TIP
💡 Learn more : Azure Network Security Groups (opens new window)
This post was brought to you by Kumar Allamraju (opens new window).
# Reusing Network Service Groups across Virtual Machines
Have you ever wondered that your NSG blade was cluttered with too many Network Security Groups? See my NSG blade.
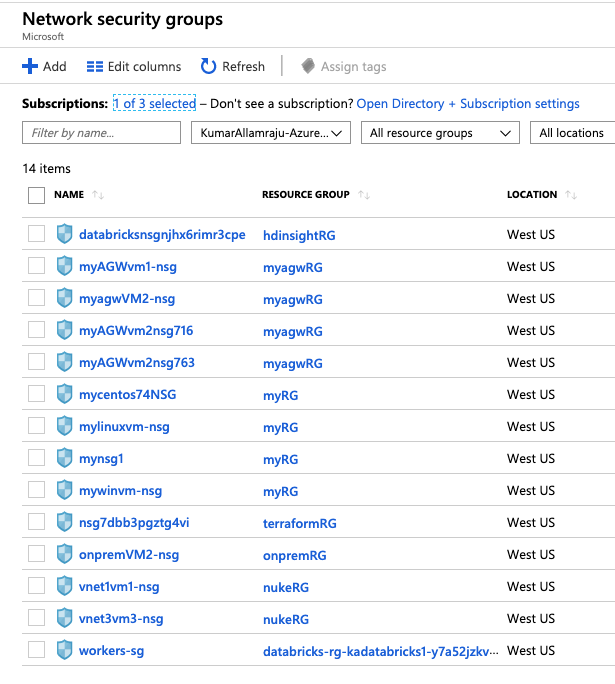
Shocking huh? This list was even bigger in my customer's environment. When you create a new Virtual Machine from Azure Portal or CLI, a new network security group is created for each VM. This is by design. However there's a way to specify an existing NSG assuming you want to apply the same inbound and outbound rules for a group of virtual machines.
This can be done by choosing the Advanced option in the Networking tab. The default option is "None".
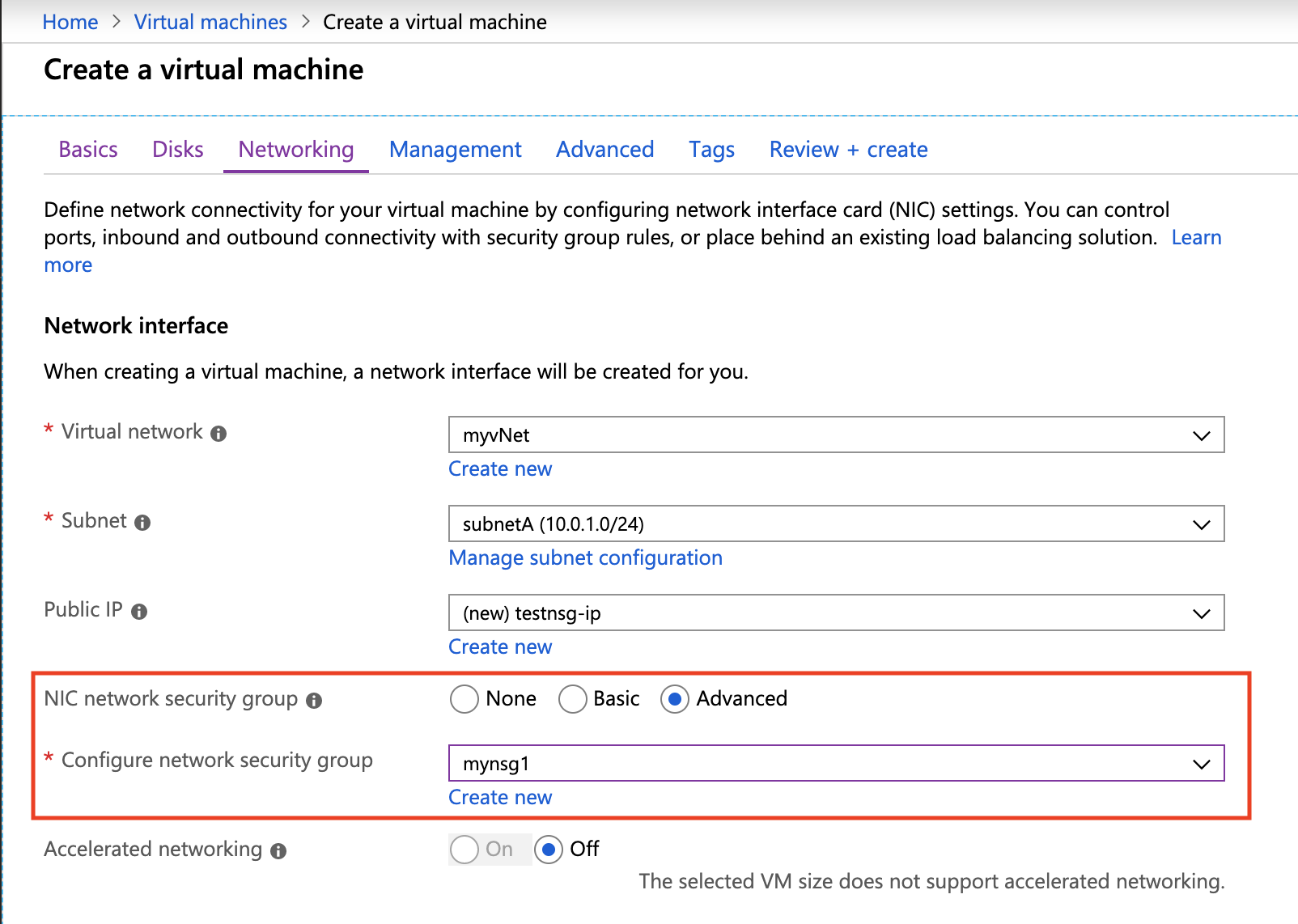
When you select Advanced option, you will have an option to select the existing NSGs. I have created a network security group called "mynsg1" with a set of inbound and outbound rules prior to creating a VM. See the screenshot below.
