aviatrix – Aviatrix provides insights into cloud networking and firewall policy enforcement
- CheckPhish – CheckPhish AI analyzes URLs for phishing threats, tech support scams, cryptojacking, and other risks
- Computer Incident Response Center Luxembourg (CIRCL) – CIRCL is a government initiative to validate suspicious files in the form of hashes
- CrowdSec – CrowdSec provides identification and verification of potentially malicious IPs
- CyberArk – CyberArk Privilege Cloud helps to securely store, rotate, and isolate credentials
- Cybersixgill – Cybersixgill offers real-time TI solutions, including from the dark web
- Cyware Intel Exchange – Cyware Intel is a TI Platform for ingestion, enrichment, analysis, prioritization, actioning, and sharing of threat data
- Cyware Respond – Cyware Respond is an end-to-end incident management and response platform
- Darktrace – Darktrace offers cybersecurity AI services
- Forescout Risk and Exposure Management – Forescout REM provides a view of device risks and vulnerabilities
- Forescout Vedere Labs – Forescout research teams provide a TI feed containing IP, URL, and File hash indicators for potentially malicious activity
- GreyNoise – GreyNoise collects and analyzes Internet-wide scan and attack data
- Intel 471 – Intel 471 provides cybercrime intelligence
- IPGeolocation – IPGeolocation provides geolocation data, time zone details, security insights (VPN, proxy, bot detection), etc.
- IPinfo – IPinfo provides IP geolocation, IP to Privacy Detection (VPN, Tor, Proxy), ASN data, company data, carrier metadata, and WHOIS data
- Jamf – Jamf Pro provides enterprise-level Mobile Device Management (MDM)
- Netskope – Netskope combines security and networking services, enabling Secure Access Services Edge (SASE) and Zero Trust
- Pure Signal Scout – Pure Signal Scout is Team Cymru’s TI tool
- Quest Security Guardian – Quest Security Guardian is an Active Directory tool that reduces your attack surface
- Red Canary – Red Canary provides managed detection and response (MDR) services
- ReversingLabs – ReversingLabs helps SOC teams understand file-based threats
- Saviynt – Saviynt provides insights into identity-related risks
- SGNL – SGNL provides Zero Standing Privilege (ZSP) initiatives to protect user sessions and credentials
- Shodan – Shodan is a search engine that allows users to find specific types of devices connected to the Internet
- Silverfort – Silverfort provides advanced CEF data from Microsoft Sentinel
- NEW: Splunk! – Splunk is a widely used SIEM, SOAR, and threat intelligence platform
- Tanium – Tanium is a Converged Endpoint Management (XEM) reference platform
- TufinMate – Tufin Orchestration Suite is a firewall management platform
- UrlScan – UrlScan allows users to scan and analyze potentially malicious URLs
- Valence Security – Valence combines SaaS Security Posture Management (SSPM) and advanced remediation
- Whoisfreaks – Whoisfreaks provides domain and IP intelligence services
Extensibility Features
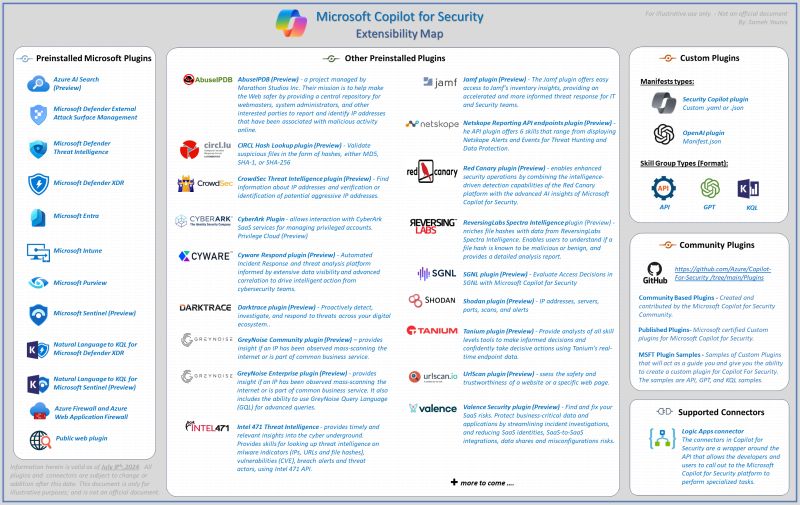
Relevant Community Plugins
Disclaimer: Some of these plugins were developed and are maintained by the community and are not owned and/or managed by Microsoft.
- Security Copilot Login Activities
- Microsoft Sentinel custom plugin scenarios
- Microsoft Defender XDR custom plugin scenarios
- QR Code AiTM Phishing Detection
- Redact Personally Identifiable Information (PII) – this plugin will redact PII content from a session or a prompt output
- Have I Been Pwned – Have I Been Pwned allows users to verify whether their personal data has been compromised by data breaches
- NEW: Sentinel MCP Server – Python-based MCP server using FastMCP library to bridge dev environments and Security Copilot
Back to Table of Contents. Are you ready to drive customer adoption?
