Task 2.2: Enable migrated Splunk rules in Sentinel
Now that the Splunk data rules have been imported, converted and verified in Microsoft Sentinel, we’ll need to enable the rules so that Sentinel can take over the detection of incidents in your environment.
The following document may help you complete this task.
-
Return to the Microsoft Sentinel - Analytics panel.
-
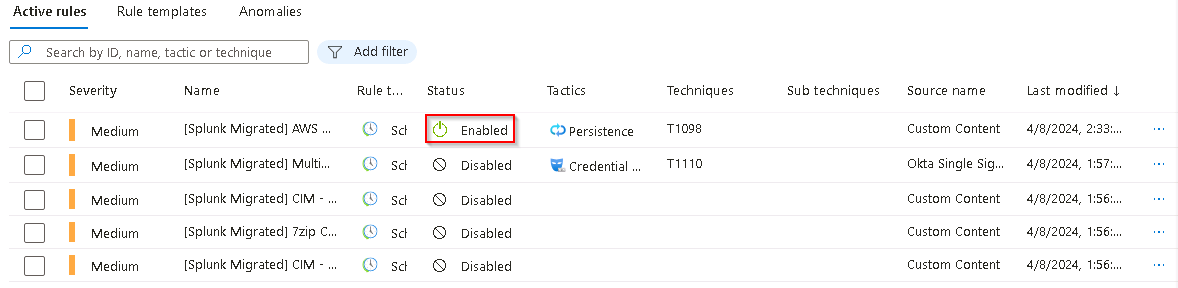
Select the [Splunk Migrated] Multiple Okta Users With Invalid Credentials From The Same IP entry in the list to display the details in the [Splunk Migrated] Multiple Okta Users With Invalid Credentials From The Same IP pane.
If the right panel is not displayed select the « icon on the right side to display it.
-
On the [Splunk Migrated] Multiple Okta Users With Invalid Credentials From The Same IP pane, select Edit.
-
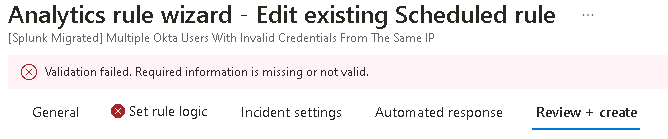
Change Status from Disabled to Enabled and then select the Review + create tab.

If there’s an error in the query it will fail the validation and can’t be enabled.
-
Return to the Microsoft Sentinel - Analytics panel and select the [Splunk Migrated] AWS CreateAccessKey entry in the list to display the details in the [Splunk Migrated] AWS CreateAccessKey pane.
-
On the right panel select Edit to edit the selected analytics rule.
-
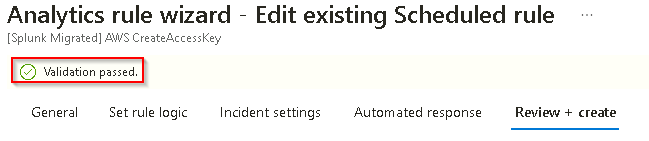
Change the Status from Disabled to Enabled and then select the Review + create tab.
This rule does not contain any issues in the Query and will pass validation
-
Once the Analytics rule has been validated select Save to commit the update of the Analytics rule and then return to the Microsoft Sentinel - Analytics pane.
The Status of the updated Analytics rule in the list should now be updated to Enabled. If it hasn’t been updated select the Refresh link in the top menu to update the list.