This site has been deprecated and no longer being maintained. The repo will be
deleted on December 1, 2025. YouTube content will be updated here: https://www.youtube.com/@theacademyhub and an archive of the repo will be available here:
https://github.com/bhitney/PartnerResources
Microsoft Defender XDR
Explore Microsoft Defender XDR videos with demos delivered directly to partners, relevant certifications, and further resources.
Stay connected with the Microsoft Defender XDR Blog.🔗
 |
NEW: Securing AI Applications: Real-World Threats, Protection w/ Microsoft Defender for Cloud Apps, & Q&A🆕 Discover how Microsoft Defender for Cloud Apps protects AI apps like DeepSeek through real-world scenarios, followed by a Q&A with the product team. |
 |
Learn About Insider Risk Management Data in Microsoft Defender XDR Microsoft Purview Insider Risk Management data is now available in Microsoft Defender XDR, allowing access to IRM alerts, indicators, and events via Graph API, advanced hunting with KQL, custom detections, and more. |
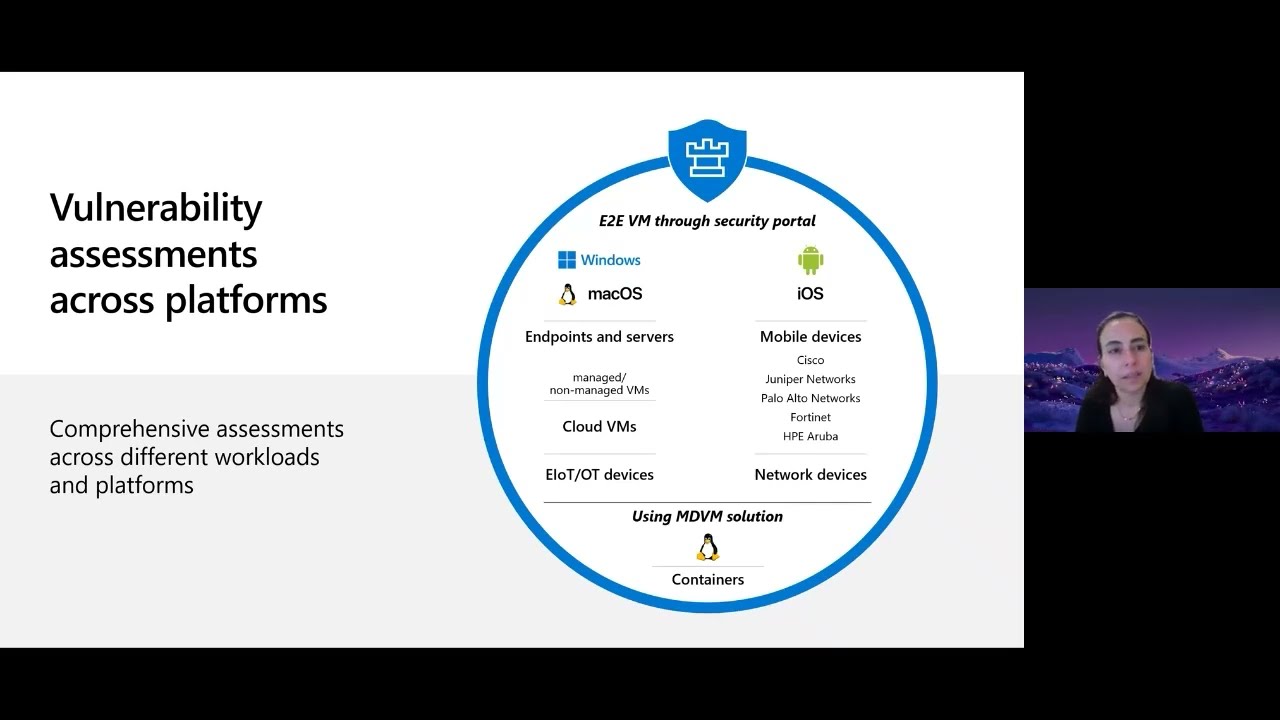 |
Get the Most Out of Microsoft Defender for Vulnerability Management (MDVM) Join the MDVM engineering team and learn about its capabilities, use cases, and best practices for developing and implementing posture and risk management. |
 |
