Task 3.5: Add automation to the Windows Security event log clear incident
In this task, you’ll configure the Windows data connector to be linked to the modified Logic app. Automation rules streamline the use of automation in Microsoft Sentinel, enabling you to simplify complex workflows for your threat response orchestration processes.
The following document may help you complete this task.
- Automate threat response in Microsoft Sentinel with automation rules
- Create and use Microsoft Sentinel automation rules to manage response
-
In the upper left, select the hamburger icon
 , then select Home to return to the Microsoft Azure home page.
, then select Home to return to the Microsoft Azure home page. -
On the Microsoft Azure Home page, under Azure services, select Microsoft Sentinel.

-
On the Microsoft Sentinel page, select LogAnalytics-workspace.
-
On the left navigation, under Configuration select Analytics.
-
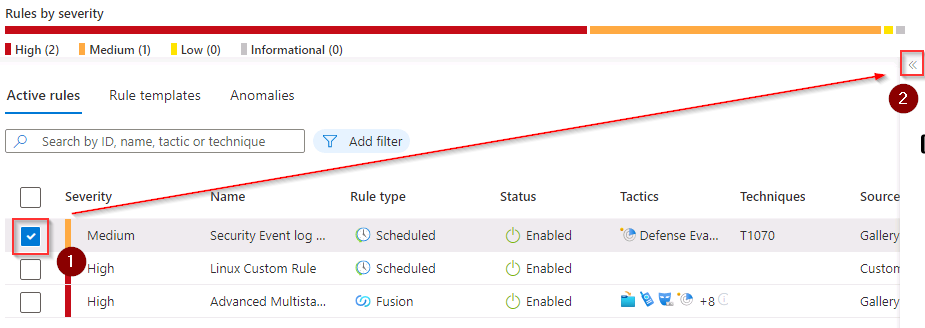
From the list of Active rules, select the Medium severity rule named NRT Security Event log cleared.
If necessary, open the Active rules details panel on the right by selecting the « icon.
-
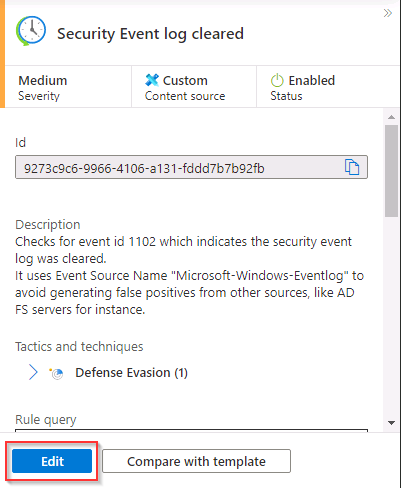
On the Security Event log cleared details panel, select Edit.
-
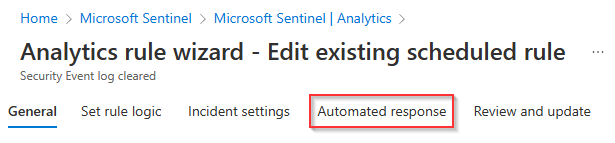
On the Analytics rule wizard - Edit existing scheduled rule page, on the General tab, review the fields and select the Automated response tab.
-
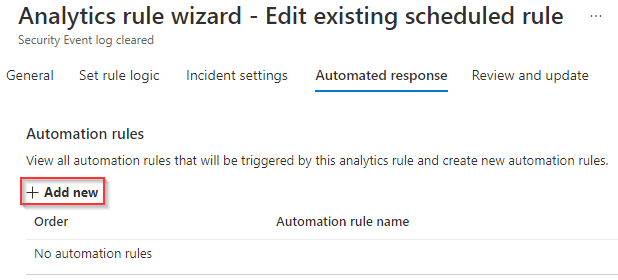
On the Automated response tab select + Add new.
-
In the Create new automation rule panel, set the Automation rule name to WinWatchlist.
-
Set the first value in Actions to Run playbook.
-
In the second value in Actions, select the Add-HostToWatchlist-IncidentTrigger playbook.

-
Review the rest of the fields and select Apply.
-
On the Automated response tab, select Next : Review + create >.
-
Once the Validation process has completed successfully select Save.