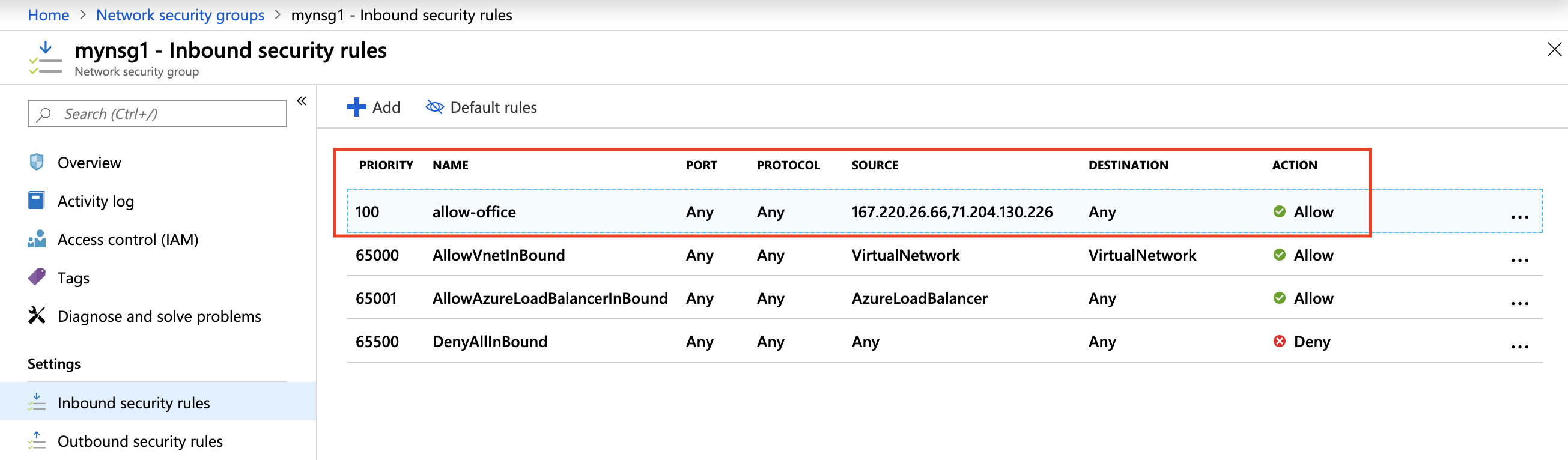
In this case, I'm allowing access to my VMs only from my Home and Office IPs. You can further fine tune the NGSG by the protocol and specific ports and re-use the same NSG.
When you create a VM using az CLI, you have an option to specify the NSG. See below.
The following example creates a simple Ubuntu Linux VM with a public IP address, DNS entry, wih an existing NSG, two data disks (10GB and 20GB), and then generates ssh key pairs.
az vm create -n MyVm -g MyResourceGroup --nsg mynsg1 --public-ip-address-dns-name MyUniqueDnsName --image ubuntults --data-disk-sizes-gb 10 20 --size Standard_DS2_v2 \
--generate-ssh-keys
2
Now if you want to apply this NSG to all your VMs that shares the same set of allow/deny rules, you can stop the VM, go to the vNet blade attached to your VM, click on the device under Connected Devices, under Network Security Group blade click on Edit icon and select the new NSG that was created above and restart your VM(s). The same rule applies to existing VMs as well.
# Conclusion
Network Security Groups is an important feature in Azure Virtual Networking that allows you to filter traffic to and from Internet and across Azure resources. The intent of this article is to share a quick Azure tip but NSG shouldn't be used as a first line of defense to your Azure resources.