Improved SecOps Efficiency with New Detections, Advanced Hunting, and Response Flows Explore how to use the SecOps guide for MDO to streamline incident response, reduce false positives, and strengthen your email security! |
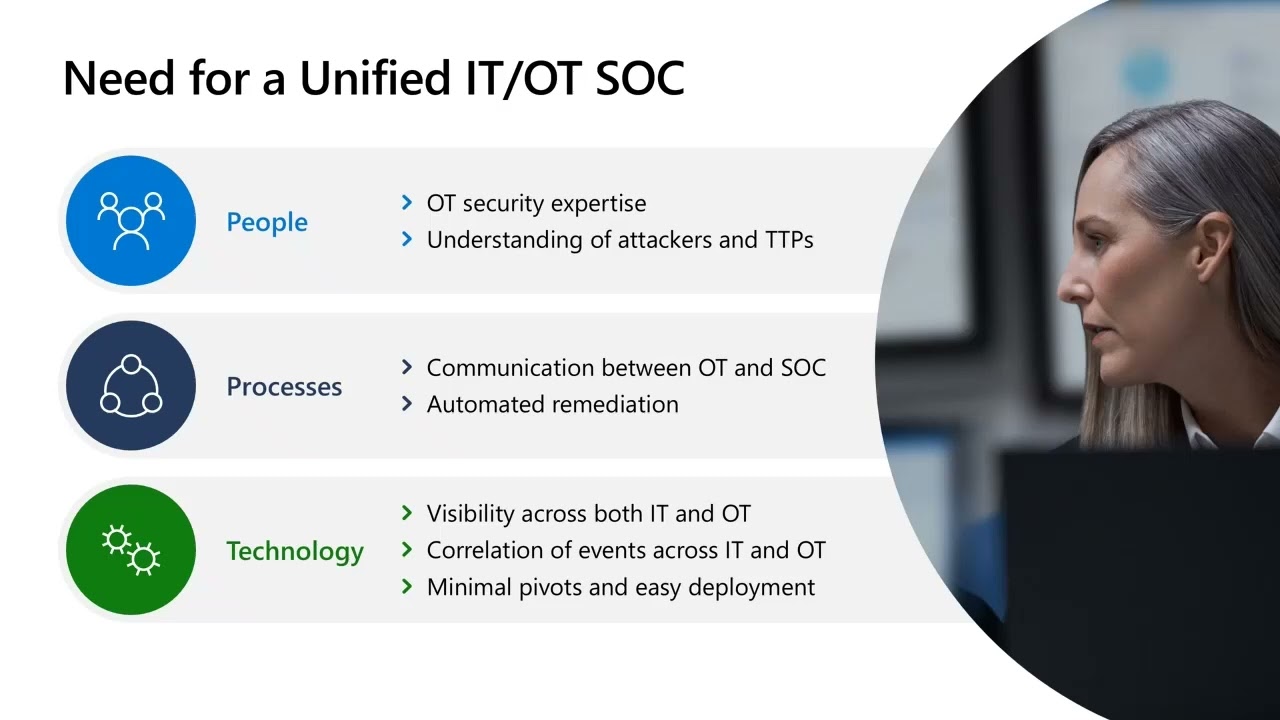 |
New Ways for Security Teams to Protect OT Environments with Microsoft Defender XDR Learn how digital transformation has created new security challenges, particularly in industrial processes and critical infrastructure, as well as how Microsoft Defender XDR is changing the way we safeguard critical assets. |
 |
ITDR Introduction and Prevention Capabilities Learn about Microsoft's vision for ITDR and its importance in today's threat landscape. We'll cover the prevention pillar, focusing on adaptive controls and security posture as the critical foundation. |
 |
ITDR Detection Learn how Microsoft can protect your identity environments with holistic detection capabilities for advanced identity attacks, whether on-prem, hybrid, or in the cloud. |
 |
ITDR Investigation and Hunting SOCs need deep visibility into identities, context, and telemetry that are crucial for investigations, allowing Security Analysts to efficiently triage incidents and understand the scope of any compromise. |
 |
ITDR Response Successfully responding to identity-based attacks with native response actions embedded into the SOC workflow is a crucial part of mitigating attacks. Learn how to use these native response capabilities to stop attackers and remediate issues. |