Driving Customer Adoption
Microsoft Security Copilot enables customers and partners to defend against threats, streamline security workflows, and protect critical assets. Learn how to drive customer adoption below.
Pricing📌
Security Copilot pricing is consumption-based and costs approximately $4 per SCU per hr. A Security Compute Unit (SCU) is Security Copilot’s unit of measurement of computing capacity to run a Copilot workload (i.e., prompt/promptbook). The amount of SCUs needed depends on the complexity of the prompt, promptbook, Logic App, or agent. The pricing is consistent across the standalone experience and the embedded experiences as well as regions.
What’s new? Customers can also use Overage SCUs, which are $6 per SCU/hour and billed only on usage. These provide flexibility to handle occasional demand spikes without needing to provision fixed capacity in advance, and they can be set to unlimited or capped at a maximum amount.
To use Security Copilot, you will need to provision at least 1 SCU per hr 24x7. Therefore, the minimum annual price is $35,040 USD ($4 * 24hr per day * 365day per yr). Your monthly bill is calculated as (SCUs per hr) x $4 x 730/month or you can leverage the Azure Pricing Calculator. Customers and partners can purchase SCUs in the standalone portal or in Azure and can manually provision SCUs up or down so long as there is at least 1 SCU/hr. Once an analyst is nearing the capacity limit (90%), they will receive a warning and the option to increase the capacity.
If you delete Security Copilot (zero SCUs per hr), we will retain your data for 90 days. Tenant-level MDTI workbench is included with Security Copilot and although it’s not the standalone API, the TI information is easy to read and in the context of your investigations (e.g., activity groups, tooling, and vulnerabilities). From a licensing perspective, this is also significant cost savings.
Since computing capacity and token usage is variable (quantifying a consistent # of tokens or SCUs needed per prompt, promptbook, Logic App, or agent is difficult), it’s important for partners to know what they can do now:
- Calculate your average SCU utilization over a standard 7 days
- Provision ≈1 SCU per embedded experience, ≈4 SCU per standalone experience, and ≈5 SCU per automation and/or promptbooks
- Measure SCU usage between different use cases (SOC analysts, Purview admins, Identity/access admins, etc.)
- Measure SCU usage between different levels of expertise (Junior analysts vs Senior analysts)
- Measure SCU usage across different types of investigations (incident triage, threat actor investigation, reverse engineering a malicious script, etc.)
- Explore the Security Copilot SCU Optimizer Solution to simplify cost management
Integrations
- Azure AI Search
- Azure Firewall
- Azure Web Application Firewall
- Microsoft Sentinel
- Copilot in Defender XDR
- Copilot in Entra
- Copilot in Intune
- Copilot in Defender EASM
- Copilot in Surface Management
- Copilot in Threat Intelligence
- Copilot in Purview
- Copilot in Defender for Cloud (Preview)
Microsoft Security Integration Reference Architecture
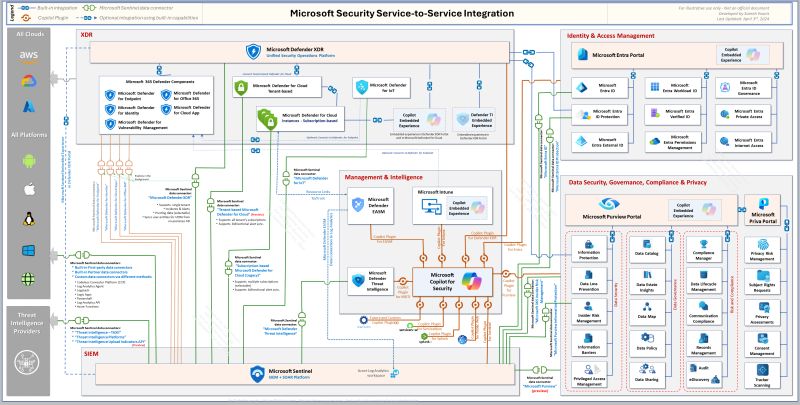
Multi-tenant & Delegation Models
As of today, MSSPs can only invoke Sentinel skills on their customer tenants via the Security Copilot standalone portal. Support for other skills like Entra, Intune, and Purview is coming soon. What’s changed? Customers are no longer required to purchase the SCUs themselves.
To get started, an MSSP admin should 1. provision SCUs (including the new Overage SCUs, which are $6 per SCU/hour and billed only on usage) and 2. apply them to their Azure Lighthouse subscription. Then, 3. make sure you have access to your customer’s Sentinel workspace.
Address Concerns
- OAuth 2.0 On-Behalf-Of flow
- Privileged Identity Management (PIM)
- Microsoft Defender for Endpoint (MDE) Device Groups
Technical Considerations
- Assist a Human in Completing Work – It’s a Copilot, integrations are driven by/drive human engagement, not background runtime processing of large amounts of data.
- Have High Customer Value — The cost of Generative AI is orders of magnitude higher per transaction than your average feature today and depends on a constrained hardware supply (GPUs).
- Will be Regularly Used — The best integrations will be used regularly so it is ongoing value, not a one-time value (like a configuration assistant).